| layout | comments | title | excerpt | tags | toc | img_excerpt | ||
|---|---|---|---|---|---|---|---|---|
post |
true |
Elasticsearch use cases in cybersecurity |
Learn about the difference use cases for Elasticsearch in a cybersecurity context |
|
true |
-
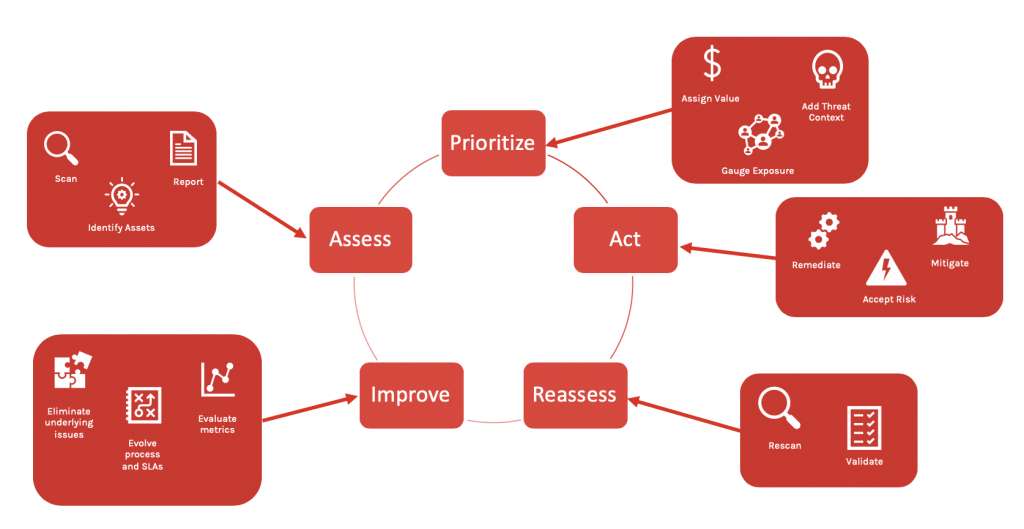
Data centralization: Elasticsearch provides a centralized repository for storing vulnerability data from disparate sources like threat intelligence feeds, asset inventory lists, application and system audits, and penetration testing reports. By consolidating this data, security operations teams can obtain an overarching view of their organization's vulnerabilities and prioritize remediation efforts accordingly.
-
Automatic parsing: As soon as new vulnerabilities are discovered or updated, they must go through manual triage, which requires extensive human effort and often leads to delays. Elasticsearch can automatically parse vulnerability data streams from various sources (e.g., CVE, NVD, OSVDB, MITRE ATT&CK) to extract necessary contextual attributes. Then, it assigns scores or severity ratings based on predefined rules tailored to each organization's unique environment.
-
Enhanced visibility: Elasticsearch indexes vulnerability records, allowing users to perform full-text queries, faceted navigation, and sorting. This capability provides enhanced visibility into the types, origins, and impact levels of the identified vulnerabilities, empowering administrators to focus attention on problem areas more precisely.
-
Adaptive workflow orchestration: Integration with Elasticsearch enables orchestration tools like open-source OSBase, Demisto, and Phantom Cyber to dynamically adjust their workstreams based on the current state of known vulnerabilities. This adaptive approach ensures that security practitioners always tackle high-priority weaknesses first while minimizing resource wastage on already-resolved issues.
-
Personalized notifications: Leveraging machine learning algorithms, Elasticsearch can assist in generating personalized notification strategies b
I hope you enjoyed this article, feel free to leave a comment or reach out on twitter @bachiirc.