-
Notifications
You must be signed in to change notification settings - Fork 7
EN_9_Fine grained_SNAT
Contributor: Jesonchen
At present, more and more Internet businesses provide external services in the form of APIs, and at the same time, they also put forward more requirements for API security construction. Therefore, API services for To B services often use a simple and efficient method of restricting the source IP to improve security. In the past, when enterprises called these services, they needed to use the specified public network IP as the source address. When the enterprise's own services were containerized, this model would not change. On the contrary, due to the highly dynamic nature of containers, the Pod IP changed frequently for network management. The designated public network IP mapping brings greater challenges, mainly reflected in the following two points:
- When the source address changes dynamically, it is necessary to identify and maintain the source address list
- Different outgoing IPs need to be matched according to different services to achieve refined management and control
When the container needs outbound access, it is difficult to perform access control according to the traditional source address method, and a more dynamic access control policy is required, which can be changed according to the change of the source address. This article mainly introduces the application of CES in the outbound access of container services and the need to specify the source IP.
F5 SNAT (Secure Network Address Translation) is a necessary technical means in load balancing. A common scenario is to convert the incoming client source address into F5's internal interface IP or designated network segment to simplify server return packet routing settings. As shown below:
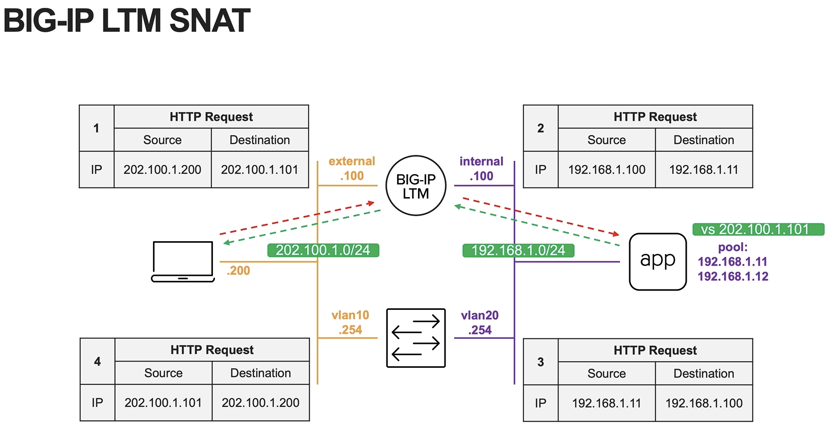
The same logic is used for outbound access. After the client source address passes through F5, it will be converted to the internal interface IP or designated IP of F5. With F5 iRules, you can set custom SNAT rules, such as using specific SNAT IPs with specific source and destination addresses.
But this only applies when the source address is known statically. If the source address is dynamic, iRules cannot automatically identify and maintain the source address and then match the SNAT rule.
Now, we can use CES's ability to discover Pods, dynamically identify and maintain Pod source addresses, and match SNAT rules, so as to achieve outbound access to the specified public IP, as shown in the following figure:
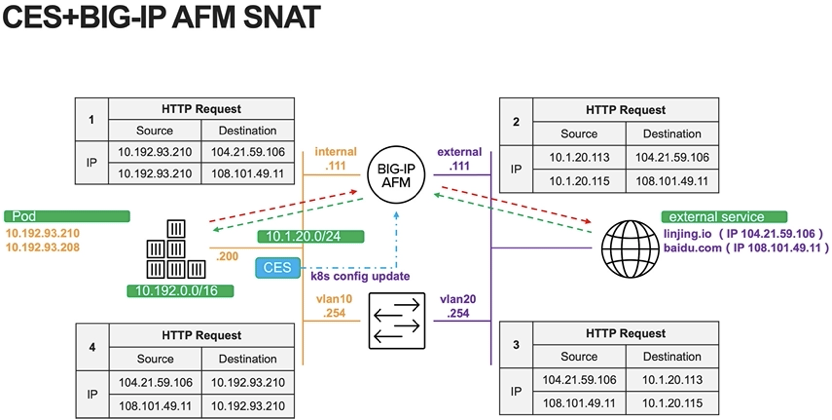
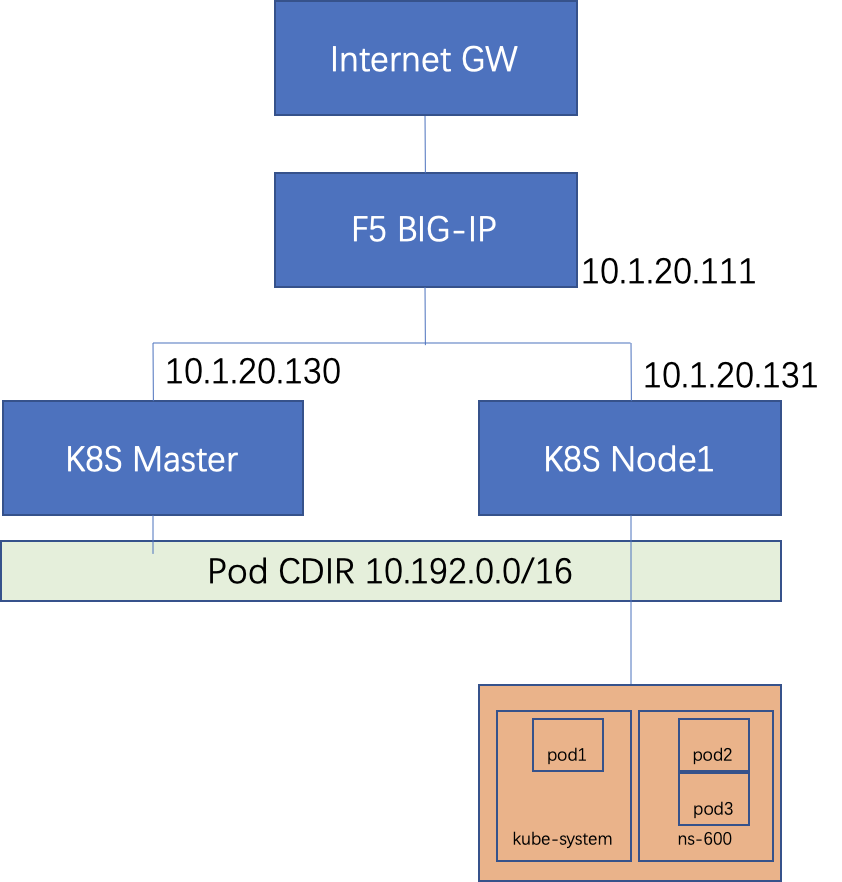
The figure below shows the LAB demonstration environment. To simplify network configuration, set all K8S node gateways to F5 AFM.
In actual deployment, all K8S node gateways are usually switches, and F5 may be connected to the switch when deployed. In this case, policy routing needs to be set on the switch, and the route for accessing external services from the Pod network segment to F5 is ensured to ensure that the outgoing traffic of the Pod passes through AFM.
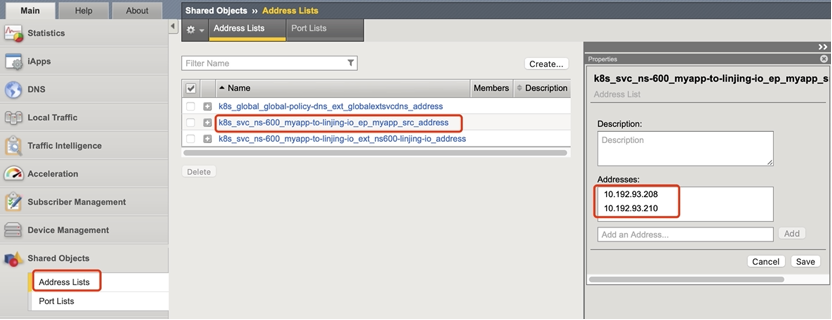
Deploy the ns-600per service outbound policy for the myapp service in . CES will automatically create a Pod IP address list in Shared Objects, and CES will automatically update this list when the number and IP of the same Service Pod change. An example is as follows:
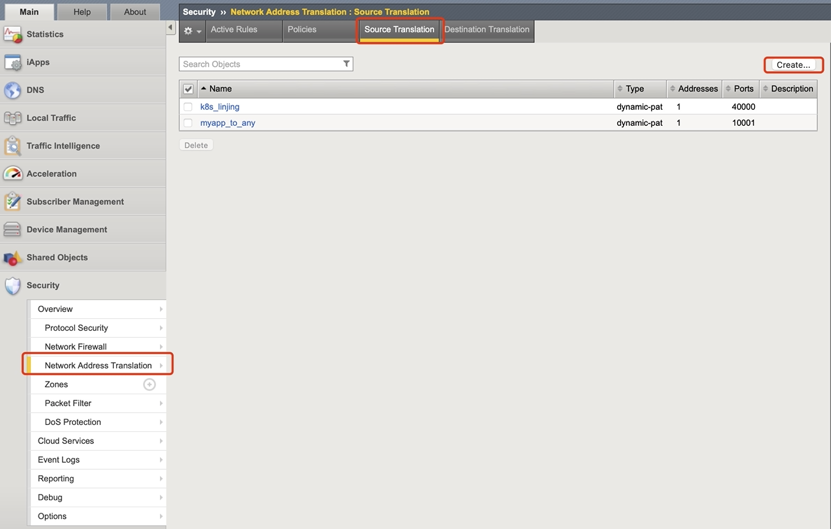
- Enter BIG-IP, in the Security - Network Address Translation - Source Translation menu, create a SNAT address:
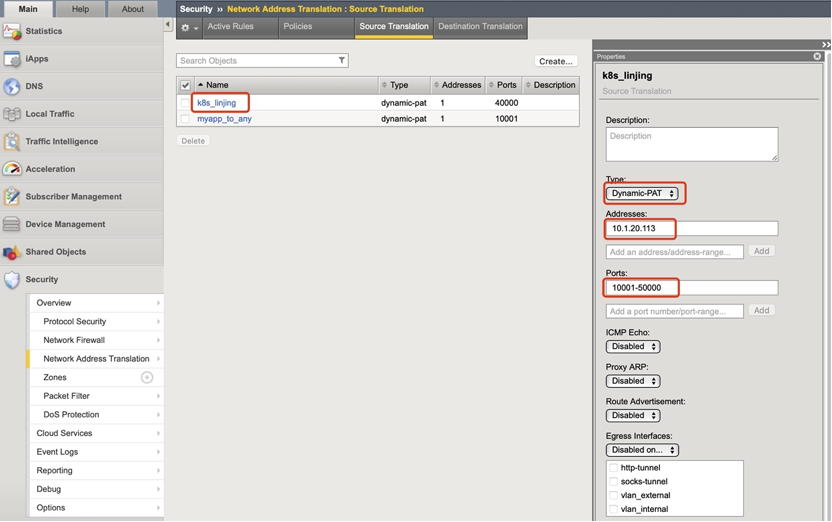
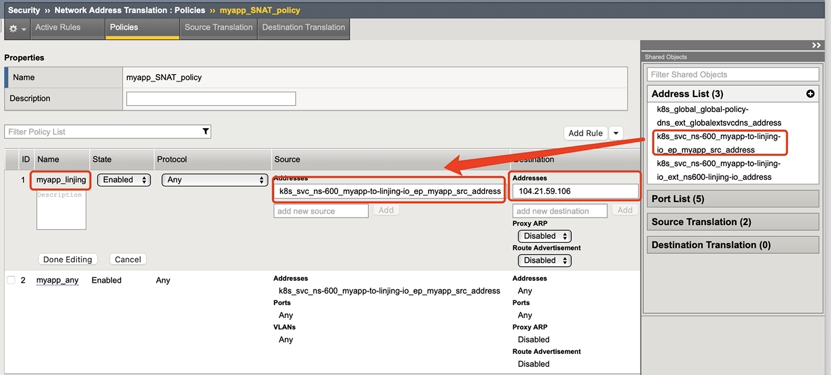
- In the Security - Network Address Translation - Policies menu, create a NAT policy
Note: When adding a source address, you can drag it from the Address List on the right; Destination Address can be left blank to indicate Any or fill in a specific destination address, indicating that the SNAT policy takes effect on the destination address.
- Outbound vs associated SNAT policy
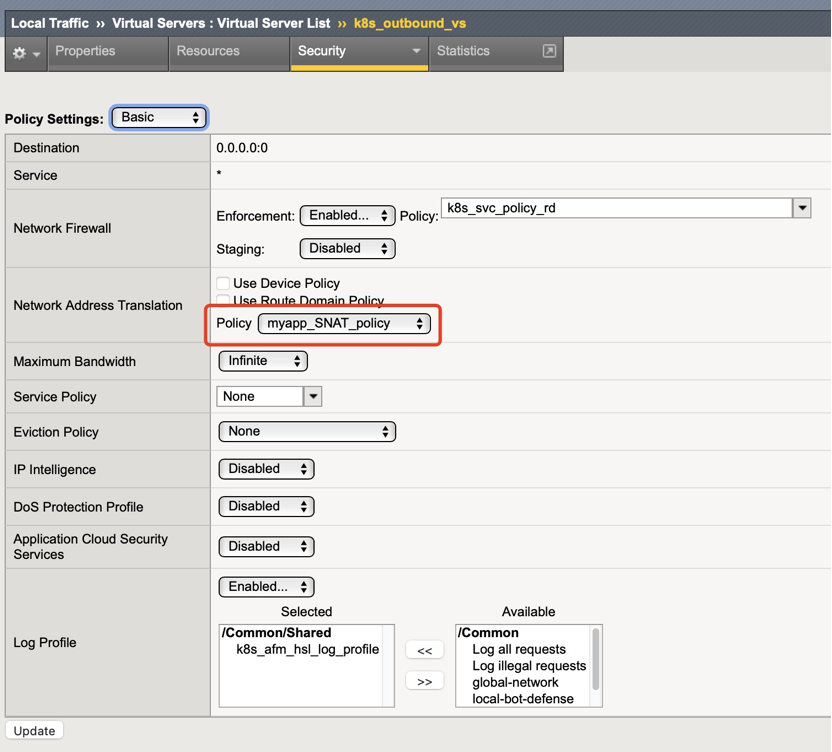
Note: At present, the SNAT policy needs to be manually associated. When the NAT policy is associated, the SNAT of vs needs to be set to None, and the pool cannot be associated. Future plans to add to CES form standard features.
- Verify SNAT rules
There are two outbound access SNAT policies in the LAB
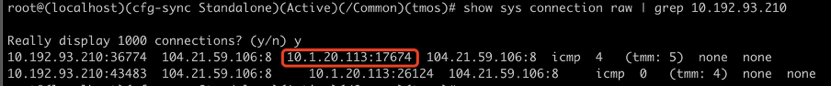
- Myapp Service Pod accesses 104.21.59.106 using source address 10.1.20.113
- Myapp Service Pod accesses Any using source address 10.1.20.115
Note: 104.21.59.106 is the A record of linjing.io
To verify the access, select a Myapp Service Pod arbitrarily, access linjing.io and baidu.com after entering the container, view the connection table in AFM, and confirm the SNAT mapping relationship:
Ping linjing.io in the above pod:
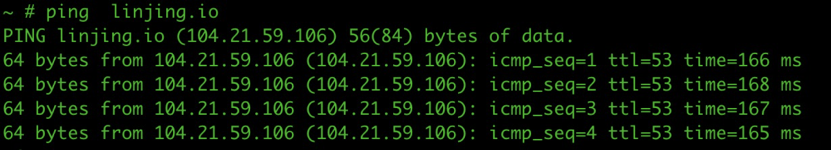
Looking at the AFM table, you can see that the SNAT address used is 10.1.20.113:
Continue to ping www.baidu.com in the Pod:
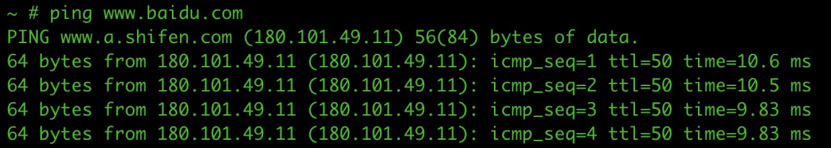
Query the connection table, you can see that the SNAT address is 10.1.20.115:
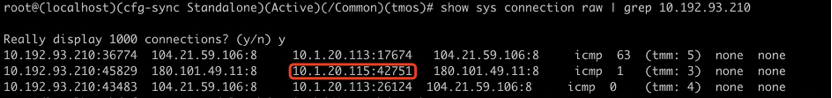
It can be seen that CES+F5 BIG-IP can perform SNAT IP management and control according to the fine-grained Per Service dimension, and can set different SNAT IP rules for the same service to access different targets, thus realizing the flexibility and intelligence of fixed source address SNAT change.
Next step