diff --git a/docusaurus.config.js b/docusaurus.config.js
index 4bff9de5e4..4844bbaf61 100644
--- a/docusaurus.config.js
+++ b/docusaurus.config.js
@@ -37,9 +37,9 @@ const config = {
banner: "none",
path: "/",
},
- "1.13": {
- label: "1.13",
- path: "1.13",
+ "1.14": {
+ label: "1.14",
+ path: "1.14",
banner: "none"
},
},
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.10.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.10.0.md
new file mode 100644
index 0000000000..0fcf6dee47
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.10.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 24.0.6
+docker-buildx: 0.11.2
+docker-compose: 2.21.0
+docker-credential-helpers: 0.8.0
+helm: 3.12.3
+kuberlr: 0.4.2
+nerdctl: 1.5.0
+trivy: 0.45.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.11.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.11.0.md
new file mode 100644
index 0000000000..985e09fb75
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.11.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 24.0.6
+docker-buildx: 0.12.0
+docker-compose: 2.22.0
+docker-credential-helpers: 0.8.0
+helm: 3.13.1
+kuberlr: 0.4.4
+nerdctl: 1.6.2
+trivy: 0.46.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.12.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.12.0.md
new file mode 100644
index 0000000000..fb00c1577d
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.12.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 24.0.6
+docker-buildx: 0.12.0
+docker-compose: 2.22.0
+docker-credential-helpers: 0.8.0
+helm: 3.13.3
+kuberlr: 0.4.4
+nerdctl: 1.6.2
+trivy: 0.46.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.13.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.13.0.md
new file mode 100644
index 0000000000..43969ecec8
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.13.0.md
@@ -0,0 +1,10 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 25.0.4
+docker-buildx: 0.13.0
+docker-compose: 2.24.7
+docker-credential-helpers: 0.8.1
+helm: 3.14.2
+kuberlr: 0.4.5
+nerdctl: 1.7.3
+spin-shim: 0.11.1
+trivy: 0.49.1
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.14.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.14.0.md
new file mode 100644
index 0000000000..0658b36f0a
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.14.0.md
@@ -0,0 +1,12 @@
+amazon-ecr-credential-helper: 0.8.0
+docker: 26.1.0
+docker-buildx: 0.14.1
+docker-compose: 2.27.1
+docker-credential-helpers: 0.8.2
+helm: 3.15.1
+kuberlr: 0.4.5
+nerdctl: 1.7.6
+spin: 2.5.1
+spin-shim: 0.14.1
+spinkube: 0.2.0
+trivy: 0.51.4
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.6.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.6.0.md
new file mode 100644
index 0000000000..011346c7e1
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.6.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.6.0
+docker: 20.10.17
+docker-buildx: 0.9.1
+docker-compose: 2.11.1
+docker-credential-helpers: 0.6.4
+helm: 3.9.4
+kuberlr: 0.4.2
+nerdctl: 0.23.0
+trivy: 0.32.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.7.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.7.0.md
new file mode 100644
index 0000000000..a697b2a9fb
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.7.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.6.0
+docker: 20.10.21
+docker-buildx: 0.9.1
+docker-compose: 2.14.0
+docker-credential-helpers: 0.6.4
+helm: 3.10.2
+kuberlr: 0.4.2
+nerdctl: 1.0.0
+trivy: 0.35.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.8.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.8.0.md
new file mode 100644
index 0000000000..3ab897d6c9
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.8.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.6.0
+docker: 23.0.1
+docker-buildx: 0.10.4
+docker-compose: 2.16.0
+docker-credential-helpers: 0.6.4
+helm: 3.11.2
+kuberlr: 0.4.2
+nerdctl: 1.2.1
+trivy: 0.38.3
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0-tech-preview.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0-tech-preview.md
new file mode 100644
index 0000000000..5208832f73
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0-tech-preview.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.6.0
+docker: 23.0.3
+docker-buildx: 0.10.4
+docker-compose: 2.17.2
+docker-credential-helpers: 0.6.4
+helm: 3.11.3
+kuberlr: 0.4.2
+nerdctl: 1.3.0
+trivy: 0.39.1
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0.md
new file mode 100644
index 0000000000..48c8092d7e
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.0.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 24.0.2
+docker-buildx: 0.10.5
+docker-compose: 2.18.1
+docker-credential-helpers: 0.7.0
+helm: 3.12.0
+kuberlr: 0.4.2
+nerdctl: 1.4.0
+trivy: 0.42.0
diff --git a/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.1.md b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.1.md
new file mode 100644
index 0000000000..e16df95623
--- /dev/null
+++ b/versioned_docs/version-1.14/bundled-utilities-version-info/v1.9.1.md
@@ -0,0 +1,9 @@
+amazon-ecr-credential-helper: 0.7.1
+docker: 24.0.2
+docker-buildx: 0.11.0
+docker-compose: 2.19.0
+docker-credential-helpers: 0.7.0
+helm: 3.12.1
+kuberlr: 0.4.2
+nerdctl: 1.4.0
+trivy: 0.42.1
diff --git a/versioned_docs/version-1.14/faq.md b/versioned_docs/version-1.14/faq.md
new file mode 100644
index 0000000000..af8d0e16f9
--- /dev/null
+++ b/versioned_docs/version-1.14/faq.md
@@ -0,0 +1,232 @@
+---
+title: FAQ
+---
+
+import Tabs from '@theme/Tabs';
+import TabItem from '@theme/TabItem';
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+This FAQ is a work in progress designed to answer the questions our users most frequently ask about Rancher Desktop.
+
+#### **Q: Is Rancher Desktop a desktop version of Rancher?**
+
+**A:** No. Rancher Desktop is not Rancher on the Desktop.
+
+While [Rancher](https://rancher.com/) and [Rancher Desktop](https://rancherdesktop.io/) share the _Rancher_ name, they do different things. But, the two solutions do complement each other:
+
+Rancher is a complete software stack for managing multiple Kubernetes clusters across any infrastructure.
+
+Rancher Desktop provides container management and a Kubernetes instance on the desktop to support local development use cases.
+
+#### **Q: Is there a Kubernetes Cluster Explorer available in Rancher Desktop?**
+
+**A:** Yes, the Rancher Dashboard is included as a feature preview in the release 1.2.1. Invoke the dashboard by clicking on **Dashboard** option in the system tray menu.
+
+Learn more about [Rancher Desktop](./getting-started/introduction.md).
+Learn more about [Rancher](https://rancher.com/why-rancher).
+
+[Rancher]:
+https://rancher.com/
+
+[minikube]:
+https://minikube.sigs.k8s.io/docs/
+
+[kind]:
+https://kind.sigs.k8s.io/docs/user/quick-start/
+
+[Docker Desktop]:
+https://docs.docker.com/desktop/
+
+
+#### **Q: Can I have Docker Desktop installed alongside Rancher Desktop?**
+
+**A:** Yes, but they cannot be run at the same time as both Rancher Desktop and Docker Desktop use the same Docker socket (`/var/run/docker.sock`). Be sure to stop one before starting the other.
+
+
+
+
+#### **Q: How can I perform a clean uninstall of Rancher Desktop?**
+
+**A:** First, perform a [Factory Reset](ui/troubleshooting.md#factory-reset), and then uninstall the app. The uninstall process varies based on the operating system. For more information, please refer [here](./getting-started/installation.md).
+
+#### **Q: What support, if any, is available for DNS over VPN on Windows?**
+
+**A:** An alternative DNS resolver for Windows has been implemented to address some of the VPN issues on Windows. It should support DNS lookup over VPN connections. It has to be enabled manually by editing an internal [configuration file](https://github.com/rancher-sandbox/rancher-desktop/issues/1899#issuecomment-1109128277).
+
+#### **Q: What does the "WSL Integration" tab do?**
+
+**A:** This makes the Kubernetes configuration accessible in the displayed WSL distributions so that you can use commands such as `kubectl` to communicate with Kubernetes.
+
+#### **Q: Where can I find detailed logs?**
+
+**A:** Click on the **Troubleshooting** tab, then click on **Show Logs**.
+
+#### **Q: How can I enable the dashboard for the Traefik ingress controller?**
+
+**A:** For security reasons, the Traefik dashboard is not exposed by default. However, it is possible to expose the dashboard in multiple ways. For instance, you can use one of the two approaches shown below.
+
+##### Using `port-forward` to enable dashboard access
+
+```
+kubectl port-forward -n kube-system $(kubectl -n kube-system get pods --selector "app.kubernetes.io/name=traefik" --output=name) 9000:9000
+```
+
+Visit [http://127.0.0.1:9000/dashboard/](http://127.0.0.1:9000/dashboard/) in your browser to view the Traefik dashboard.
+
+##### Using `HelmChartConfig` to enable dashboard access
+
+Copy the instructions below into a file, for example, `expose-traefik.yaml`
+
+```yaml
+apiVersion: helm.cattle.io/v1
+kind: HelmChartConfig
+metadata:
+ name: traefik
+ namespace: kube-system
+spec:
+ valuesContent: |-
+ dashboard:
+ enabled: true
+ ports:
+ traefik:
+ expose: true # Avoid this in production deployments
+ logs:
+ access:
+ enabled: true
+```
+
+Run the command
+
+```
+kubectl apply -f expose-traefik.yaml
+```
+
+Visit [http://127.0.0.1:9000/dashboard/](http://127.0.0.1:9000/dashboard/) in your browser to view the Traefik dashboard.
+
+#### **Q: Can I disable Traefik, and will doing so remove Traefik resources?**
+
+**A:** Yes, you can disable Traefik in order to free up port 80 and 443 for alternate ingress configuration. Disabling Traefik will _not_ delete existing resources. By default, the `Enable Traefik` feature is selected under **Kubernetes Settings**; uncheck this box to disable it.
+
+If you want to delete Traefik resources, click on `Reset Kubernetes` on the **Kubernetes Settings** panel of the UI.
+
+#### **Q: Is there support for internal container port forwarding?**
+
+**A:** Yes, support for this feature is available on all three platforms, Windows, Linux, and macOS, as of [v1.1.0](https://github.com/rancher-sandbox/rancher-desktop/releases/tag/v1.1.0).
+
+#### **Q: Does file sharing work similarly to Docker Desktop? Do I have to do any additional configuration to mount volumes to VMs?**
+
+**A:** Currently, the following directories are shared by default: `/Users/$USER` on macOS, `/home/$USER` on Linux, and `/tmp/rancher-desktop` on both. For Windows, all files are automatically shared via WSL2.
+
+Standard Docker volumes that are not generally accessible from the host computer work out of the box.
+
+To access other directories on Linux/macOS, you will have to perform additional configuration.
+
+If you want to change the behavior of the mounts, that will also require [additional configuration](https://github.com/rancher-sandbox/rancher-desktop/issues/1209#issuecomment-1370181132).
+
+#### **Q: Can containers reach back to host services via `host.docker.internal`?**
+
+**A:** Yes. On Windows, you may need to create a firewall rule to allow communication between the host and the container. You can run below command in a privileged powershell to create the firewall rule.
+
+```
+New-NetFirewallRule -DisplayName "WSL" -Direction Inbound -InterfaceAlias "vEthernet (WSL)" -Action Allow
+```
+
+
+#### **Q: I don't need the Kubernetes cluster deployed by Rancher Desktop; how do I disable it to save resources?**
+
+**A:** Open **Rancher Desktop** settings, click the cog to open **Preferences**, select **Kuberentes**, uncheck `Enable Kubernetes` feature is selected under **Kubernetes Settings**; uncheck this box to disable it.
+
+This will allow you to run just `containerd` or `dockerd` by without allocating resources for Kubernetes.
+
+
+#### **Q: What's happening to the Kubernetes Image Manager (kim)?**
+
+**A:** As of version 1.0, Kim is no longer shipped and has been replaced by nerdctl and the Docker CLI.
+
+
+#### **Q: Running `brew install rancher` is failing with a `It seems there is already a Binary at '/usr/local/bin/'` error, why?**
+
+**A:** If any of the Rancher Desktop supporting utilities (Helm, kubectl, nerdctl, docker) are already managed by Homebrew, then the installation fails due to how the Homebrew cask formula is defined. Installing using the Mac app will avoid this issue.
+
+#### Q: I installed `nerdctl` through the Arch User Repository, but it doesn't work with Rancher Desktop, why?
+
+**A:** For Rancher Desktop, `nerdctl` must run inside the VM and not on the host. The host version distributed with Rancher Desktop is just a shell wrapper to execute the command inside the VM.
+
+
+#### **Q: The tools on the Support Utilities page (in Rancher Desktop `<1.3.0`) are not installed and I see an `Insufficient permission to manipulate /usr/local/bin` error, how do I fix it?**
+
+**A:** This occurs when you do not have ownership of `/usr/local/bin`. A long-term solution to improve the handling of permissions is in the works. In the meantime, a temporary workaround is to change ownership of `/usr/local/bin` by running `sudo chown $USER /usr/local/bin`. When you are able to write to the directory, Rancher Desktop should be able to create the symlinks.
+
+From versions 1.3.0 and above, we no longer create symlinks in `/usr/local/bin` but in `~/.rd/bin` and put that directory on the PATH instead, to avoid having to deal with write permissions to `/usr/local/bin` and file conflicts. We strongly recommend you to upgrade to the latest version of Rancher Desktop.
+
+
+#### **Q: Is Cygwin compatible with Rancher Desktop?**
+
+**A:** No, but there are plans to add compatibility.
+
+#### **Q: Where does Rancher Desktop actually put the data volumes?**
+
+**A:**
+
+**Windows:**
+Open Run menu (Press Windows + R) and open the path provided below, depending on the active container runtime.
+```
+dockerd(moby): \\wsl$\rancher-desktop-data\var\lib\docker\volumes
+containerd: \\wsl$\rancher-desktop-data\var\lib\nerdctl\dbb19c5e\volumes\
+```
+**macOS & Linux:**
+Navigate to the path provided below in the (lima) VM, depending on the active container runtime. You can use `rdctl shell` to access these paths in the VM.
+```
+dockerd(moby): /var/lib/docker/volumes
+containerd: /var/lib/nerdctl/dbb19c5e/volumes/
+```
+#### **Q: How can I downgrade Rancher Desktop to a non-current (older) release version**
+
+**A:** We strongly recommend you use the current release version as it has the latest features and bug fixes included. However, if you want to downgrade to an earlier version, please follow the steps below.
+
+1. Perform `Troubleshooting > Factory Reset` from the current installation. Please make sure the `Keep cached Kubernetes images` box is *not* checked in the `Factory Reset` pop up dialog.
+2. For downgrading on Windows platforms, please shutdown WSL before installing an older version of Rancher Desktop with `wsl --shutdown` in a PowerShell command prompt.
+3. Uninstall the current version by following [uninstallation instructions](./getting-started/installation.md) for your OS.
+4. Install the older version that you need.
+
+#### Q: Rancher Desktop becomes unresponsive after my Windows machine wakes up from hibernation. How can I get my Rancher Desktop session working again with out having to reboot my machine?
+
+**A:** This is because of a WSL [bug](https://github.com/microsoft/WSL/issues/8696) that makes WSL unresponsive after hibernation on some Windows configurations. While the WSL bug itself is not yet resolved, various workarounds discussed on the GitHub issue thread make the problem a bit less frustrating; you can at least avoid a machine restart to get WSL and Rancher Desktop working again. You can follow the below steps.
+
+1. Shutdown WSL via the command `wsl --shutdown`. If the `wsl --shutdown` command is successful then jump to step 3.
+2. Stop and Restart the LxssManager service.
+
+
+
+
+- Stop the LxssManager service.
+```
+stop-service lxssmanager
+```
+
+- Start the LxssManager service.
+```
+start-service lxssmanager
+```
+
+
+
+
+Open the list of services running on your machine using the command `services.msc`. Locate the lxssmanager service in the list, right-click on it, and select `Stop`, `Start` to stop and start the service.
+
+
+
+
+3. Exit and Restart Rancher Desktop.
+
+#### **Q: What is `rancher-desktop-data` and why is it in a stopped state?**
+
+**A:** `rancher-desktop-data` is a persistent volume used for storage, such as container images. When running, the volume is mounted inside the `rancher-desktop` distribution and it will never run by itself. It is for implementation purposes and can be ignored by Rancher Desktop users.
diff --git a/versioned_docs/version-1.14/getting-started/deployment.md b/versioned_docs/version-1.14/getting-started/deployment.md
new file mode 100644
index 0000000000..4bc8accdb0
--- /dev/null
+++ b/versioned_docs/version-1.14/getting-started/deployment.md
@@ -0,0 +1,393 @@
+---
+title: Deployment Profiles
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Deployment profiles provide 2 features:
+
+* "Defaults" provide preference values that are applied on first run (or after a factory reset).
+* "Locked" settings allow an administrator to pin preference values.
+
+They can be specified both by an "admin" or by the "user". If either the "defaults" or the "locked" settings exists in the "admin" context, then the "user" profile is ignored.
+
+### Preferences Values at Startup
+
+Rancher Desktop settings are determined as follows:
+
+* Load "admin" deployment profile (both "defaults" and "locked")
+* If neither of them exist then load "user" deployment profile (again both "defaults" and "locked")
+* Load saved preferences from `settings.json` file
+* If there are no saved settings, use the "defaults" profile loaded earlier instead
+* Copy values from command-line arguments used to launch the app into settings
+* If the settings are still completely empty, show the first-run dialog
+* Fill any missing values from the builtin application defaults
+* Copy values from the "locked" profile over the current settings
+
+The user cannot modify any settings (via GUI or CLI) that have been locked by the profile.
+
+Rancher Desktop will refuse to load the application if a profile exists, but cannot be parsed correctly.
+
+Deployment profiles will not be modified or removed by Rancher Desktop. They will not be affected by a factory reset or uninstall.
+
+The structure of the profile data matches the application settings:
+
+```json title="rdctl list-settings"
+{
+ "version": 10,
+ ...
+ "containerEngine": {
+ "allowedImages": {
+ "enabled": false,
+ "patterns": []
+ },
+ "name": "containerd"
+ },
+ ...
+}
+```
+
+The platform-specific documentation below will show how to create a deployment profile that changes the default container engine to `moby`, disables Kubernetes, and locks down the list of allowed images to just `busybox` and `nginx`.
+
+### Locked Preference Fields
+
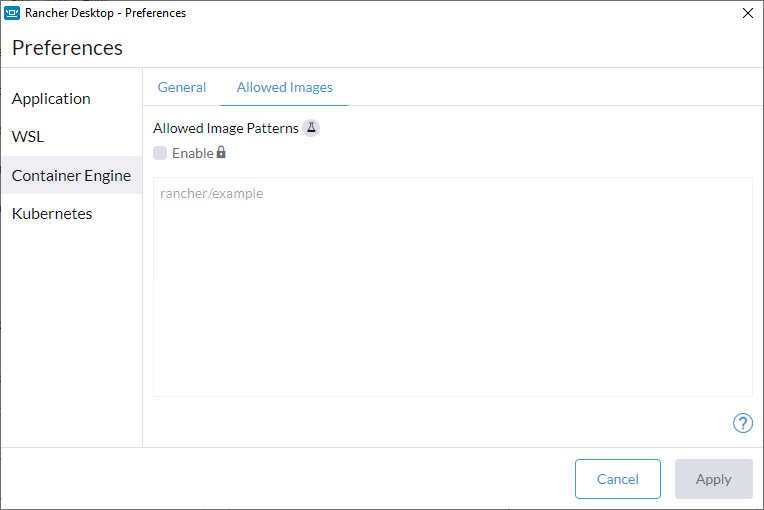
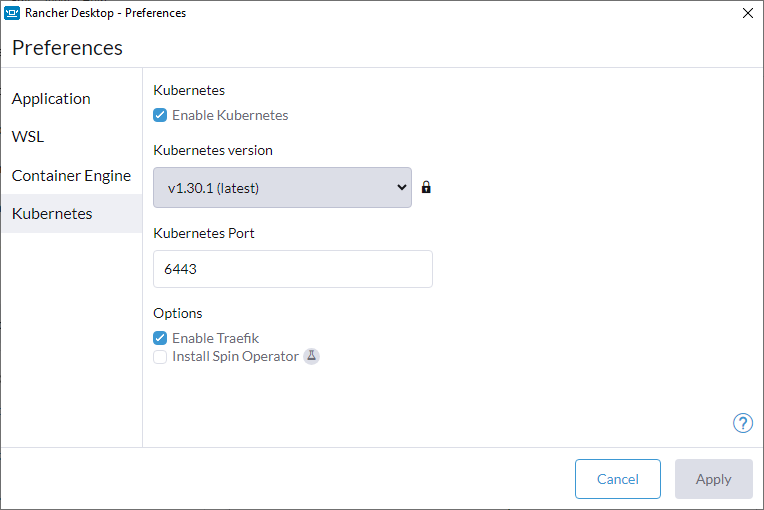
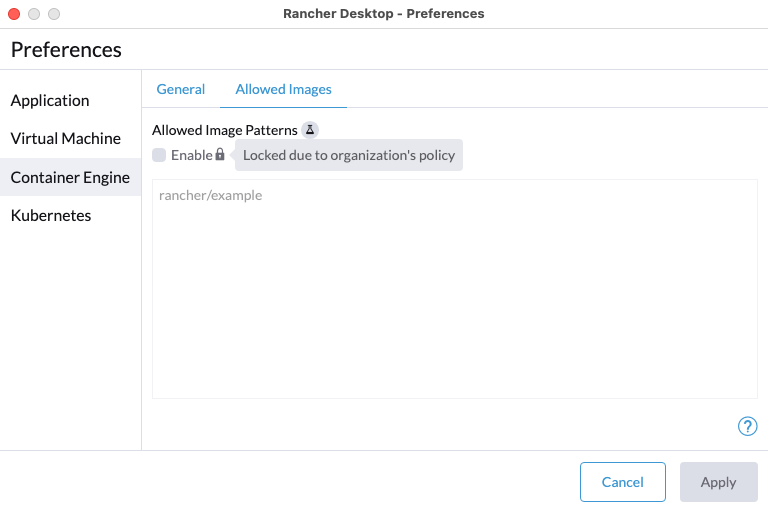
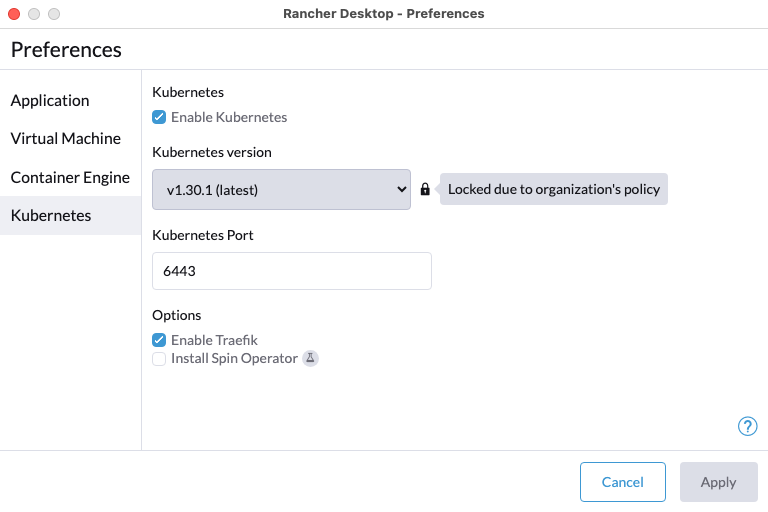
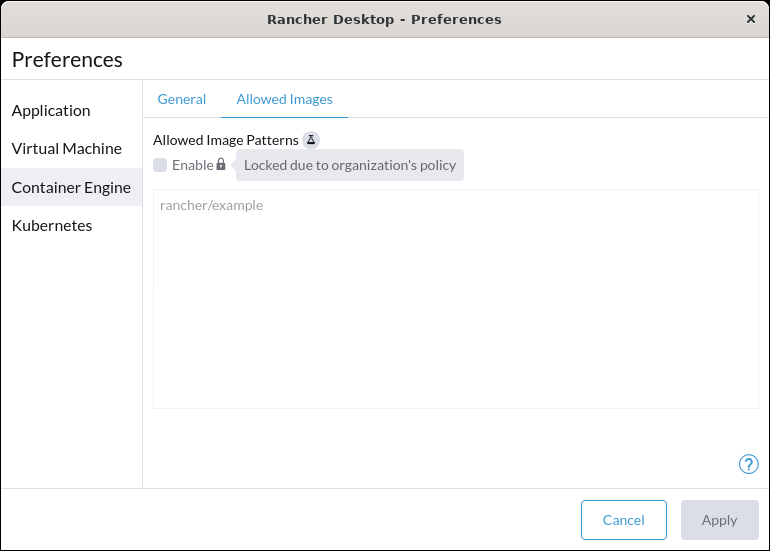
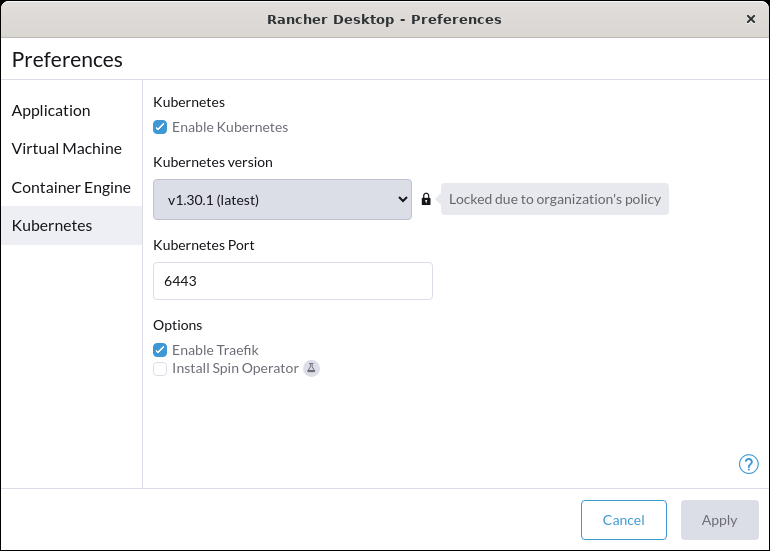
+For versions `1.9` and later of Rancher Desktop, all preferences values can be locked when configuring a deployment profile. Depending on the directory or registry used for the lock file creation, users may need to have super user permissions for MacOS/Linux or execute from an admin shell for Windows in order to access privileged paths. Once pinned, the various locked values will not be accessible from the application as seen in the UI examples below:
+
+
+Locked Fields UI Examples
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+### Profile Format and Location
+
+Deployment profiles are stored in a platform-specific format and location.
+
+
+
+
+On Windows the deployment profiles are stored in the registry and can be distributed via group policy.
+
+The locations for the profiles are:
+
+```
+HKEY_LOCAL_MACHINE\Software\Policies\Rancher Desktop\Defaults
+HKEY_LOCAL_MACHINE\Software\Policies\Rancher Desktop\Locked
+HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Defaults
+HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Locked
+```
+
+The `reg` tool can be used to create a profile manually. To create an "admin" profile it will have to be executed from an elevated shell.
+
+Boolean values are stored in `REG_DWORD` format, and lists in `REG_MULTI_SZ`.
+
+#### Delete existing profiles
+
+```
+reg delete "HKCU\Software\Policies\Rancher Desktop" /f
+```
+
+#### By default use the "moby" container engine and disable Kubernetes
+
+```
+reg add "HKCU\Software\Policies\Rancher Desktop\Defaults" /v version /t REG_DWORD -d 10
+reg add "HKCU\Software\Policies\Rancher Desktop\Defaults\containerEngine" /v name /t REG_SZ -d moby
+reg add "HKCU\Software\Policies\Rancher Desktop\Defaults\kubernetes" /v enabled /t REG_DWORD -d 0
+```
+
+#### Lock allowed images list to only allow "busybox" and "nginx"
+
+```
+reg add "HKCU\Software\Policies\Rancher Desktop\Locked" /v version /t REG_DWORD -d 10
+reg add "HKCU\Software\Policies\Rancher Desktop\Locked\containerEngine\allowedImages" /v enabled /t REG_DWORD -d 1
+reg add "HKCU\Software\Policies\Rancher Desktop\Locked\containerEngine\allowedImages" /v patterns /t REG_MULTI_SZ -d busybox\0nginx
+```
+
+#### Verify registry settings
+
+The profile can be exported into a `*.reg` file
+
+```
+C:\>reg export "HKCU\Software\Policies\Rancher Desktop" rd.reg
+The operation completed successfully.
+```
+
+This file can be used to distribute the profile to other machines. Note that the `REG_MULTI_SZ` values are encoded in UTF16LE, so are not easily readable:
+
+```text title="HKCU\Software\Policies\Rancher Desktop"
+Windows Registry Editor Version 5.00
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop]
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Defaults]
+"version"=dword:a
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Defaults\containerEngine]
+"name"="moby"
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Defaults\kubernetes]
+"enabled"=dword:00000000
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Locked]
+"version"=dword:a
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Locked\containerEngine]
+
+[HKEY_CURRENT_USER\Software\Policies\Rancher Desktop\Locked\containerEngine\allowedImages]
+"enabled"=dword:00000001
+"patterns"=hex(7):62,00,75,00,73,00,79,00,62,00,6f,00,78,00,00,00,6e,00,67,00,\
+ 69,00,6e,00,78,00,00,00,00,00
+```
+
+
+
+
+On macOS the deployment profiles are stored as plist files.
+
+The locations for the profiles are:
+
+```
+/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+/Library/Preferences/io.rancherdesktop.profile.locked.plist
+~/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+~/Library/Preferences/io.rancherdesktop.profile.locked.plist
+```
+
+#### Convert all current settings into a deployment profile
+
+A simple way to turn existing settings into a deployment profile is by converting them from JSON into the plist XML format, and then manually trimming it down in an editor.
+
+```
+rdctl list-settings | plutil -convert xml1 - -o ~/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+```
+
+Alternatively the profile can be created manually, either with an editor, or with the `plutil` tool. The `defaults` utility doesn't work because it cannot create nested keys.
+
+#### By default use the "moby" container engine and disable Kubernetes
+
+```
+DEFAULTS=~/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+plutil -create xml1 "$DEFAULTS"
+
+plutil -insert version -integer 10 "$DEFAULTS"
+
+plutil -insert containerEngine -dictionary "$DEFAULTS"
+plutil -insert containerEngine.name -string moby "$DEFAULTS"
+
+plutil -insert kubernetes -dictionary "$DEFAULTS"
+plutil -insert kubernetes.enabled -bool false "$DEFAULTS"
+```
+
+#### Lock allowed images list to only allow "busybox" and "nginx"
+
+```
+LOCKED=~/Library/Preferences/io.rancherdesktop.profile.locked.plist
+plutil -create xml1 "$LOCKED"
+
+plutil -insert version -integer 10 "$LOCKED"
+
+plutil -insert containerEngine -dictionary "$LOCKED"
+plutil -insert containerEngine.allowedImages -dictionary "$LOCKED"
+plutil -insert containerEngine.allowedImages.enabled -bool true "$LOCKED"
+
+plutil -insert containerEngine.allowedImages.patterns -array "$LOCKED"
+plutil -insert containerEngine.allowedImages.patterns -string busybox -append "$LOCKED"
+plutil -insert containerEngine.allowedImages.patterns -string nginx -append "$LOCKED"
+```
+
+#### Verify the plist files
+
+```xml title="~/Library/Preferences/io.rancherdesktop.profile.defaults.plist"
+
+
+
+
+ containerEngine
+
+ name
+ moby
+
+ kubernetes
+
+ enabled
+
+
+ version
+ 10
+
+
+```
+
+```xml title="~/Library/Preferences/io.rancherdesktop.profile.locked.plist"
+
+
+
+
+ containerEngine
+
+ allowedImages
+
+ enabled
+
+ patterns
+
+ busybox
+ nginx
+
+
+
+ version
+ 10
+
+
+```
+
+
+
+
+On Linux the deployment profiles are stored in JSON format.
+
+The locations for the profiles are:
+
+```
+/etc/rancher-desktop/defaults.json
+/etc/rancher-desktop/locked.json
+~/.config/rancher-desktop.defaults.json
+~/.config/rancher-desktop.locked.json
+```
+
+#### Convert all current settings into a deployment profile
+
+Since deployment profiles are stored in JSON format, the simplest way to create them is by saving the current application settings to the profile location, and then fine-tuning the profile with a text editor.
+
+```
+rdctl list-settings > ~/.config/rancher-desktop.defaults.json
+```
+
+#### By default use the "moby" container engine and disable Kubernetes
+
+```json title="~/.config/rancher-desktop.defaults.json"
+{
+ "version": 10,
+ "containerEngine": {
+ "name": "moby"
+ },
+ "kubernetes": {
+ "enabled": false
+ }
+}
+```
+
+#### Lock allowed images list to only allow "busybox" and "nginx"
+
+```json title="~/.config/rancher-desktop.locked.json"
+{
+ "version": 10,
+ "containerEngine": {
+ "allowedImages": {
+ "enabled": true,
+ "patterns": ["busybox","nginx"]
+ }
+ }
+}
+```
+
+
+
+
+### `version` Field
+
+Rancher Desktop version 1.12 introduces an explicit deployment profile `version` field in generated profiles using `rdctl`.
+
+If you are using deployment profiles created in previous Rancher Desktop versions, please either regenerate the file with the latest installation, or explicitly add the `version` field to your existing file. See below for updating instructions for various operating systems:
+
+#### Linux
+
+User deployments are stored in:
+
+```console
+~/.config/rancher-desktop.defaults.json
+~/.config/rancher-desktop.locked.json
+```
+
+If the `XDG_CONFIG_HOME` environment variable is set, the user deployments are stored there instead of in `~/.config/....`.
+
+System deployments are stored in:
+
+```console
+/etc/rancher-desktop/defaults.json
+/etc/rancher-desktop/locked.json
+```
+
+Then add `"version": 10` at the very start of your JSON-formatted file immediately after the initial open brace `(})`.
+
+#### macOS
+
+User deployments are stored in:
+
+```console
+~/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+~/Library/Preferences/io.rancherdesktop.profile.locked.plist
+```
+
+System deployments are stored in:
+
+```console
+/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+/Library/Preferences/io.rancherdesktop.profile.locked.plist
+```
+
+Then add `version10` after the initial `` tag into your respective `.plist` file.
+
+#### Windows
+
+The Windows deployments are stored in the registry. User deployments are stored at:
+
+```console
+HKEY_CURRENT_USER\SOFTWARE\Policies\Rancher Desktop\Defaults
+HKEY_CURRENT_USER\SOFTWARE\Policies\Rancher Desktop\Locked
+```
+
+And the system deployments are stored at:
+
+```console
+HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Rancher Desktop\Defaults
+HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Rancher Desktop\Locked
+```
+
+Then add a `DWORD` value named `version`, with value `10` (hexadecimal `a`) at the top level of each profile that needs updating:
+
+```console
+"version"=dword:a
+```
+
+### Known Issues and Limitations
+
+* You can set default values for `diagnostics.showMuted` (and on Windows `WSL.integrations`) via deployment profile, but currently can't lock them.
diff --git a/versioned_docs/version-1.14/getting-started/installation.md b/versioned_docs/version-1.14/getting-started/installation.md
new file mode 100644
index 0000000000..a223388412
--- /dev/null
+++ b/versioned_docs/version-1.14/getting-started/installation.md
@@ -0,0 +1,286 @@
+---
+title: Installation
+---
+
+
+
+
+
+Rancher Desktop is delivered as a desktop application. You can download it from
+the [releases page on GitHub](https://github.com/rancher-sandbox/rancher-desktop/releases).
+
+When run for the first time or when changing versions, Kubernetes container
+images are downloaded. It may take a little time to load on first run for a new
+Kubernetes version.
+
+After Rancher Desktop is installed, users will have access to these supporting utilities:
+
+- [Helm](https://helm.sh/)
+- [kubectl](https://kubernetes.io/docs/reference/kubectl/overview/)
+- [nerdctl](https://github.com/containerd/nerdctl)
+- [Moby](https://github.com/moby/moby)
+- [Docker Compose](https://docs.docker.com/compose/)
+
+## macOS
+
+### Requirements
+
+Rancher Desktop requires the following on macOS:
+
+- macOS Catalina 10.15 or higher.
+- Apple Silicon (M1) or Intel CPU with VT-x.
+- Persistent internet connection.
+
+It is also recommended to have:
+
+- 8 GB of memory
+- 4 CPU
+
+Additional resources may be required depending on the workloads you plan to run.
+
+### Installing Rancher Desktop on macOS
+
+1. Go to the [releases page] on GitHub.
+1. Find the version of Rancher Desktop you want to download.
+1. Expand the **Assets** section and download `Rancher.Desktop-X.Y.Z.dmg`, where `X.Y.Z` is the version of Rancher Desktop.
+1. Navigate to the directory where you downloaded the installer to and run the installer. This will usually be the `Downloads` folder.
+1. Double-click the DMG file.
+1. In the Finder window that opens, drag the Rancher Desktop icon to the Applications folder.
+1. Navigate to the `Applications` folder and double-click the Rancher Desktop to launch it.
+
+[releases page]:
+https://github.com/rancher-sandbox/rancher-desktop/releases
+
+After Rancher Desktop is installed, users will have access to these supporting utilities:
+
+- [Helm](https://helm.sh/)
+- [kubectl](https://kubernetes.io/docs/reference/kubectl/overview/)
+- [nerdctl](https://github.com/containerd/nerdctl)
+- [docker (moby)](https://github.com/moby/moby)
+
+### Uninstalling Rancher Desktop on macOS
+
+1. Open **Finder** > **Applications**.
+1. Find Rancher Desktop.
+1. Select it and choose **File > Move to Trash**.
+1. To delete the app, Finder > Empty Trash.
+
+## Windows
+
+### Requirements
+
+Rancher Desktop requires the following on Windows:
+
+- Windows 10 build 1909 or higher. The Home edition is supported.
+- Running on a machine with [virtualization capabilities].
+- Persistent internet connection.
+
+Rancher Desktop requires [Windows Subsystem for Linux] on Windows; this will
+automatically be installed as part of the Rancher Desktop setup. Manually
+downloading a distribution is not necessary.
+
+[Windows Subsystem for Linux]:
+https://docs.microsoft.com/en-us/windows/wsl/install-win10
+
+[virtualization capabilities]:
+https://docs.microsoft.com/en-us/windows/wsl/troubleshooting#error-0x80370102-the-virtual-machine-could-not-be-started-because-a-required-feature-is-not-installed
+
+It is also recommended to have:
+
+- 8 GB of memory
+- 4 CPU
+
+Additional resources may be required depending on the workloads you plan to run.
+
+**Note:** You can use Rancher Desktop as a Non-Admin user on a Windows machine. However, an Admin's intervention is required during the installation process for the below components.
+
+- **WSL2 - ** You need Admin privileges to install WSL2, which is an essential component of Rancher Desktop.
+- **Rancher Desktop Privileged Service - ** You need Admin privileges to install the Rancher Desktop privileged service, which is required to expose applications/services, running inside containers, on all interfaces on the host machine. However, you can skip the installation of the Rancher Desktop Privileged Service with the limitation that you will not be able to expose applications/services on any interface except `127.0.0.1`.
+
+### Installing Rancher Desktop on Windows
+
+1. Go to the [releases page] on GitHub.
+1. Find the version of Rancher Desktop you want to download.
+1. Expand the **Assets** section and download the Windows installer. It will be called `Rancher.Desktop.Setup.X.Y.Z.msi`, where `X.Y.Z` is the version of Rancher Desktop.
+1. Navigate to the directory where you downloaded the installer to and run the installer. This will usually be the `Downloads` folder.
+1. Review the License Agreement and click **I Agree** to proceed with the installation.
+1. If prompted, choose between installing for everyone on the machine or installing
+ just for the current user. Installing for everyone is preferred in order to
+ install the Rancher Desktop Privileged Service, as noted above.
+1. Follow the prompts to confirm installation.
+1. When the installation completes, click **Finish** to close the installation wizard.
+
+[release page]:
+https://github.com/rancher-sandbox/rancher-desktop/releases
+
+### Uninstalling Rancher Desktop on Windows
+
+1. From the taskbar, click the **Start** menu.
+1. Go to **Settings > Apps > Apps & features**.
+1. Find and select the Rancher Desktop entry.
+1. Click **Uninstall** and click it again when the confirmation appears.
+1. Follow the prompts on the Rancher Desktop uninstaller to proceed.
+1. Click **Finish** when complete.
+
+## Linux
+
+### Requirements
+
+Rancher Desktop requires the following on Linux:
+
+- A distribution that can install .deb or .rpm packages, or AppImages.
+- A persistent internet connection.
+- An x86_64 processor with either AMD-V or VT-x.
+- Read-write access on `/dev/kvm`. See below for details.
+
+It is also recommended to have:
+
+- 8 GB of memory
+- 4 CPU
+
+Additional resources may be required depending on the workloads you plan to run.
+
+:::note
+Some Linux distributions such as Ubuntu and Fedora that make use of Gnome do not support a system tray out of the box, and therefore no tray icon will be displayed for Rancher Desktop in these environments.
+:::
+
+#### Ensuring You Have Access to `/dev/kvm`
+
+On some distributions (Ubuntu 18.04 for example) the user has insufficient
+privileges to use `/dev/kvm`, which is required for Rancher Desktop.
+To check whether you have the required privileges, do:
+
+```
+[ -r /dev/kvm ] && [ -w /dev/kvm ] || echo 'insufficient privileges'
+```
+
+If it outputs `insufficient privileges`, you need to add your user to the
+`kvm` group. You can do this with:
+
+```
+sudo usermod -a -G kvm "$USER"
+```
+
+Then reboot in order to make these changes take effect.
+
+
+#### `pass` Setup
+
+By default, Rancher Desktop uses `pass` to securely store credentials
+passed via `docker login` and `nerdctl login`. `pass` requires a small amount
+of setup if this is the first time it has been used on your machine. If you don't
+intend to use `docker login` or `nerdctl login` you don't have to set up
+`pass` - just remember that if you use them in the future, you must set it
+up or you will run into errors.
+
+Once Rancher Desktop is installed, you should create a GPG key. This will be
+used by `pass` to secure secrets. You can create a GPG key with:
+
+```
+gpg --generate-key
+```
+
+The output should contain something like `8D818FB37A9279E341F01506ED96AD27A40C9C73`.
+This is your key ID. You can then initialize `pass` by passing this key ID to it:
+
+```
+pass init 8D818FB37A9279E341F01506ED96AD27A40C9C73
+```
+
+For more information on `pass`, please see [its website].
+
+[its website]: https://www.passwordstore.org/
+
+
+#### Traefik Port Binding Access
+
+Rancher Desktop makes use of Traefik as the default ingress controller. Users may run into a `permission denied` error after deploying Rancher Desktop due to restricted port access on the Traefik ingress. Most Linux distributions (e.g. Ubuntu 20.04) do not allow non-root users to listen on TCP and UDP ports below `1024`. In order to allow Traefik to listen to privileged ports on the local host, please run the following command:
+
+```
+sudo sysctl -w net.ipv4.ip_unprivileged_port_start=80
+```
+
+After the command is run, all ports `80` and above will become unprivileged and Traefik will be able to successfully access said ports.
+
+To preserve this change across reboots as a custom kernel parameter setting, add the same command inside your `/etc/sysctl.conf` file.
+
+### Installation via .deb Package
+
+Add the Rancher Desktop repository and install Rancher Desktop with:
+
+```
+curl -s https://download.opensuse.org/repositories/isv:/Rancher:/stable/deb/Release.key | gpg --dearmor | sudo dd status=none of=/usr/share/keyrings/isv-rancher-stable-archive-keyring.gpg
+echo 'deb [signed-by=/usr/share/keyrings/isv-rancher-stable-archive-keyring.gpg] https://download.opensuse.org/repositories/isv:/Rancher:/stable/deb/ ./' | sudo dd status=none of=/etc/apt/sources.list.d/isv-rancher-stable.list
+sudo apt update
+sudo apt install rancher-desktop
+```
+
+
+### Uninstalling .deb Package
+
+You can remove the package, repository, and key with:
+
+```
+sudo apt remove --autoremove rancher-desktop
+sudo rm /etc/apt/sources.list.d/isv-rancher-stable.list
+sudo rm /usr/share/keyrings/isv-rancher-stable-archive-keyring.gpg
+sudo apt update
+```
+
+
+### Installing via .rpm Package
+
+**Note:** RHEL, Fedora, and related distributions package QEMU, which Rancher Desktop
+uses on Linux, differently than other distributions. To use Rancher Desktop on these
+distributions, please use the AppImage.
+
+To add the repository and install on openSUSE:
+
+```
+sudo zypper addrepo https://download.opensuse.org/repositories/isv:/Rancher:/stable/rpm/isv:Rancher:stable.repo
+sudo zypper install rancher-desktop
+```
+
+
+### Uninstalling .rpm Package
+
+Ensure that Rancher Desktop has exited (if not, it should appear in the dock) and do:
+
+```
+sudo zypper remove --clean-deps rancher-desktop
+sudo zypper removerepo isv_Rancher_stable
+```
+
+
+### Installing via AppImage
+
+First, ensure that `pass` and `gpg` are installed. For example, on Fedora:
+
+```
+dnf install pass gnupg2
+```
+
+You may download the AppImage [here]. In order to run it, simply make it executable
+and execute it. For better integration with your desktop, you may use [AppImageLauncher].
+
+[here]:
+https://download.opensuse.org/repositories/isv:/Rancher:/stable/AppImage/rancher-desktop-latest-x86_64.AppImage
+[AppImageLauncher]:
+https://github.com/TheAssassin/AppImageLauncher
+
+
+### Uninstalling AppImage
+
+Simply delete the AppImage. That's it!
+
+## Proxy Environments: Important URL Patterns
+
+There are situations where you may be using a secured, locked down internet environment and need to configure necessary Rancher Desktop dependencies through a proxy. Here is a list of key URL patterns you will need to allow through your proxy:
+
+- Get available K3s releases for download: https://api.github.com/repos/k3s-io/k3s/releases
+- Download K3s releases: https://github.com/k3s-io/k3s/releases/download
+- `kubectl` releases downloaded by `kuberlr`: https://storage.googleapis.com/kubernetes-release/release
+- Check available upgrade versions: https://desktop.version.rancher.io/v1/checkupgrade
+- Access the documentation from the application help menu and help buttons; also used to check online status: https://docs.rancherdesktop.io
+
+These dependencies are specific to Rancher Desktop and do not represent a standard list across the Rancher platform.
diff --git a/versioned_docs/version-1.14/getting-started/introduction.md b/versioned_docs/version-1.14/getting-started/introduction.md
new file mode 100644
index 0000000000..2c6f0899df
--- /dev/null
+++ b/versioned_docs/version-1.14/getting-started/introduction.md
@@ -0,0 +1,30 @@
+---
+title: Introduction
+slug: /
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
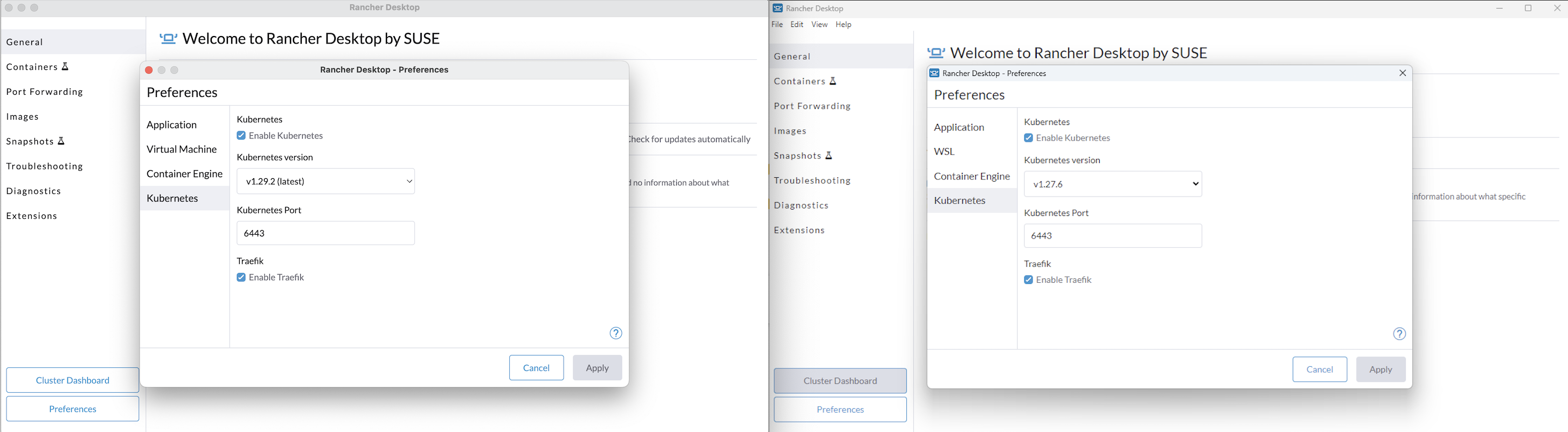
+Rancher Desktop is an app that provides container management and Kubernetes on the desktop. It is available for Mac (both on Intel and Apple Silicon), Windows, and Linux.
+
+
+
+_The above image shows Kubernetes settings on Mac on the left and Windows on the right._
+
+## Container Management
+
+Rancher Desktop provides the ability to build, push, and pull container images along with the ability to run containers. This is provided by either the Docker CLI (when you choose Moby/dockerd as you engine) or nerdctl (when you choose containerd as your engine). [nerdctl](https://github.com/containerd/nerdctl) is a "Docker-compatible CLI for containerd" provided by the containerd project.
+
+## Kubernetes
+
+Kubernetes is built in to Rancher Desktop. Kubernetes is provided by [k3s](https://k3s.io/), a lightweight certified distribution. With Rancher Desktop you have the ability to _choose your version of Kubernetes_ and _reset Kubernetes or Kubernetes and the whole container runtime with the click of a button_.
+
+## Rancher vs Rancher Desktop
+
+While [Rancher](https://rancher.com/) and Rancher Desktop share the _Rancher_ name they do different things. Rancher Desktop is not Rancher on the Desktop. Rancher is a powerful solution to manage Kubernetes clusters. Rancher Desktop provides a local Kubernetes and container management platform. The two solutions complement each other.
+
+If you want to run Rancher on your local system, you can install Rancher into Rancher Desktop.
diff --git a/versioned_docs/version-1.14/how-to-guides/create-multi-node-cluster.md b/versioned_docs/version-1.14/how-to-guides/create-multi-node-cluster.md
new file mode 100644
index 0000000000..b3d54131e7
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/create-multi-node-cluster.md
@@ -0,0 +1,48 @@
+---
+title: Create a Multi-Node Cluster with k3d
+---
+
+
+
+
+
+Rancher Desktop provides a **single cluster with single node** setup, which is adequate for most local development scenarios. However, there are use cases where, the ability to create a multi node cluster or spin up multiple clusters with flexibilty to switch between clusters is required. Eventhough Rancher Desktop doesn't have in-built multi node/cluster functionality, you can use [k3d](https://k3d.io) with Rancher Desktop to accomplish the same. k3d is a lightweight wrapper to run k3s (a minimal Kubernetes distribution, which is used by Rancher Desktop as well) in docker. k3d makes it very easy to create single- and multi-node k3s clusters in docker, e.g. for local development on Kubernetes.
+
+### Steps to spin up a multi-node cluster
+
+1. Make sure **dockerd(moby)** is selected as the Container Runtime in the **Kubernetes Settings** page.
+
+2. Install k3d.
+
+
+
+
+```
+wget -q -O - https://raw.githubusercontent.com/k3d-io/k3d/main/install.sh | bash
+```
+
+
+
+
+```
+curl -s https://raw.githubusercontent.com/k3d-io/k3d/main/install.sh | bash
+```
+
+
+
+
+3. Run `k3d cluster create` command to spin up multi node clusters. For example:
+
+```
+k3d cluster create two-node-cluster --agents 2
+k3d cluster create three-node-cluster --agents 3
+```
+
+4. k3d sets the newly created cluster as active. You can switch between clusters via `kubectl config use-context` command. For example:
+
+```
+kubectl config use-context k3d-two-node-cluster
+```
+To learn more about **k3s** and **k3d**, refer to these projects' docs at [k3s docs](https://docs.k3s.io/) and [k3d docs](https://k3d.io/).
+
+**:warning: Please note that the clusters created by `k3d` are not managed by Rancher Desktop GUI.**
diff --git a/versioned_docs/version-1.14/how-to-guides/generating-deployment-profiles.md b/versioned_docs/version-1.14/how-to-guides/generating-deployment-profiles.md
new file mode 100644
index 0000000000..1f87dec46b
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/generating-deployment-profiles.md
@@ -0,0 +1,192 @@
+---
+title: Generating Deployment Profiles
+---
+
+
+
+
+
+Deployment Profiles are a way of both providing first-time default settings for Rancher Desktop, and locking down any or all of the application settings. The purpose of this guide is to demonstrate how to create deployment profiles. General information about deployment profiles are further detailed in [Getting Started > Deployment Profiles](../getting-started/deployment.md).
+
+:::note
+If your organization has its own methods of remotely configuring users' systems, it is out of the scope of this document.
+:::
+
+## Where do deployment profiles get installed?
+
+The profile locations vary for each platform. We'll cover them from the simplest to most complex, and it is worth noting the file generation steps below will refer to these locations:
+
+### Linux
+
+User deployments are stored in:
+
+```bash
+~/.config/rancher-desktop.defaults.json
+~/.config/rancher-desktop.locked.json
+```
+
+If the `XDG_CONFIG_HOME` environment variable is set, the user deployments are stored there instead of in `~/.config/...`.
+
+System deployments always go in:
+
+```bash
+/etc/rancher-desktop/defaults.json
+/etc/rancher-desktop/locked.json
+```
+
+As is apparent from the filenames' extensions, they are `json` files.
+
+### macOS
+
+User deployments are stored in:
+
+```bash
+~/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+~/Library/Preferences/io.rancherdesktop.profile.locked.plist
+```
+
+System deployments always go in:
+
+```bash
+/Library/Preferences/io.rancherdesktop.profile.defaults.plist
+/Library/Preferences/io.rancherdesktop.profile.locked.plist
+```
+
+These two lists look similar but differ in permissions. The user-deployments go under the user's home directory, while the system deployments are in the common `/Library/` tree, and cannot be modified by users without root privileges.
+
+These files are all in a plain-text form of Apple's `plist` format, an XML-based language. It is possible to manually create these files, and the process is described below in "Generating Deployments".
+
+### Windows
+
+The Windows deployments are stored in the registry. User deployments are stored at:
+
+```shell
+HKEY_CURRENT_USER\SOFTWARE\Policies\Rancher Desktop\Defaults
+HKEY_CURRENT_USER\SOFTWARE\Policies\Rancher Desktop\Locked
+```
+
+And the system deployments are stored at:
+
+```shell
+HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Rancher Desktop\Defaults
+HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Rancher Desktop\Locked
+```
+
+The structure of the registry instances follows the structure of the JSON files for the other platforms. The name of a non-leaf node in the JSON structure (a name to the left of a ":") will appear as a registry key. Leaf nodes appear as key-value pairs in the right-hand pane of a key's view where the key is the field's name. And hash-like objects (like `WSL.integrations`) also appear as key-value pairs, in this case for the key `...\WSL\integrations`.
+
+Additionally, if you're coding against the registry, names are always case-insensitive. Feel free to use all lower-case, UPPER-CASE, or spOnGeBoBCasE.
+
+## Generating deployments
+
+The easiest way to do this is on a system already running Rancher Desktop, mainly for its `rdctl` command-line tool, and the default list of settings.
+
+First, you're going to want to verify that the deployments you create make sense on a working Rancher Desktop, so the rest of this document assumes you'll have access to it. Rancher Desktop runs on air-gapped systems, so if you're creating deployments for security-related reasons, security shouldn't be a concern while creating them.
+
+### Prerequisite
+
+We also assume you've installed the `jq` json tool. If you have a preferred variant, simply substitute it for `jq` in the following text.
+
+### Crafting JSON deployment files
+
+Let's assume you want to create both default-value and locked-value deployment profiles.
+
+:::note
+If you want to start with Rancher Desktop's default values, and don't have your own workloads you need to preserve, you can run `rdctl factory-reset` first.
+:::
+
+Start up Rancher Desktop, and run the following commands in your preferred shell:
+
+```shell
+rdctl list-settings | jq . > working-defaults.txt
+rdctl list-settings | jq . > working-locked.txt
+```
+
+If you're only making one type of profile, you'll only need one of the above lines, of course. It also is not necessary to create both a user and system profile for the same type of deployment. If Rancher Desktop sees a system-profile, it won't load the user-profile of the same kind. However, if Rancher Desktop finds, for example, a user-defaults and a system-locked profile, but no system-defaults profile, it will load the user-defaults and system-locked profiles.
+
+Next, you can edit each of the JSON files to contain only the values you care about. You can use the `jq` command to validate the final outputs:
+
+```shell
+jq -e . working-defaults.txt >/dev/null 2>&1
+```
+
+The command will have a 0 status if the file is valid (`True` on Powershell), 1 or `False` otherwise.
+
+Here's a sample locked-field JSON file:
+
+```json
+{
+ "containerEngine": {
+ "allowedImages": {
+ "enabled": true,
+ "patterns": [
+ "PATTERN1",
+ "PATTERN2"
+ ]
+ },
+ "name": "moby"
+ },
+ "kubernetes": {
+ "version": "1.24.10"
+ }
+}
+```
+
+:::caution Warning
+Users with this locked file will be able to use only `moby`, not `containerd`, and will only be able to pull container images that match the supplied patterns. They will also be constrained to using the specified kubernetes version.
+:::
+
+If you're on a Linux system, you can quickly test these files with the following steps:
+
+```bash
+# Shut down Rancher Desktop
+rdctl factory-reset
+cp working-defaults.txt ~/.config/rancher-desktop.defaults.json
+cp working-locked.txt ~/.config/rancher-desktop.locked.json
+```
+
+Now bring up Rancher Desktop, and bring up the `Preferences` window. Verify that the fields you entered in the `locked` file have the specified values, appear with a padlock icon in the UI, and can't be changed. Verify that the fields from the `defaults` value appear with the specified values in the UI,
+and can be changed (as expected, if a field appears in both the `defaults` and `locked` deployment profile, the `locked` value takes precedence).
+
+### Targeting other systems
+
+If all your users are on Linux systems, you're done, but if not, the rest is straightforward. `rdctl` can take a JSON file and generate a deployment for either macOS or Windows. Windows uses the registry, so we generate *registry import files*, and you can then use the `reg` command in a terminal to install them.
+
+#### macOS
+
+For macOS, you would run the following commands to generate either system or user deployment files:
+
+```bash
+rdctl create-profile --output plist --input working-defaults.txt > io.rancherdesktop.profile.defaults.plist
+rdctl create-profile --output plist --input working-locked.txt > io.rancherdesktop.profile.locked.plist
+```
+
+And the `io.*.plist` files just need to be deployed to the users' systems, as described above.
+
+#### Windows
+
+Windows differs from the other platforms. Here you specify the type of profile ("locked" or "defaults") and hive (`HKLM` or `HKCU`) on the command-line, and let the `run.exe` command decide which part of the registry to update:
+
+```bash
+rdctl create-profile --output reg --hive hklm --type defaults working-defaults.txt > reg-system-defaults.txt
+rdctl create-profile --output reg --hive hkcu --type defaults working-defaults.txt > reg-user-defaults.txt
+rdctl create-profile --output reg --hive hklm --type locked working-locked.txt > reg-system-locked.txt
+rdctl create-profile --output reg --hive hkcu --type locked working-locked.txt > reg-user-locked.txt
+```
+
+The above commands generate four different files, but as explained before, system takes precedence over user profiles, so there's only need to generate at most two files.
+
+You would then deploy the files to the target Windows systems, and in a shell with administrative privileges run the command:
+
+```bash
+reg import FILENAME
+```
+
+## Troubleshooting
+
+System profiles are loaded only when there is no `settings.json` in the config area - so these typically are loaded only on first-run and after a factory-reset.
+
+Locked profiles are loaded at the start of every run, and take precedence over the values in existing `settings.json` files (which means a crafty user can't shut down Rancher Desktop and manually edit the `settings.json` file to get around the locked-deployment-profile restrictions).
+
+### Running `reg.exe`
+
+Running `reg.exe` - registry entries under the `Policies` key can only be loaded with the `reg import` command when the user is running as an administrator.
diff --git a/versioned_docs/version-1.14/how-to-guides/hello-world-example.md b/versioned_docs/version-1.14/how-to-guides/hello-world-example.md
new file mode 100644
index 0000000000..e6b979d72b
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/hello-world-example.md
@@ -0,0 +1,147 @@
+---
+title: Hello World Example
+---
+
+
+
+
+
+This tutorial will demonstrate how to get started with Rancher Desktop by pushing an app to a local Kubernetes cluster.
+
+Rancher Desktop works with two container engines, [containerd](https://containerd.io/) and [Moby](https://mobyproject.org/), the open-sourced components of the Docker ecosystem. For `nerdctl`, use the **containerd** runtime. For `docker`, use the **dockerd(moby)** runtime.
+
+### Example#1 - Build Image & Run Container
+
+#### Create a folder
+```
+mkdir hello-world
+cd hello-world
+```
+
+#### Create a blank Dockerfile
+
+On Windows, Create a blank file named `Dockerfile`
+
+On Linux, You can use below command to create a blank `Dockerfile`
+
+```
+vi Dockerfile
+```
+
+#### Populate the Dockerfile with the command below
+```
+FROM alpine
+CMD ["echo", "Hello World!!"]
+```
+
+#### Build and run the image for verification purposes
+
+
+
+
+```
+nerdctl build --tag helloworld:v1.0 .
+nerdctl images | grep helloworld
+nerdctl run --rm helloworld:v1.0
+# Remove the image
+nerdctl rmi helloworld:v1.0
+```
+
+
+
+
+```
+docker build --tag helloworld:v1.0 .
+docker images | grep helloworld
+docker run --rm helloworld:v1.0
+# Remove the image
+docker rmi helloworld:v1.0
+```
+
+
+
+
+### Example#2 - Build Image & Deploy Container to Kubernetes
+
+Make sure that you switch the **Container Runtime** setting in the **Kubernetes Settings** panel to either `dockerd` or `containerd` as needed.
+
+#### Create a folder and add a sample index.html file as follows
+```
+mkdir nginx
+cd nginx
+echo "
Hello World from NGINX!!
" > index.html
+```
+
+#### Create a blank Dockerfile
+
+On Windows, Create a blank file named `Dockerfile`
+
+On Linux, You can use below command to create a blank `Dockerfile`
+
+```
+vi Dockerfile
+```
+
+#### Populate the Dockerfile with the command below
+```
+FROM nginx:alpine
+COPY . /usr/share/nginx/html
+```
+
+#### Build image from code locally
+
+:warning: **Note:** Please note that you need to pass the flag `--namespace k8s.io` to the `nerdctl` build command, so that `nerdctl` builds the image and then makes it available in the `k8s.io` namespace.
+
+
+
+
+```
+nerdctl --namespace k8s.io build --tag nginx-helloworld:latest .
+nerdctl --namespace k8s.io images | grep nginx-helloworld
+```
+
+
+
+
+```
+docker build --tag nginx-helloworld:latest .
+docker images | grep nginx-helloworld
+```
+
+
+
+#### Deploy to Kubernetes
+
+Run below command to create and run a pod using the image built in the previous step.
+
+:warning: **Note:** Please note that you need to pass the flag `--image-pull-policy=Never` to use a local image with `:latest` tag, as `:latest` tag will always try to pull the images from a remote repository.
+
+```
+kubectl run hello-world --image=nginx-helloworld:latest --image-pull-policy=Never --port=80
+kubectl port-forward pods/hello-world 8080:80
+```
+
+Point your web browser to `localhost:8080`, and you will see the message `Hello World from NGINX!!`. If you prefer to stay on the command line, use `curl localhost:8080`.
+
+#### Delete the pod and the image
+
+
+
+
+```
+kubectl delete pod hello-world
+# Remove the image
+nerdctl --namespace k8s.io rmi nginx-helloworld:latest
+```
+
+
+
+
+```
+kubectl delete pod hello-world
+# Remove the image
+docker rmi nginx-helloworld:latest
+```
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/increasing-open-file-limit.md b/versioned_docs/version-1.14/how-to-guides/increasing-open-file-limit.md
new file mode 100644
index 0000000000..6072662bee
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/increasing-open-file-limit.md
@@ -0,0 +1,77 @@
+---
+title: Increasing Open File Limit
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+You may wish to increase the open file limit as Rancher Desktop's default `ulimit` setting for pods may be too low, depending on your use case. This guide provides steps for increasing the open file limit using provisioning scripts alongside Rancher Desktop's internal processes.
+
+## macOS & Linux Steps
+
+First, use lima override.yaml to write the provisioning scripts.
+
+- Create `override.yaml` file at below path
+
+
+
+
+```
+~/Library/Application Support/rancher-desktop/lima/_config/override.yaml
+```
+
+
+
+
+```
+~/.local/share/rancher-desktop/lima/_config/override.yaml
+```
+
+
+
+
+You can then use the script below to increase the `ulimit` for containers inside your created `override.yaml` file.
+
+```
+provision:
+- mode: system
+ script: |
+ #!/bin/sh
+ cat <<'EOF' > /etc/security/limits.d/rancher-desktop.conf
+ * soft nofile 82920
+ * hard nofile 82920
+ EOF
+```
+
+If using the Elastic platform, please use the script below to set the `vm.max_map_count` parameter as well.
+
+```
+provision:
+- mode: system
+ script: |
+ #!/bin/sh
+ cat <<'EOF' > /etc/security/limits.d/rancher-desktop.conf
+ * soft nofile 82920
+ * hard nofile 82920
+ EOF
+ sysctl -w vm.max_map_count=262144
+```
+
+Lastly, please stop and restart Rancher Desktop in order for the updated limits to take effect.
+
+## Windows Steps
+
+First, be sure that you have run Rancher Desktop at least once in order for the configurations to initialize.
+
+You can then create a provisioning script, say `map_count.start`, at `%AppData%\rancher-desktop\provisioning` with the below code to update the open file limit by increasing the `max_map_count` parameter.
+
+```
+#!/bin/sh
+
+sysctl -w vm.max_map_count=262144
+```
+
+Lastly, please stop and restart Rancher Desktop for these changes to take effect.
diff --git a/versioned_docs/version-1.14/how-to-guides/installing-uninstalling-extensions.md b/versioned_docs/version-1.14/how-to-guides/installing-uninstalling-extensions.md
new file mode 100644
index 0000000000..985bbeee28
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/installing-uninstalling-extensions.md
@@ -0,0 +1,200 @@
+---
+title: Installing and Uninstalling Rancher Desktop Extensions
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+The **Extensions** feature introduced in the `v1.9.0-tech-preview` release enables you to use **Docker Desktop Extensions** within Rancher Desktop. The feature helps you extend Rancher Desktop's functionality to meet your additional needs. This guide will demonstrate how to install and uninstall Docker extensions in Rancher Desktop.
+
+### Prerequisites
+
+Rancher Desktop Extensions are available as part of release `v1.9.0-tech-preview` or later.
+
+### Installing Extensions
+
+There are two ways in which you can install extensions, a method using the UI and another using the `rdctl extension install` command.
+
+
+
+
+#### Using the UI
+
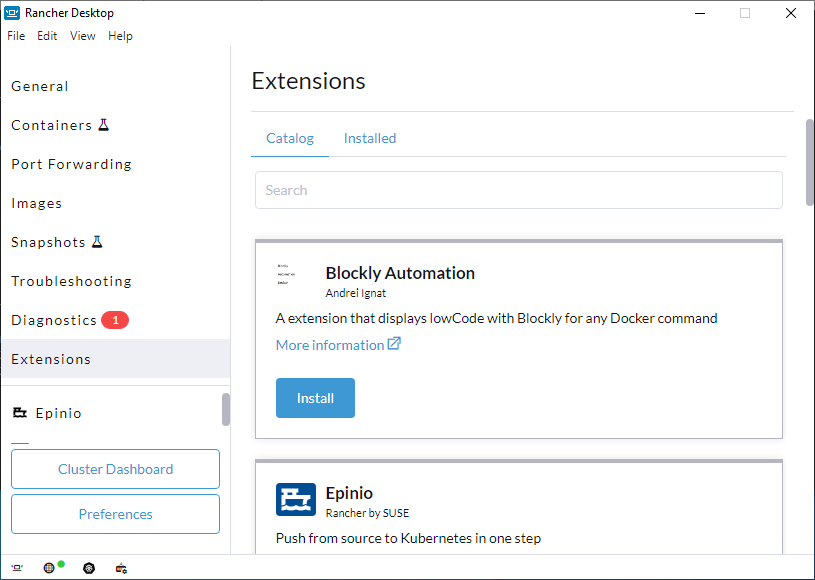
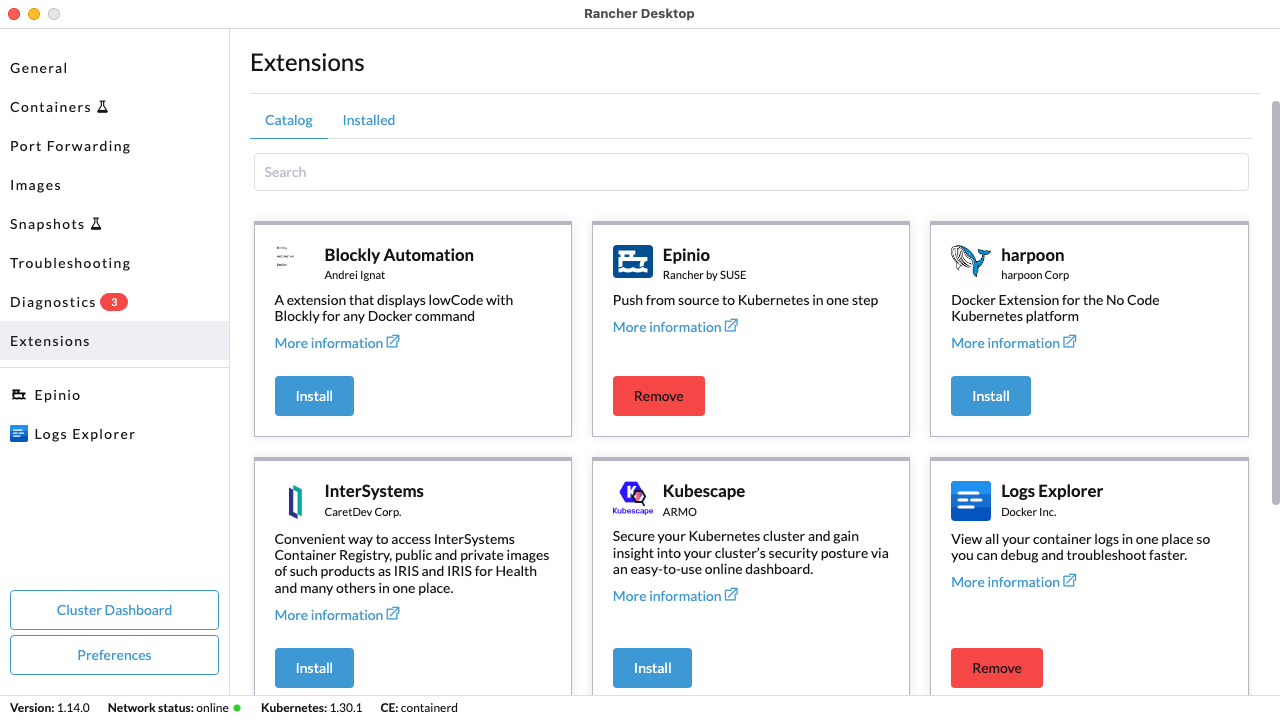
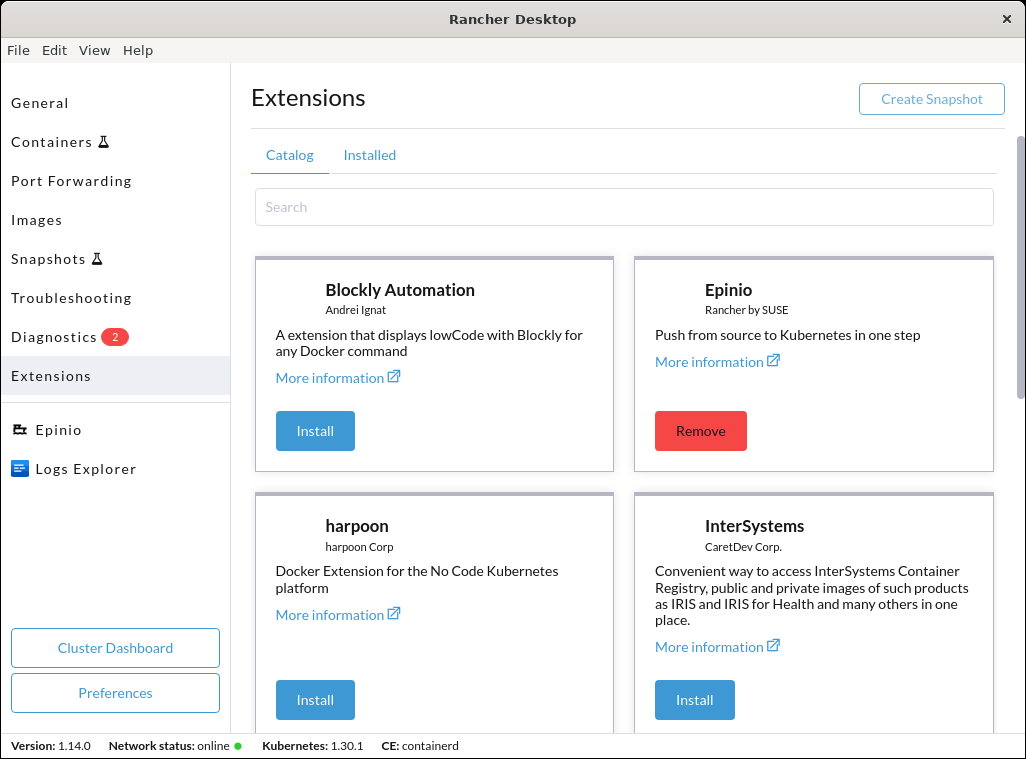
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to install extensions. Please use the command below to install extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension install :
+```
+
+
+
+
+#### Using the UI
+
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to install extensions. Please use the command below to install extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension install :
+```
+
+
+
+
+#### Using the UI
+
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to install extensions. Please use the command below to install extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension install :
+```
+
+
+
+
+### Uninstalling Extensions
+
+Additionally, there are two ways in which you can uninstall extensions, a method using the UI and another using the `rdctl extension uninstall` command.
+
+
+
+
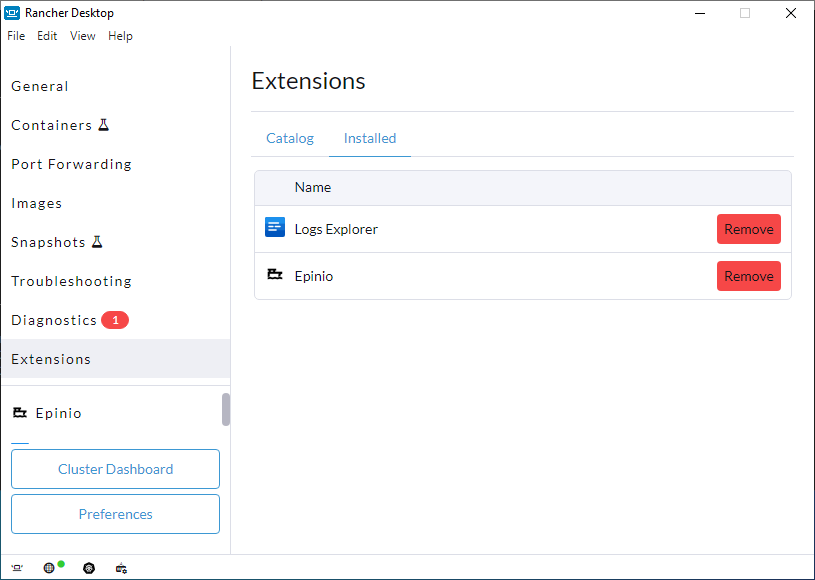
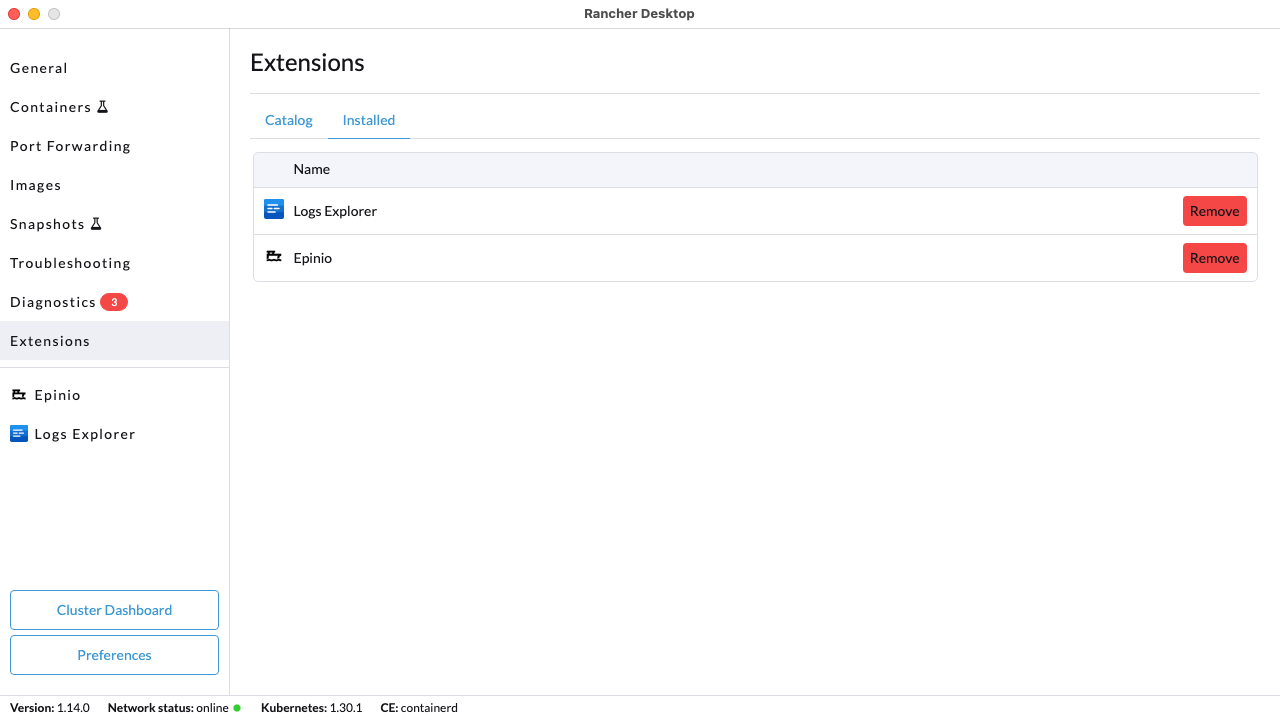
+#### Using the UI
+
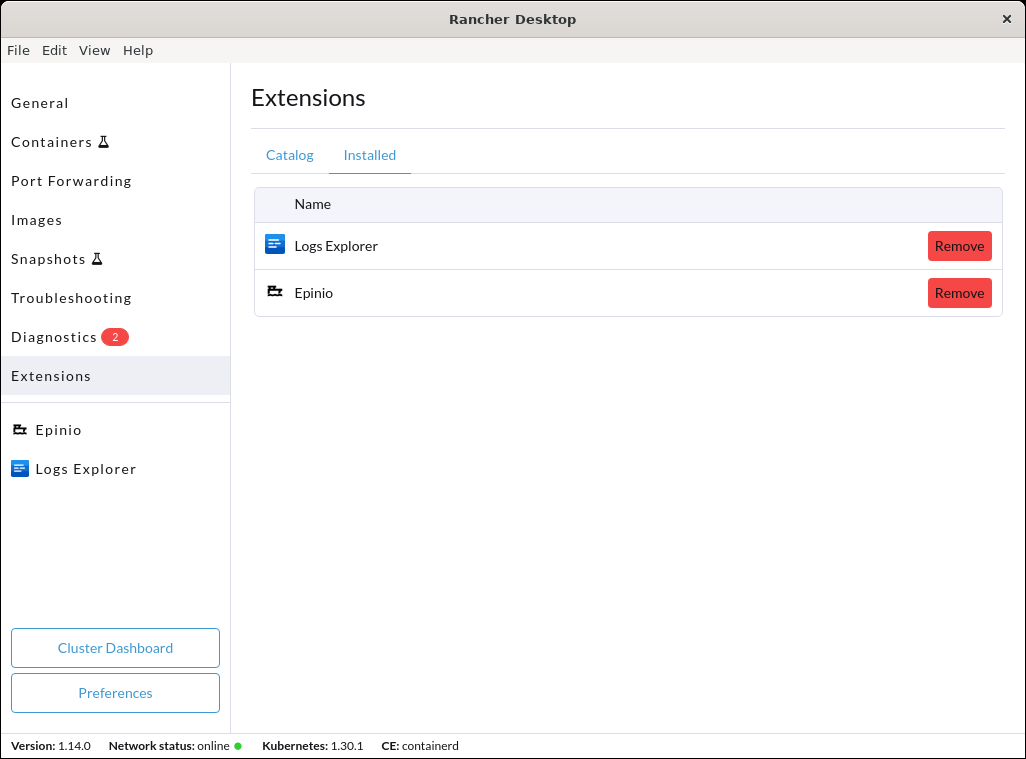
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. On this view, you can search through the available extensions, and uninstall the already installed extensions. Extensions can also be uninstalled from the **Installed** tab by clicking the **Remove** button.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to uninstall extensions. Please use the command below to uninstall extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension uninstall :
+```
+
+
+
+
+#### Using the UI
+
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. On this view, you can search through the available extensions, and uninstall the already installed extensions. Extensions can also be uninstalled from the **Installed** tab by clicking the **Remove** button.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to uninstall extensions. Please use the command below to uninstall extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension uninstall :
+```
+
+
+
+
+#### Using the UI
+
+Click **Extensions** from the main UI to navigate to the **Catalog** tab. On this view, you can search through the available extensions, and uninstall the already installed extensions. Extensions can also be uninstalled from the **Installed** tab by clicking the **Remove** button.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+#### Using the Command Line
+
+We have also extended the `rdctl` command line in the `v1.9.0-tech-preview` release to uninstall extensions. Please use the command below to uninstall extensions:
+
+:::note
+
+The use of the `` parameter is optional.
+
+:::
+
+```
+rdctl extension uninstall :
+```
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/mirror-private-registry.md b/versioned_docs/version-1.14/how-to-guides/mirror-private-registry.md
new file mode 100644
index 0000000000..5eb9b460da
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/mirror-private-registry.md
@@ -0,0 +1,112 @@
+---
+title: Mirroring Private Registries
+---
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+Rancher Desktop can be configured to mirror private registries using either container runtime (`containerd` or `dockerd`) via provisioning scripts or updating the registry file used by `k3s`. Please see the `k3s` documentation for further information on [private registry configuration](https://docs.k3s.io/installation/private-registry).
+
+
+
+
+Below is an example [provisioning script](../how-to-guides/provisioning-scripts.md#macOS--Linux) that can be used to mirror private registries.
+
+Check if you have the `override.yaml` file in the path below, otherwise you can create the file in the path with the suggested provisioning commands.
+
+Override File Path:
+`$HOME/.local/share/rancher-desktop/lima/_config/override.yaml`
+
+Example Script:
+```bash
+provision:
+ - mode: system
+ script: |
+ #!/bin/sh
+ set -eux
+ mkdir -p /etc/rancher/k3s
+ cat </etc/rancher/k3s/registries.yaml
+ mirrors:
+ ":5000":
+ endpoint:
+ - http://:5000
+ EOF
+```
+
+After restarting the application, you can verify the script being applied using the `rdctl shell` command below:
+
+```bash
+rdctl shell -- cat /etc/rancher/k3s/registries.yaml
+```
+
+
+
+
+Below is an example [provisioning script](../how-to-guides/provisioning-scripts.md#macOS--Linux) that can be used to mirror private registries.
+
+Check if you have the `override.yaml` file in the path below, otherwise you can create the file in the path with the suggested provisioning commands.
+
+Override File Path:
+`$HOME/Library/Application Support/rancher-desktop/lima/_config/override.yaml`
+
+Example Script:
+
+```bash
+provision:
+ - mode: system
+ script: |
+ #!/bin/sh
+ set -eux
+ mkdir -p /etc/rancher/k3s
+ cat </etc/rancher/k3s/registries.yaml
+ mirrors:
+ ":5000":
+ endpoint:
+ - http://:5000
+ EOF
+```
+
+After restarting the application, you can verify the script being applied using the `rdctl shell` command below:
+
+```bash
+rdctl shell -- cat /etc/rancher/k3s/registries.yaml
+```
+
+
+
+
+Ensure that you have initialized the application with a first run in order to create the `\provisioning\` directory. Once created, [provisioning scripts](../how-to-guides/provisioning-scripts.md#Windows) can be utilized to mirror private registries using a `.start` file.
+
+The file path and example provisioning script are provided below. After you have created the file with the appropriate configuration, restart the Rancher Desktop application for the provisioning script to take effect.
+
+`.start` File Path:
+`$HOME\AppData\Roaming\rancher-desktop\provisioning\mirror-registry.start`
+
+Example Script:
+
+```shell
+#!/bin/sh
+
+set -eux
+
+mkdir -p /etc/rancher/k3s
+
+cat </etc/rancher/k3s/registries.yaml
+mirrors:
+ "localhost:5000":
+ endpoint:
+ - http://localhost:5000
+EOF
+```
+
+Verify using the `rdctl shell` command below that the script is applied:
+
+```shell
+rdctl shell -- cat /etc/rancher/k3s/registries.yaml
+```
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/odo-rancher-desktop.md b/versioned_docs/version-1.14/how-to-guides/odo-rancher-desktop.md
new file mode 100644
index 0000000000..fff51a8afd
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/odo-rancher-desktop.md
@@ -0,0 +1,715 @@
+---
+title: ODO and Rancher Desktop
+---
+
+`odo` is a fast, iterative and straightforward CLI tool for developers who write, build, and deploy applications on Kubernetes. The `odo` CLI abstracts away complex Kubernetes concepts and allows developers to focus on iterating code. The helper tool can detect changes to local code and deploy them to a container orchestrated cluster automatically, giving instant feedback to validate changes in real-time. Please refer to the [`odo` project documentation](https://odo.dev/docs/introduction) to learn more.
+
+## Prerequisites
+
+For this guide you will use the [express-sample node.js application](https://github.com/rancher-sandbox/docs.rancherdesktop.io/tree/main/assets/express-sample) in the [Rancher Desktop documentation](https://github.com/rancher-sandbox/docs.rancherdesktop.io) repository as a way to demonstrate the use of `odo` and Rancher Desktop.
+
+:::note
+`odo` works with the `dockerd (moby)` runtime, be sure to have it selected from the preferences dialog location *Preferences* > *Container Engine* > *Allowed Images*.
+:::
+
+Please ensure that Kubernetes is enabled for your application. Additionally, in order to use `odo deploy`, you will need to be able to build and push an image to a Docker container registry. Log in using your Docker credentials as noted below:
+
+```shell
+$ docker login docker.io
+Username:
+Password:
+Login Succeeded!
+```
+
+### Installation
+
+Install `odo` by visiting https://odo.dev/docs/overview/installation and perform the appropriate install for your platform. The tool can be used both as a [CLI tool](https://odo.dev/docs/overview/installation#cli-installation) or an [IDE plugin](https://odo.dev/docs/overview/installation#ide-installation), as well as a few [alternative install methods](https://odo.dev/docs/overview/installation#alternative-installation-methods) depending on your preference. This guide will focus on using the tool through the CLI.
+
+## Steps: `odo init`
+
+This command will initialize the application by creating a `devfile.yaml` for deployments.
+
+1. Clone the [Rancher Desktop documentation](https://github.com/rancher-sandbox/docs.rancherdesktop.io) repository and change your directory to the [sample-express](https://github.com/rancher-sandbox/docs.rancherdesktop.io/tree/main/assets/express-sample) application.
+
+```shell
+git clone https://github.com/rancher-sandbox/docs.rancherdesktop.io.git
+cd docs.rancherdesktop.io/assets/express-sample
+```
+
+2. Before initializing, you must connect `odo` to your cluster via a namespace, which can be created with the command [`odo create namespace `](https://odo.dev/docs/command-reference/create-namespace):
+
+```shell
+odo create namespace odo-dev
+```
+
+
+Sample Output
+
+```shell
+$ odo create namespace odo-dev
+ ✓ Creating the namespace "odo-dev" [5ms]
+ ✓ Namespace "odo-dev" is ready for use
+ ✓ New namespace created and now using namespace: odo-dev
+```
+
+
+
+3. The command [`odo init`](https://odo.dev/docs/command-reference/init) will auto-detect your project framework and choose the appropriate `devfile.yaml` to be used for deployment of your application. The command will allow you to confirm the Devfile (Y/n), select a container to change configuration (choose none for this example), and enter a component name (e.g. my-nodejs-app).
+
+ Alternatively, the following command with the additional flags (e.g. `--devfile-version 2.2.0`) can be used to initialize `odo` and allow your application to be deployed:
+
+```shell
+odo init --name my-nodejs-app --devfile nodejs --devfile-registry DefaultDevfileRegistry --devfile-version 2.2.0
+```
+
+
+Sample Output
+
+```shell
+ __
+ / \__ Initializing a new component
+ \__/ \
+ / \__/ odo version: v3.13.0
+ \__/
+
+ ✓ Downloading devfile "nodejs:2.2.0" from registry "DefaultDevfileRegistry" [1s]
+
+Your new component 'my-nodejs-app' is ready in the current directory.
+To start editing your component, use 'odo dev' and open this folder in your favorite IDE.
+Changes will be directly reflected on the cluster.
+```
+
+
+
+```shell
+odo init
+```
+
+
+Sample Output
+
+```shell
+$ odo init
+ __
+ / \__ Initializing a new component
+ \__/ \ Files: Source code detected, a Devfile will be determined based upon source code autodetection
+ / \__/ odo version: v3.13.0
+ \__/
+
+Interactive mode enabled, please answer the following questions:
+ ✓ Determining a Devfile for the current directory [910ms]
+Based on the files in the current directory odo detected
+Language: JavaScript
+Project type: Node.js
+Application ports: 3000
+The devfile "nodejs:2.1.1" from the registry "DefaultDevfileRegistry" will be downloaded.
+? Is this correct? Yes
+ ✓ Downloading devfile "nodejs:2.1.1" from registry "DefaultDevfileRegistry" [933ms]
+
+↪ Container Configuration "runtime":
+ OPEN PORTS:
+ - 3000
+ - 5858
+ ENVIRONMENT VARIABLES:
+ - DEBUG_PORT = 5858
+
+? Select container for which you want to change configuration? NONE - configuration is correct
+? Enter component name: my-nodejs-app
+
+You can automate this command by executing:
+ odo init --name my-nodejs-app --devfile nodejs --devfile-registry DefaultDevfileRegistry --devfile-version 2.1.1
+
+Your new component 'my-nodejs-app' is ready in the current directory.
+To start editing your component, use 'odo dev' and open this folder in your favorite IDE.
+Changes will be directly reflected on the cluster.
+```
+
+
+
+## Steps: `odo dev`
+
+Now, you can run the command [`odo dev`](https://odo.dev/docs/command-reference/dev) to continuously deploy applications as you make changes to your code through your preferred IDE.
+
+:::caution
+You may run into an `ErrImagePull` error as the image may not be covered by Rancher Desktop's allowed images list. To resolve the error, please add the necessary image in *Preferences* > *Container Engine* > *Allowed Images* and hit apply to update allowed images immediately.
+:::
+
+```shell
+odo dev
+```
+
+
+Sample Output
+
+```shell
+$ odo dev
+ __
+ / \__ Developing using the "my-nodejs-app" Devfile
+ \__/ \ Namespace: odo-dev
+ / \__/ odo version: v3.13.0
+ \__/
+
+↪ Running on the cluster in Dev mode
+I0728 13:50:53.115137 92567 starterserver.go:123] API Server started at localhost:20000/api/v1
+ • Waiting for Kubernetes resources ...
+ ⚠ Pod is Pending
+ ✓ Pod is Running
+ ✓ Syncing files into the container [306ms]
+ ✓ Building your application in container (command: install) [3s]
+ • Executing the application (command: run) ...
+ ✓ Waiting for the application to be ready [1s]
+ - Forwarding from 127.0.0.1:20001 -> 3000
+
+
+↪ Dev mode
+ Status:
+ Watching for changes in the current directory /Users/docs.rancherdesktop.io/assets/express-sample
+
+ Keyboard Commands:
+[Ctrl+c] - Exit and delete resources from the cluster
+ [p] - Manually apply local changes to the application on the cluster
+```
+
+
+
+The `express-sample` application can now be accessed by the local port (127.0.0.1:20001). As an example, you can make a text change to the `index.jade` file in the *views* folder to see a real-time update to the application.
+
+## Steps: `odo deploy`
+
+This command will deploy your application to your cluster with instructions from your `devfile.yaml`.
+
+1. Be sure to be logged into the Docker container registry to push the application to, and set your container image build arguments to be the same as your container architecture using the [`ODO_IMAGE_BUILD_ARGS`](https://odo.dev/docs/overview/configure/#environment-variables-controlling-odo-behavior:~:text=ODO_IMAGE_BUILD_ARGS) environment variable:
+
+
+
+
+```shell
+export ODO_IMAGE_BUILD_ARGS="--platform=linux/amd64"
+```
+
+
+
+
+```shell
+export ODO_IMAGE_BUILD_ARGS="--platform=linux/arm64"
+```
+
+
+
+
+2. Update the `Dockerfile` in the `express-sample` directory to containerize the application with correct variables in order to build and push to a registry:
+
+
+Sample Dockerfile
+
+```shell
+# Install the app dependencies in a full SLE Node image
+FROM registry.suse.com/bci/nodejs:16
+
+# Copy package.json and package-lock.json
+COPY package*.json ./
+
+# Install app dependencies
+RUN npm install --production
+
+# Install app dependencies
+COPY . /opt/app-root/src
+
+ENV NODE_ENV production
+ENV PORT 3000
+
+CMD ["npm", "start"]
+```
+
+
+
+3. Modify the `devfile.yaml` to the example noted below for your container cluster.
+
+* Update the variables to access your container registry:
+
+```yaml
+# Add the following variables code anywhere in devfile.yaml
+# This MUST be a container registry you are able to access
+variables:
+ CONTAINER_IMAGE: docker.io//nodejs-odo-example
+ RESOURCE_NAME: my-nodejs-app
+ CONTAINER_PORT: "3000"
+ DOMAIN_NAME: nodejs.example.com
+```
+
+* Update the Devfile schema to `2.2.0` as `odo deploy` makes use of this version. Additionally, there is a command to initialize `odo` with the correct `schemaVersion: 2.2.0` noted above in the installation:
+
+```yaml
+# Deploy "kind" ID's use schema 2.2.0+
+schemaVersion: 2.2.0
+```
+
+* The commands seen below are used for deployment activities:
+
+
+Deployment Commands
+
+```yaml
+# This is the main "composite" command that will run all below commands
+commands:
+- id: deploy
+ composite:
+ commands:
+ - build-image
+ - k8s-deployment
+ - k8s-service
+ - k8s-url
+ group:
+ isDefault: true
+ kind: deploy
+
+# Below are the commands and their respective components that they are "linked" to deploy
+- id: build-image
+ apply:
+ component: outerloop-build
+- id: k8s-deployment
+ apply:
+ component: outerloop-deployment
+- id: k8s-service
+ apply:
+ component: outerloop-service
+- id: k8s-url
+ apply:
+ component: outerloop-url
+```
+
+
+
+* The commands seen below are used for adding the Docker image location, K8s deployment and services to `components`:
+
+
+Component Commands
+
+```yaml
+# This will build the container image before deployment
+- name: outerloop-build
+ image:
+ dockerfile:
+ buildContext: ${PROJECT_SOURCE}
+ rootRequired: false
+ uri: ./Dockerfile
+ imageName: "{{CONTAINER_IMAGE}}"
+# This will create a Deployment in order to run your container image across
+# the cluster.
+- name: outerloop-deployment
+ kubernetes:
+ inlined: |
+ kind: Deployment
+ apiVersion: apps/v1
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ replicas: 1
+ selector:
+ matchLabels:
+ app: {{RESOURCE_NAME}}
+ template:
+ metadata:
+ labels:
+ app: {{RESOURCE_NAME}}
+ spec:
+ containers:
+ - name: {{RESOURCE_NAME}}
+ image: {{CONTAINER_IMAGE}}
+ ports:
+ - name: http
+ containerPort: {{CONTAINER_PORT}}
+ protocol: TCP
+ resources:
+ limits:
+ memory: "1024Mi"
+ cpu: "500m"
+
+# This will create a Service so your Deployment is accessible.
+# Depending on your cluster, you may modify this code so it's a
+# NodePort, ClusterIP or a LoadBalancer service.
+- name: outerloop-service
+ kubernetes:
+ inlined: |
+ apiVersion: v1
+ kind: Service
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ ports:
+ - name: "{{CONTAINER_PORT}}"
+ port: {{CONTAINER_PORT}}
+ protocol: TCP
+ targetPort: {{CONTAINER_PORT}}
+ selector:
+ app: {{RESOURCE_NAME}}
+ type: NodePort
+```
+
+
+
+* The last addition to our Devfile is adding the Kubernetes ingress component as noted below:
+
+
+Ingress Commands
+
+```yaml
+- name: outerloop-url
+ kubernetes:
+ inlined: |
+ apiVersion: networking.k8s.io/v1
+ kind: Ingress
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ rules:
+ - host: "{{DOMAIN_NAME}}"
+ http:
+ paths:
+ - path: "/"
+ pathType: Prefix
+ backend:
+ service:
+ name: {{RESOURCE_NAME}}
+ port:
+ number: {{CONTAINER_PORT}}
+```
+
+
+
+* Below is the example `devfile.yaml` that you can use to help illustrate command and variable settings after they are all put together. Please review your Devfile to match or update the appropriate variables as noted below:
+
+
+Final Devfile
+
+```yaml
+commands:
+- exec:
+ commandLine: npm install
+ component: runtime
+ group:
+ isDefault: true
+ kind: build
+ workingDir: ${PROJECT_SOURCE}
+ id: install
+- exec:
+ commandLine: npm start
+ component: runtime
+ group:
+ isDefault: true
+ kind: run
+ workingDir: ${PROJECT_SOURCE}
+ id: run
+- exec:
+ commandLine: npm run debug
+ component: runtime
+ group:
+ isDefault: true
+ kind: debug
+ workingDir: ${PROJECT_SOURCE}
+ id: debug
+- exec:
+ commandLine: npm test
+ component: runtime
+ group:
+ isDefault: true
+ kind: test
+ workingDir: ${PROJECT_SOURCE}
+ id: test
+# This is the main "composite" command that will run all below commands
+- id: deploy
+ composite:
+ commands:
+ - build-image
+ - k8s-deployment
+ - k8s-service
+ - k8s-url
+ group:
+ isDefault: true
+ kind: deploy
+# Below are the commands and their respective components that they are "linked" to deploy
+- id: build-image
+ apply:
+ component: outerloop-build
+- id: k8s-deployment
+ apply:
+ component: outerloop-deployment
+- id: k8s-service
+ apply:
+ component: outerloop-service
+- id: k8s-url
+ apply:
+ component: outerloop-url
+components:
+- container:
+ args:
+ - tail
+ - -f
+ - /dev/null
+ endpoints:
+ - name: http-node
+ targetPort: 3000
+ - exposure: none
+ name: debug
+ targetPort: 5858
+ env:
+ - name: DEBUG_PORT
+ value: "5858"
+ image: registry.suse.com/bci/nodejs:16:latest
+ memoryLimit: 1024Mi
+ mountSources: true
+ name: runtime
+# This will build the container image before deployment
+- name: outerloop-build
+ image:
+ dockerfile:
+ buildContext: ${PROJECT_SOURCE}
+ rootRequired: false
+ uri: ./Dockerfile
+ imageName: "{{CONTAINER_IMAGE}}"
+# This will create a Deployment in order to run your container image across
+# the cluster.
+- name: outerloop-deployment
+ kubernetes:
+ inlined: |
+ kind: Deployment
+ apiVersion: apps/v1
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ replicas: 1
+ selector:
+ matchLabels:
+ app: {{RESOURCE_NAME}}
+ template:
+ metadata:
+ labels:
+ app: {{RESOURCE_NAME}}
+ spec:
+ containers:
+ - name: {{RESOURCE_NAME}}
+ image: {{CONTAINER_IMAGE}}
+ ports:
+ - name: http
+ containerPort: {{CONTAINER_PORT}}
+ protocol: TCP
+ resources:
+ limits:
+ memory: "1024Mi"
+ cpu: "500m"
+
+# This will create a Service so your Deployment is accessible.
+# Depending on your cluster, you may modify this code so it's a
+# NodePort, ClusterIP or a LoadBalancer service.
+- name: outerloop-service
+ kubernetes:
+ inlined: |
+ apiVersion: v1
+ kind: Service
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ ports:
+ - name: "{{CONTAINER_PORT}}"
+ port: {{CONTAINER_PORT}}
+ protocol: TCP
+ targetPort: {{CONTAINER_PORT}}
+ selector:
+ app: {{RESOURCE_NAME}}
+ type: NodePort
+- name: outerloop-url
+ kubernetes:
+ inlined: |
+ apiVersion: networking.k8s.io/v1
+ kind: Ingress
+ metadata:
+ name: {{RESOURCE_NAME}}
+ spec:
+ rules:
+ - host: "{{DOMAIN_NAME}}"
+ http:
+ paths:
+ - path: "/"
+ pathType: Prefix
+ backend:
+ service:
+ name: {{RESOURCE_NAME}}
+ port:
+ number: {{CONTAINER_PORT}}
+metadata:
+ description: Stack with Node.js 16
+ displayName: Node.js Runtime
+ icon: https://nodejs.org/static/images/logos/nodejs-new-pantone-black.svg
+ language: JavaScript
+ name: my-node-app
+ projectType: Node.js
+ tags:
+ - Node.js
+ - Express
+ - ubi8
+ version: 2.1.1
+schemaVersion: 2.2.0
+starterProjects:
+- git:
+ remotes:
+ origin: https://github.com/odo-devfiles/nodejs-ex.git
+ name: nodejs-starter
+# Add the following variables code anywhere in devfile.yaml
+# This MUST be a container registry you are able to access
+variables:
+ CONTAINER_IMAGE: docker.io//node-odo-example
+ RESOURCE_NAME: my-node-app
+ CONTAINER_PORT: "3000"
+ DOMAIN_NAME: node.example.com
+ ```
+
+
+
+4. Now, you can run the command [`odo deploy`](https://odo.dev/docs/command-reference/deploy) to deploy the application to the cluster:
+
+:::caution
+You may run into an `unauthorized: image` error as the image may not be covered by Rancher Desktop's allowed images list. To resolve the error, please add the necessary image in *Preferences* > *Container Engine* > *Allowed Images* and hit apply to update allowed images immediately.
+:::
+
+
+Sample Output
+
+```shell
+$ odo deploy
+ __
+ / \__ Running the application in Deploy mode using my-node-app Devfile
+ \__/ \ Namespace: odo-dev
+ / \__/ odo version: v3.13.0
+ \__/
+
+↪ Building & Pushing Image: docker.io/arjsin/nodejs-odo-example
+ • Building image locally ...
+[+] Building 2.7s (9/9) FINISHED
+ => [internal] load build definition from Dockerfile 0.0s
+ => => transferring dockerfile: 405B 0.0s
+ => [internal] load .dockerignore 0.0s
+ => => transferring context: 364B 0.0s
+ => [internal] load metadata for registry.suse.com/bci/nodejs:16 2.2s
+ => [1/4] FROM registry.suse.com/bci/nodejs:16@sha256:dda0e616a0fcb3dc589 0.0s
+ => [internal] load build context 0.0s
+ => => transferring context: 5.14kB 0.0s
+ => CACHED [2/4] COPY package*.json ./ 0.0s
+ => CACHED [3/4] RUN npm install --production 0.0s
+ => [4/4] COPY . /opt/app-root/src 0.0s
+ => exporting to image 0.4s
+ => => exporting layers 0.4s
+ => => writing image sha256:c6d3ed7d9fb4736d3c4e95b54054533f79d64d3a01e65 0.0s
+ => => naming to docker.io/arjsin/nodejs-odo-example 0.0s
+ ✓ Building image locally [3s]
+ • Pushing image to container registry ...
+Using default tag: latest
+The push refers to repository [docker.io/arjsin/nodejs-odo-example]
+20658d9b13ba: Pushed
+7b1ee26c3aea: Pushed
+067890bef08d: Pushed
+d08e96dfc7bc: Pushed
+174c0e293bd0: Pushed
+latest: digest: sha256:ca598fc0c5278e8d00cba41e14914f1d3f7a3561bd4a324f2ffcd33b166135ad size: 1368
+ ✓ Pushing image to container registry [30s]
+
+↪ Deploying Kubernetes Component: my-node-app
+ ✓ Creating resource Deployment/my-node-app
+
+↪ Deploying Kubernetes Component: my-node-app
+ ✓ Creating resource Service/my-node-app
+
+↪ Deploying Kubernetes Component: my-node-app
+ ✓ Creating resource Ingress/my-node-app
+
+Your Devfile has been successfully deployed
+```
+
+
+
+### Steps: `odo describe component`
+
+Now, the command [`odo describe component`](https://odo.dev/docs/command-reference/describe-component) can be used to view information from the Devfile such as Kubernetes components, ingresses, and the URL to access the application:
+
+```shell
+odo describe component
+```
+
+
+Sample Output
+
+```shell
+$ odo describe component
+Name: my-nodejs-app
+Display Name: Node.js Runtime
+Project Type: Node.js
+Language: JavaScript
+Version: 2.2.0
+Description: Node.js 18 application
+Tags: Node.js, Express, ubi8
+
+Running in: None
+
+Supported odo features:
+ • Dev: true
+ • Deploy: false
+ • Debug: true
+
+Commands:
+ • install
+ Type: exec
+ Group: build
+ Command Line: "npm install"
+ Component: runtime
+ Component Type: container
+ • run
+ Type: exec
+ Group: run
+ Command Line: "npm start"
+ Component: runtime
+ Component Type: container
+ • debug
+ Type: exec
+ Group: debug
+ Command Line: "npm run debug"
+ Component: runtime
+ Component Type: container
+ • test
+ Type: exec
+ Group: test
+ Command Line: "npm test"
+ Component: runtime
+ Component Type: container
+
+Container components:
+ • runtime
+ Source Mapping: /projects
+```
+
+
+
+## Steps: `odo delete component`
+
+After you have completed testing, you can free the resources used by `odo` by using the command [`odo delete component`](https://odo.dev/docs/command-reference/delete-component):
+
+```shell
+odo delete component
+```
+
+
+Sample Output
+
+```shell
+$ odo delete component
+Searching resources to delete, please wait...
+This will delete "my-node-app" from the namespace "odo-dev".
+ • The following resources will get deleted from cluster:
+ • - Deployment: my-node-app
+ • - Service: my-node-app
+ • - Ingress: my-node-app
+
+? Are you sure you want to delete "my-node-app" and all its resources? Yes
+ ✓ Deleting resources from cluster [52ms]
+The component "my-node-app" is successfully deleted from namespace "odo-dev"
+```
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/provisioning-scripts.md b/versioned_docs/version-1.14/how-to-guides/provisioning-scripts.md
new file mode 100644
index 0000000000..1c43356602
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/provisioning-scripts.md
@@ -0,0 +1,107 @@
+---
+title: Provisioning Scripts
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Provisioning scripts can be used to override some of Rancher Desktop's internal processes. For example, scripts can be used to provide certain command line parameters to K3s, add additional mounts, increase ulimit value etc. This guide will explain how to set up your provisioning scripts for macOS, Linux, and Windows.
+
+## macOS & Linux
+
+On macOS and Linux, you can use lima override.yaml to write provisioning scripts.
+
+- Run Rancher Desktop at least once to allow it to create the `_config` directory.
+
+:::note
+Please note that the directory will be deleted during a factory-reset, so ensure a backup for your provisioning scripts in case you need them after a factory-reset.
+:::
+
+- Create `override.yaml` file at below path
+
+
+
+
+```
+~/Library/Application Support/rancher-desktop/lima/_config/override.yaml
+```
+
+
+
+
+```
+~/.local/share/rancher-desktop/lima/_config/override.yaml
+```
+
+
+
+
+- Write a provisioning script in the `override.yaml` file created in the previous step. For example, you can use the below script to increase ulimit for containers.
+
+```
+provision:
+- mode: system
+ script: |
+ #!/bin/sh
+ cat <<'EOF' > /etc/security/limits.d/rancher-desktop.conf
+ * soft nofile 82920
+ * hard nofile 82920
+ EOF
+```
+
+- You can also use `override.yaml` to override/modify a lima configuration setting, for example, to create additional mounts as shown below.
+
+```
+mounts:
+ - location: /some/path
+ writable: true
+```
+
+- Another example uses the `override.yaml` file to allow users to implement custom settings for [`K3s`](https://k3s.io/?ref=traefik.io) environments using Rancher Desktop's `K3S_EXEC` syntax (Similar to the `K3s` syntax [`INSTALL_K3S_EXEC`](https://docs.k3s.io/reference/env-variables#:~:text=as%20the%20default.-,INSTALL_K3S_EXEC,-Command%20with%20flags)). Please see the [agent](https://docs.k3s.io/cli/agent) and [server](https://docs.k3s.io/cli/server) command line flags documentation for further installation options. Below is an example setting using the [`--tls-san value`](https://docs.k3s.io/cli/server#:~:text=of%20the%20cluster-,%2D%2Dtls%2Dsan%20value,-N/A) flag to add additional hostnames as Subject Alternative Names on the TLS certification:
+
+```
+env:
+ K3S_EXEC: --tls-san value
+```
+
+## Windows
+
+**Caution:** You can only utilize these provisioning scripts for Rancher Desktop, version 1.1.0 or later, on Windows.
+
+- Run Rancher Desktop at least once to allow it to create the configuration `provisioning` directory.
+
+:::note
+Please note that the directory will be deleted during a factory-reset, so ensure a backup for your provisioning scripts in case you need them after factory-reset.
+:::
+
+- Open the `%LOCALAPPDATA%\rancher-desktop\provisioning` directory. An example of the full path: `C:\Users\Joe\AppData\Local\rancher-desktop\provisioning`.
+
+- Note that any files with a file extension of `.start`, such as `k3s-overrides.start`, can be executed when _Rancher Desktop starts its Kubernetes backend_ (if enabled). Such files will run within the Rancher Desktop WSL context.
+
+Example flow for `.start` files:
+- Rancher Desktop internal setup
+- Run provisioning scripts
+- Enable `dockerd` or `containerd` in the UI
+- Kubernetes (K3s)
+
+As an example, using `%LOCALAPPDATA%\rancher-desktop\provisioning\insecure-registry.start` will allow `nerdctl` to use insecure registries by default:
+
+```
+#!/bin/sh
+
+mkdir -p /etc/nerdctl
+cat > /etc/nerdctl/nerdctl.toml <
+
+
+
+While [Rancher](https://rancher.com/) and [Rancher Desktop](https://rancherdesktop.io/) share the _Rancher_ name, they do different things. Rancher Desktop is not Rancher on the Desktop. Rancher is a powerful solution to manage Kubernetes clusters. Rancher Desktop runs local Kubernetes and a container management platform. The two solutions complement each other. For example, you can install Rancher as a workload in Rancher Desktop.
+
+This guide outlines steps to install Rancher Dashboard on Rancher Desktop using `container runtime` or `helm` (local environment):
+
+**Note:** You may encounter issues if the supporting utilities (ex: helm), or your workload versions are incompatible with the Kubernetes version in your session. As a potential fix, you can switch to a compatible Kubernetes version via the [Preferences > Kubernetes](../ui/preferences/kubernetes.md) dialog. Supported Kubernetes platforms for Rancher are available on the [support matrix page](https://www.suse.com/suse-rancher/support-matrix/all-supported-versions/rancher-v2-7-1/).
+
+
+
+
+```console
+nerdctl run --privileged -d --restart=always -p 8080:80 -p 8443:443 rancher/rancher
+```
+
+
+
+
+```console
+docker run --privileged -d --restart=always -p 8080:80 -p 8443:443 rancher/rancher
+```
+
+
+
+
+1: Add Jetstack charts:
+```console
+helm repo add jetstack https://charts.jetstack.io
+```
+
+2: Add latest Rancher charts:
+```console
+helm repo add rancher-latest https://releases.rancher.com/server-charts/latest
+```
+
+3: Create cert-manager namespace:
+```console
+kubectl create namespace cert-manager
+```
+
+4: Install cert-manager services:
+```console
+helm install cert-manager jetstack/cert-manager --namespace cert-manager --version v1.7.1 --set installCRDs=true
+```
+
+5: Apply CRDs:
+```console
+kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.7.1/cert-manager.crds.yaml
+```
+
+6: Create cattle-system namespace:
+```console
+kubectl create namespace cattle-system
+```
+
+7: Install Rancher application:
+```console
+helm install rancher rancher-latest/rancher --namespace cattle-system --set hostname=rancher.rd.localhost --wait --timeout=10m
+```
+
+
+
+
+The installation takes a few minutes to complete. After the installation, you can access the Rancher UI as follows:
+* Installed through `container runtime`: [https://localhost:8443/](https://localhost:8443/)
+* Installed through `helm` [https://rancher.rd.localhost/](https://rancher.rd.localhost/)
+
+
+
+
+
+
+
+In order to access the Rancher UI, you need to get the Bootstrap Password:
+
+1: Get Rancher UI container ID/Name:
+```console
+nerdctl ps
+```
+2: Get the Bootstrap Password:
+```console
+nerdctl logs [rancherContainerID] 2>&1 | grep "Bootstrap Password:"
+```
+3: Bootstrap Password example:
+```console
+[INFO] Bootstrap Password: 7fwjjw4ldcmnq8ghns22q7nhl5lrznwwt9p9vjljfjc6tqbcvhxmwq
+```
+
+
+
+
+In order to access the Rancher UI, you need to get the Bootstrap Password:
+
+1: Get Rancher UI container ID/Name:
+```console
+docker ps
+```
+2: Get the Bootstrap Password:
+```console
+docker logs [rancherContainerID] 2>&1 | grep "Bootstrap Password:"
+```
+3: Bootstrap Password example:
+```console
+[INFO] Bootstrap Password: 7fwjjw4ldcmnq8ghns22q7nhl5lrznwwt9p9vjljfjc6tqbcvhxmwq
+```
+
+
+
+Follow the wizard instructions and click on `Continue` to land on the main Rancher UI page.
+
+
+
+From the Rancher UI, you can manage your local cluster, node, and more. For more information, see [Rancher Docs](https://ranchermanager.docs.rancher.com/).
diff --git a/versioned_docs/version-1.14/how-to-guides/running-air-gapped.md b/versioned_docs/version-1.14/how-to-guides/running-air-gapped.md
new file mode 100644
index 0000000000..72dcb5c948
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/running-air-gapped.md
@@ -0,0 +1,171 @@
+---
+title: Running When Offline
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Rancher Desktop can be run when offline, aka in air-gapped mode. This document covers requirements
+and possible problems when running in air-gapped mode.
+
+### A Note for Windows users
+
+This document uses Powershell syntax for environment variables. If you're using the Command shell
+instead, where you see an environment variable reference of `$env:FOO`, please substitute it with `%FOO%`.
+
+### Network-Sensitive areas
+
+There are two areas where Rancher Desktop assumes network availability and will recover in an air-gapped situation:
+
+1. Pulling Kubernetes `k3s` images into the `k3s` cache directory
+
+2. Using `kuberlr` as a version-aware wrapper around `kubectl`, so the client never differs from the Kubernetes server by more than one minor version.
+
+### Existing Deployments
+
+If Rancher Desktop has been installed on a machine initially with networked access, it can
+be run subsequently on that machine after network connectivity has been turned off. The main
+difference in core functionality is that the list of versions of Kubernetes available in drop-down menus
+is limited to those versions that have actually been downloaded and stored in the cache.
+
+There is a problem using the `kubectl` client, because of the `kuberlr` wrapper (Windows users should add the `.exe` suffix to each executable utility file).
+
+In this case, we're discussing a system that was initialized when connected to the internet, but we're about
+to take the machine offline for future use.
+
+Suppose there are three versions of `k3s` in the `rancher-desktop` cache.
+
+- 1.24.3
+
+- 1.21.14
+
+- 1.19.16
+
+But suppose that on this system we only ran `kubectl` when using versions `1.24.3` and `1.21.14`. This means that
+the `~/.kuberlr/PLATFORM-ARCH/` directory (`$env:HOMEDRIVE%\$env:HOMEPATH/.kuberlr/windows-amd64` on Windows) will contain only two files:
+
+- kubectl1.24.3
+
+- kubectl1.21.14
+
+If we go offline and use the UI to switch to Kubernetes `1.19.16`, when `kubectl` is run, the system will fail.
+The problem is that `kubectl` is an alias for `kuberlr`, which will try to download `kubectl 1.19.16` and install it
+in the `.kuberlr` directory, but won't be able to access it.
+
+So in this case, it would be best to prepare a connected system for disconnecting by selecting each available version of
+Kubernetes currently in the cache, and running `kubectl --context rancher-desktop cluster-info` to ensure that an appropriate
+version of the `kubectl` client is installed.
+
+You _could_ install versioned `kubectl`s manually. This is covered in the next section.
+
+### Preparing an Air-Gapped System
+
+Here we assume you have some kind of removable media which you can populate on an internet-connected system, and then move over to the air-gapped system.
+
+There are two directories that need to be populated in order for Rancher Desktop to function off-line:
+
+#### The Cache Directory
+
+To populate a source disk (which we refer to here as `%SOURCEDISK%`, although it is probably some kind of removable medium like a USB thumb drive), you need the following files:
+
+* `k3s-versions.json` -- this file is created by Rancher Desktop. It reads a raw JSON file from `https://update.k3s.io/v1-release/channels` and converts it into a different kind of JSON file. Currently there is no utility to do that conversion; the easiest way to get this file is to run Rancher Desktop on a connected system and save the `CACHE/k3s-versions.json` file (see below for where `CACHE` exists on different platforms).
+* Tar archives of Kubernetes K3s images. These are listed at https://github.com/k3s-io/k3s/releases. You'll want to download either the `k3s-airgap-images-amd64.tar` for AMD/Intel machines, `k3s-airgap-images-arm64.tar` for M1 machines, or the respective `*.tar.zst` compressed tarball if you are using `k3s` v1.26.1 and above. Finally you'll need to download the `k3s` executable for the selected version. For example, the following commands will let you work with K3s v1.24.3 build 1 offline:
+
+```
+cd .../CACHE
+mkdir v1.24.3+k3s1
+cd v1.24.3+k3s1
+wget https://github.com/k3s-io/k3s/releases/download/v1.24.3%2Bk3s1/k3s-airgap-images-amd64.tar
+wget https://github.com/k3s-io/k3s/releases/download/v1.24.3%2Bk3s1/sha256sum-amd64.txt
+wget https://github.com/k3s-io/k3s/releases/download/v1.24.3%2Bk3s1/k3s
+```
+
+
+
+
+On Windows, the cache directory is at `$env:HOMEDRIVE%\$env:HOMEPATH\AppData\Local\rancher-desktop\cache\k3s`, and can be created with the command
+
+```
+mkdir -Force $env:HOMEDRIVE%\$env:HOMEPATH\AppData\Local\rancher-desktop\cache\k3s
+```
+
+Assuming you have some source media, you would also run the following commands to pre-populate the cache:
+
+```
+copy-item -Force $env:SOURCEDISK\k3s-versions.json $env:HOMEDRIVE%\$env:HOMEPATH\AppData\Local\rancher-desktop\cache\
+copy-item -Recurse -Force $env:SOURCEDISK\v..+k3s $env:HOMEDRIVE%\$env:HOMEPATH\AppData\Local\rancher-desktop\cache\k3s\
+```
+
+
+
+
+On macOS, the cache directory is at `$HOME/Library/Caches/rancher-desktop` and the commands to populate it would be
+
+```
+CACHEDIR=$HOME/Library/Caches/rancher-desktop
+mkdir -p $CACHEDIR/k3s
+cp $SOURCEDISK/k3s-versions.json $CACHEDIR/
+cp -r $SOURCEDISK/v..+k3s $CACHEDIR/k3s/
+```
+
+
+
+
+On Linux, the cache directory is at `$HOME/.cache/rancher-desktop` and the commands to populate it would be
+
+```
+CACHEDIR=$HOME/.cache/rancher-desktop
+mkdir -p $CACHEDIR/k3s
+cp $SOURCEDISK/k3s-versions.json $CACHEDIR/
+cp -r $SOURCEDISK/v..+k3s $CACHEDIR/k3s/
+```
+
+
+
+
+#### The kuberlr Directory
+
+The location of this directory is more straightforward. On all platforms, it's at `HOME/.kuberlr/PLATFORM-ARCH` where:
+
+- `HOME` is the home directory: usually `$env:HOMEDRIVE%\$env:HOMEPATH` on Windows, and `~` or `$HOME` on macOS and Linux.
+- `PLATFORM` is one of `windows`, `linux`, or `darwin`.
+- `ARCH` is `aarch64` on M1 machines, and `amd64` everywhere else.
+
+To populate it, determine which versions of Kubernetes you'll be using, and download the appropriate executables from the internet. These would be in:
+
+
+
+
+`https://dl.k8s.io/VERSION/bin/PLATFORM/CPU/kubectl.exe`
+
+
+
+
+`https://dl.k8s.io/VERSION/bin/PLATFORM/CPU/kubectl`
+
+
+
+
+`https://dl.k8s.io/VERSION/bin/PLATFORM/CPU/kubectl`
+
+
+
+
+Where:
+
+- `VERSION` will have the form `vMAJOR.MINOR.PATCH` (like `v1.22.1`),
+- `PLATFORM` will be one of `darwin`, `linux`, or `windows`,
+- `CPU` will `arm64` on M1 machines and `amd64` everywhere else.
+
+For example, to get a kubectl for Windows that will work with Kubernetes v1.22, this Windows command-shell (not PowerShell) command will put it on the `SOURCEDISK`:
+
+```
+wget -O %SOURCEDISK/kubectl1.22.1.exe https://dl.k8s.io/v1.22.1/bin/windows/amd64/kubectl.exe
+```
+
+##### A Note on Versions
+
+Kubectl clients are guaranteed to work with servers that are running the same MAJOR version and differ in the MINOR version by at most 1. So for example, if your organization is working with Kubernetes versions v1.21.x, v1.22.x, and v1.23.x, for any patch-version of `x`, you would only need to install `kubectl1.22.x` in the `.kuberlr` directory. But if you copy a `v1.24.x` of Kubernetes into the `CACHE` directory, you'll need to ensure there's a compatible `kubectl` in the `.kuberlr` directory as well (any of `v1.23.x`, `v1.24.x`, or `v1.25.x` would suffice).
diff --git a/versioned_docs/version-1.14/how-to-guides/setup-NGINX-Ingress-Controller.md b/versioned_docs/version-1.14/how-to-guides/setup-NGINX-Ingress-Controller.md
new file mode 100644
index 0000000000..ec395ace39
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/setup-NGINX-Ingress-Controller.md
@@ -0,0 +1,61 @@
+---
+title: Setup NGINX Ingress Controller
+---
+
+
+
+
+
+Rancher Desktop uses K3s under the hood, which in turn uses Traefik as the default ingress controller for your Kubernetes cluster. However, there are unique use cases where NGINX may be required or preferred. Below steps show how to use NGINX Ingress controller for a sample deployment.
+
+### Steps
+
+1. Uncheck `Enable Traefik` from the `Kubernetes Settings` page to disable Traefik. You may need to exit and restart Rancher Desktop for the change to take effect.
+
+2. Deploy the NGINX ingress controller via `helm` or `kubectl`.
+
+
+
+
+```
+helm upgrade --install ingress-nginx ingress-nginx \
+ --repo https://kubernetes.github.io/ingress-nginx \
+ --namespace ingress-nginx --create-namespace
+```
+
+
+
+
+```
+kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.1.2/deploy/static/provider/cloud/deploy.yaml
+```
+
+
+
+
+3. Wait for the ingress pods to come up and running.
+
+```
+kubectl get pods --namespace=ingress-nginx
+```
+
+4. Create a sample deployment and the associated service.
+
+```
+kubectl create deployment demo --image=nginx --port=80
+kubectl expose deployment demo
+```
+
+5. Create an ingress resource. The following command uses a host that maps to localhost.
+
+```
+kubectl create ingress demo-localhost --class=nginx --rule="demo.localdev.me/*=demo:80"
+```
+
+6. Forward a local port to the ingress controller.
+
+```
+kubectl port-forward --namespace=ingress-nginx service/ingress-nginx-controller 8080:80
+```
+
+If you access http://demo.localdev.me:8080/, you should see NGINX Welcome page.
diff --git a/versioned_docs/version-1.14/how-to-guides/skaffold-and-rancher-desktop.md b/versioned_docs/version-1.14/how-to-guides/skaffold-and-rancher-desktop.md
new file mode 100644
index 0000000000..42ba8059fe
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/skaffold-and-rancher-desktop.md
@@ -0,0 +1,79 @@
+---
+title: Skaffold and Rancher Desktop
+---
+
+
+
+
+
+Skaffold is a command line tool that facilitates continuous development for Kubernetes-native applications. Skaffold handles the workflow for building, pushing, and deploying your application, and it provides building blocks for creating CI/CD pipelines. This enables you to focus on iterating on your application locally while Skaffold continuously deploys to your local or remote Kubernetes cluster. To learn more about Skaffold, refer to the project docs [here](https://skaffold.dev/docs/).
+
+In order to demonstrate the steps to set up Skaffold with Rancher Desktop, a sample nodejs app example is provided within the Rancher Desktop docs repository [here](https://github.com/rancher-sandbox/docs.rancherdesktop.io/tree/main/assets/express-sample).
+
+>**Important: Skaffold only works with `dockerd` (Moby).** Therefore, make sure to select your runtime as `dockerd` from the **Kubernetes Settings** panel in the Rancher Desktop UI.
+
+1. Visit https://skaffold.dev/docs/install/ to install Skaffold.
+
+1. Clone the [Rancher Desktop docs repository](https://github.com/rancher-sandbox/docs.rancherdesktop.io.git) and navigate to the `express-sample` in a terminal as follows:
+ ```
+ cd docs.rancherdesktop.io/assets/express-sample
+ ```
+
+1. Run `skaffold init`.
+
+ Per the [Skaffold docs](https://skaffold.dev/docs/pipeline-stages/init/#build-config-initialization),`skaffold init` walks through your project directory and looks for any build configuration files such as `Dockerfile`, `build.gradle/pom.xml`, `package.json`, `requirements.txt`, or `go.mod`.
+
+ We will select `Dockerfile` and `package.json` in our example. This will generate the initial configuration file that you can modify as needed. When prompted, select `yes` to write your config to `skaffold.yaml`.
+
+1. In your editor, review your `app.js` and `manifests.yaml` files. Note that in `manifests.yaml`, you will have a deployment config as well as a service config. It is only necessary to have 1 `replica` for testing purposes.
+
+1. Back in your terminal, you'll notice that you will have two options: `skaffold run` that lets you build and deploy, and `skaffold dev` that allows you to enter development mode with auto-redeploy. We will use `skaffold dev` in this example.
+
+ You will need to have push access to the image repository. You can either use your docker login, set up a local registry, or build locally without pushing to an image registry:
+
+
+
+
+ Before running `skaffold dev`, use your docker login if you have a [Docker Hub](https://hub.docker.com/) account. Then, in the files `skaffold.yaml` and `manifests.yaml` replace `matamagu/express-sample` for `YOUR_DOCKER_HUB_USERNAME/express-sample` as `skaffold dev` will push the built image to DockerHub.
+
+
+
+
+ You can set up a local registry by first running this command:
+
+ ```
+ docker run -d -p 5000:5000 --restart=always --name registry registry:2
+ ```
+
+ Then:
+ ```
+ skaffold dev --default-repo=localhost:5000
+ ```
+
+
+
+ You can build locally without pushing to the image registry by setting your workloads `imagePullPolicy` to `IfNotPresent` in your `manifests.yaml` file. You will also need to update your `skaffold.yaml` with the following variables in order to implement this change as noted below:
+
+
+ Example YAML
+
+ ```yaml
+ apiVersion: skaffold/v2beta29
+ kind: Config
+ metadata:
+ name: skaffold
+ build:
+ local:
+ push: false
+ useDockerCLI: true
+ ```
+
+
+
+
+
+
+ As you go through your development, Skaffold will detect any changes and will automatically go through the build and deployment process again. You will be able to see any changes reflected in the cluster.
+
+1. Point your web browser to `localhost:3000`, and you will see the `express-sample` screen.
+
diff --git a/versioned_docs/version-1.14/how-to-guides/traefik-ingress-example.md b/versioned_docs/version-1.14/how-to-guides/traefik-ingress-example.md
new file mode 100644
index 0000000000..8a2e6f0ba9
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/traefik-ingress-example.md
@@ -0,0 +1,323 @@
+---
+title: Using the Traefik Ingress Controller
+---
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+Rancher Desktop uses `K3s` under the hood, which in turn uses [Traefik](https://doc.traefik.io/traefik/) as the [default Ingress controller](https://docs.k3s.io/networking#traefik-ingress-controller) for your Kubernetes cluster. As an example, the below steps outline creating simple services that can be routed by the Ingress object.
+
+### Example Steps: Traefik Ingress Controller
+
+
+
+
+1. Open a bash session and set the node IP to your localhost address:
+
+ ```bash
+ IP=127.0.0.1
+ ```
+
+1. Create a namespace called demo:
+
+ ```bash
+ kubectl create ns demo
+ ```
+
+1. Create a `whoami` example with basic deployment, service, and Ingress objects defined:
+
+ :::note
+ Some Linux distributions don't allow listening to privileged ports by default, please see the documentation on [Traefik port binding access](../getting-started/installation.md#traefik-port-binding-access) to authorize ports if necessary.
+ :::
+
+ ```bash
+ cat << EOF | kubectl apply -n demo -f -
+ ---
+ apiVersion: apps/v1
+ kind: Deployment
+ metadata:
+ labels:
+ app: whoami
+ name: whoami
+ spec:
+ replicas: 1
+ selector:
+ matchLabels:
+ app: whoami
+ template:
+ metadata:
+ labels:
+ app: whoami
+ spec:
+ containers:
+ - image: traefik/whoami:latest
+ name: whoami
+ ports:
+ - containerPort: 80
+ ---
+ apiVersion: v1
+ kind: Service
+ metadata:
+ name: whoami-svc
+ spec:
+ type: ClusterIP
+ selector:
+ app: whoami
+ ports:
+ - port: 80
+ ---
+ apiVersion: networking.k8s.io/v1
+ kind: Ingress
+ metadata:
+ name: whoami-http
+ annotations:
+ traefik.ingress.kubernetes.io/router.entrypoints: web
+ spec:
+ rules:
+ - host: whoami.$IP.sslip.io
+ http:
+ paths:
+ - path: /
+ pathType: Prefix
+ backend:
+ service:
+ name: whoami-svc
+ port:
+ number: 80
+ EOF
+ ```
+
+1. Verify the ingress works by calling `curl`:
+
+ ```bash
+ curl whoami.$IP.sslip.io
+ Hostname: whoami-6ff6dcfdc8-74mwq
+ IP: 127.0.0.1
+ IP: ::1
+ IP: 10.42.0.42
+ IP: fe80::e804:41ff:feac:7eef
+ RemoteAddr: 10.42.0.45:35392
+ GET / HTTP/1.1
+ Host: whoami.127.0.0.1.sslip.io
+ User-Agent: curl/7.64.1
+ Accept: */*
+ Accept-Encoding: gzip
+ X-Forwarded-For: 10.42.0.1
+ X-Forwarded-Host: whoami.127.0.0.1.sslip.io
+ X-Forwarded-Port: 80
+ X-Forwarded-Proto: http
+ X-Forwarded-Server: traefik-d497b4cb6-4vkg9
+ X-Real-Ip: 10.42.0.1
+ ```
+
+1. Delete the resources:
+
+ ```bash
+ kubectl delete all,ingress --all -n demo
+ ```
+
+
+
+
+1. Open a bash session and set the node IP to your localhost address:
+
+
+
+
+ ```bash
+ IP=127.0.0.1
+ ```
+
+
+
+
+ ```bash
+ IP=`kubectl get node/lima-rancher-desktop -o jsonpath='{.status.addresses[?(@.type=="ExternalIP")].address}'`
+ ```
+
+
+
+
+1. Create a namespace called demo:
+
+ ```bash
+ kubectl create ns demo
+ ```
+
+1. Create a `whoami` example with basic deployment, service, and Ingress objects defined:
+
+ ```bash
+ cat << EOF | kubectl apply -n demo -f -
+ ---
+ apiVersion: apps/v1
+ kind: Deployment
+ metadata:
+ labels:
+ app: whoami
+ name: whoami
+ spec:
+ replicas: 1
+ selector:
+ matchLabels:
+ app: whoami
+ template:
+ metadata:
+ labels:
+ app: whoami
+ spec:
+ containers:
+ - image: traefik/whoami:latest
+ name: whoami
+ ports:
+ - containerPort: 80
+ ---
+ apiVersion: v1
+ kind: Service
+ metadata:
+ name: whoami-svc
+ spec:
+ type: ClusterIP
+ selector:
+ app: whoami
+ ports:
+ - port: 80
+ ---
+ apiVersion: networking.k8s.io/v1
+ kind: Ingress
+ metadata:
+ name: whoami-http
+ annotations:
+ traefik.ingress.kubernetes.io/router.entrypoints: web
+ spec:
+ rules:
+ - host: whoami.$IP.sslip.io
+ http:
+ paths:
+ - path: /
+ pathType: Prefix
+ backend:
+ service:
+ name: whoami-svc
+ port:
+ number: 80
+ EOF
+ ```
+
+1. Verify the ingress works by calling `curl`:
+
+ ```bash
+ curl whoami.$IP.sslip.io
+ Hostname: whoami-6ff6dcfdc8-74mwq
+ IP: 127.0.0.1
+ IP: 10.42.0.4
+ RemoteAddr: 10.42.0.250:54102
+ GET / HTTP/1.1
+ Host: whoami.127.0.0.1.sslip.io
+ User-Agent: curl/8.1.1
+ Accept: */*
+ Accept-Encoding: gzip
+ X-Forwarded-For: 10.42.0.246
+ X-Forwarded-Host: whoami.127.0.0.1.sslip.io
+ X-Forwarded-Port: 80
+ X-Forwarded-Proto: http
+ X-Forwarded-Server: traefik-64b96ccbcd-26wcv
+ X-Real-Ip: 10.42.0.246
+ ```
+
+1. Delete the resources:
+
+ ```bash
+ kubectl delete all,ingress --all -n demo
+ ```
+
+
+
+
+1. Open a powershell session and set the node IP to your local address:
+
+ ```shell
+ $IP = (kubectl get node/$env:COMPUTERNAME -o=jsonpath="{range .status.addresses[?(@.type == 'InternalIP')]}{.address}{end}")
+ ```
+
+1. Create a namespace called demo:
+
+ ```shell
+ kubectl create ns demo
+ ```
+
+1. Create a `whoami` example with basic deployment, service, and Ingress objects defined:
+
+ ```shell
+ echo @"
+ ---
+ apiVersion: apps/v1
+ kind: Deployment
+ metadata:
+ labels:
+ app: whoami
+ name: whoami
+ spec:
+ replicas: 1
+ selector:
+ matchLabels:
+ app: whoami
+ template:
+ metadata:
+ labels:
+ app: whoami
+ spec:
+ containers:
+ - image: traefik/whoami:latest
+ name: whoami
+ ports:
+ - containerPort: 80
+ ---
+ apiVersion: v1
+ kind: Service
+ metadata:
+ name: whoami-svc
+ spec:
+ type: ClusterIP
+ selector:
+ app: whoami
+ ports:
+ - port: 80
+ ---
+ apiVersion: networking.k8s.io/v1
+ kind: Ingress
+ metadata:
+ name: whoami-http
+ annotations:
+ traefik.ingress.kubernetes.io/router.entrypoints: web
+ spec:
+ rules:
+ - host: whoami.$IP.sslip.io
+ http:
+ paths:
+ - path: /
+ pathType: Prefix
+ backend:
+ service:
+ name: whoami-svc
+ port:
+ number: 80
+ "@ | kubectl apply -n demo -f -
+ ```
+
+1. Verify the ingress works by calling `curl`:
+
+ ```shell
+ curl whoami.$IP.sslip.io
+ ```
+
+1. Delete the resources:
+
+ ```shell
+ kubectl delete all,ingress --all -n demo
+ ```
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/transfer-container-images.md b/versioned_docs/version-1.14/how-to-guides/transfer-container-images.md
new file mode 100644
index 0000000000..cc9eddc385
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/transfer-container-images.md
@@ -0,0 +1,115 @@
+---
+title: Transfer Container Images
+---
+
+
+
+
+
+Rancher Desktop provides `dockerd` and `containerd` as container engine options to manage containers. There are occasions when you might want to transfer the images from one container engine environment to the other. Or you may have migrated to Rancher Desktop from a different container management application and might want to bring the local images from the previous application environment to the Rancher Desktop environment. This guide provides steps to transfer images using the `save` and `load` commands.
+
+### Steps
+
+**1. Save image(s) from the source environment to a tar archive.**
+
+
+
+
+- Save a single image
+```
+nerdctl save -o local-image.tar image:tag
+```
+
+- Save multiple images
+```
+nerdctl save -o local-images.tar image1:tag1 image2:tag2
+```
+
+- Save all images in a namespace
+
+Below two commands use [jq](https://stedolan.github.io/jq/) for JSON parsing. The long command performs the below steps:
+
+- The `nerdctl -n k8s.io image ls` sub command gets the list of all images present in the `k8s.io` namespace, hence doesn't include images from any other namespace, `default` for instance.
+- The `jq` sub command filters and formats the images list from the previous step.
+ - The `select(.Repository!=\"\")` part of the command skips those images with repository having a value of ``.
+ - The `if (.Tag=="") then .Repository else (.Repository+":"+.Tag) end')` part of the command formats the name of the images to be just the `` or `:` depending on whether a image tag has a value of `` or not.
+- Finally the `nerdctl -n k8s.io save -o all-local-images-in-namespace.tar` part of the command saves the filtered and formatted images list from the previous two steps into a tar file.
+
+
+
+
+```
+nerdctl -n k8s.io save -o all-local-images-in-namespace.tar $(nerdctl -n k8s.io image ls --format '{{json .}}' | jq -r 'select(.Repository!="") | if (.Tag=="") then .Repository else (.Repository+":"+.Tag) end')
+```
+
+
+
+
+```
+nerdctl -n k8s.io save -o all-local-images-in-namespace.tar $(nerdctl -n k8s.io image ls --format '{{json .}}' | jq -r 'select(.Repository!=\"\") | if (.Tag==\"\") then .Repository else (.Repository+\":\"+.Tag) end')
+```
+
+
+
+
+
+
+
+- Save a single image
+```
+docker save -o local-image.tar image:tag
+```
+
+- Save multiple images
+```
+docker save -o local-images.tar image1:tag1 image2:tag2
+```
+
+- Save all local images
+
+Below two commands use [jq](https://stedolan.github.io/jq/) for JSON parsing. The long command performs the below steps:
+
+- The `docker image ls` sub command gets the list of all local images.
+- The `jq` sub command filters and formats the images list from the previous step.
+ - The `select(.Repository!=\"\")` part of the command skips those images with repository having a value of ``.
+ - The `if (.Tag=="") then .Repository else (.Repository+":"+.Tag) end')` part of the command formats the name of the images to be just the `` or `:` depending on whether a image tag has a value of `` or not.
+- Finally the `docker save -o all-local-images-in-namespace.tar` part of the command saves the filtered and formatted images list from the previous two steps into a tar file.
+
+
+
+
+```
+docker save -o all-local-images-in-namespace.tar $(docker image ls --format '{{json .}}' | jq -r 'select(.Repository!="") | if (.Tag=="") then .Repository else (.Repository+":"+.Tag) end')
+```
+
+
+
+
+```
+docker save -o all-local-images-in-namespace.tar $(docker image ls --format '{{json .}}' | jq -r 'select(.Repository!=\"\") | if (.Tag==\"\") then .Repository else (.Repository+\":\"+.Tag) end')
+```
+
+
+
+
+
+
+
+**2. Load images from the saved tar archive in the target environment.**
+
+
+
+
+```
+nerdctl load < local-images.tar
+```
+
+
+
+
+```
+docker load < local-images.tar
+```
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/using-testcontainers.md b/versioned_docs/version-1.14/how-to-guides/using-testcontainers.md
new file mode 100644
index 0000000000..2e83171e99
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/using-testcontainers.md
@@ -0,0 +1,120 @@
+---
+title: Using Testcontainers on Rancher Desktop
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Rancher Desktop can be used with [Testcontainers](https://testcontainers.com/) to execute ephemeral tests and containers that work inside Docker. This guide demonstrates the use of Testcontainers with a sample repository.
+
+### Prerequisites
+
+[Testcontainers](https://testcontainers.com/) can only be used with the `moby (dockerd)` runtime as it requires a Docker-API compatible container runtime. Kubernetes must be disabled for machines on Apple Silicon. The setting can be disabled via the **Preferences > Kubernetes** dialog, or by using the `rdctl` command below:
+
+```bash
+rdctl set --kubernetes-enabled=false
+```
+
+ Please also ensure that [Apache Maven](https://maven.apache.org/install.html) is installed on your machine in order to make use of the [`mvn verify`](https://maven.apache.org/run-maven/index.html) command.
+
+
+
+
+You can download a sample test repository in the `testcontainers-java-repro` located here: https://github.com/testcontainers/testcontainers-java-repro
+
+After the repository is downloaded, please navigate to the `testcontainers-java-repro` folder and run the command `mvn verify`.
+
+```bash
+mvn verify
+```
+
+After the command has been run, you should see a `BUILD SUCCESS` with test statistics for failures, number of tests ran, skipped tests, time elapsed, and errors.
+
+
+
+
+You can download a sample test repository in the `testcontainers-java-repro` located here: https://github.com/testcontainers/testcontainers-java-repro
+
+
+
+
+Currently, workarounds are needed for using Testcontainers on macOS M1 machines. Below are methods for using Testcontainers on either runtime, depending on administrative access.
+
+#### [QEMU](../ui/preferences/virtual-machine/emulation.md#qemu)
+
+
+Workaround Summary
+
+This runtime can be used with administrative access enabled which can be set via the [**Preferences > Application > General**](../ui/preferences/application/general.md) dialog. This will ensure that routable IP's are allocated.
+
+Next, export the virtual machine port explicitly using the command below:
+
+```bash
+export TESTCONTAINERS_HOST_OVERRIDE=$(rdctl shell ip a show rd0 | awk '/inet / {sub("/.*",""); print $2}')
+```
+
+
+
+#### [VZ](../ui/preferences/virtual-machine/emulation.md#vz)
+
+
+Workaround Summary
+
+This runtime can be used with administrative access enabled which can be set via the [**Preferences > Application > General**](../ui/preferences/application/general.md) dialog. This will ensure that routable IP's are allocated.
+
+Next, export the virtual machine port explicitly using the command below:
+
+```bash
+export TESTCONTAINERS_HOST_OVERRIDE=$(rdctl shell ip a show vznat | awk '/inet / {sub("/.*",""); print $2}')
+```
+
+For `VZ` virtual machines, you can also use Testcontainers without the need for administrative access by exporting the settings below:
+
+```bash
+export DOCKER_HOST=unix://$HOME/.rd/docker.sock
+export TESTCONTAINERS_DOCKER_SOCKET_OVERRIDE=/var/run/docker.sock
+export TESTCONTAINERS_HOST_OVERRIDE=$(rdctl shell ip a show vznat | awk '/inet / {sub("/.*",""); print $2}')
+```
+
+
+
+After the respective virtual machine settings have been applied, and the repository is downloaded, please navigate to the `testcontainers-java-repro` folder and run the command `mvn verify`.
+
+```shell
+mvn verify
+```
+
+After the command has been run, you should see a `BUILD SUCCESS` with test statistics for failures, number of tests ran, skipped tests, time elapsed, and errors.
+
+
+
+
+After the repository is downloaded, please navigate to the `testcontainers-java-repro` folder and run the command `mvn verify`.
+
+```shell
+mvn verify
+```
+
+After the command has been run, you should see a `BUILD SUCCESS` with test statistics for failures, number of tests ran, skipped tests, time elapsed, and errors.
+
+
+
+
+
+
+
+You can download a sample test repository in the `testcontainers-java-repro` located here: https://github.com/testcontainers/testcontainers-java-repro
+
+After the repository is downloaded, please navigate to the `testcontainers-java-repro` folder and run the command `mvn verify`.
+
+```shell
+mvn verify
+```
+
+After the command has been run, you should see a `BUILD SUCCESS` with test statistics for failures, number of tests ran, skipped tests, time elapsed, and errors.
+
+
+
diff --git a/versioned_docs/version-1.14/how-to-guides/vs-code-docker.md b/versioned_docs/version-1.14/how-to-guides/vs-code-docker.md
new file mode 100644
index 0000000000..49df3b80d3
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/vs-code-docker.md
@@ -0,0 +1,49 @@
+---
+title: Debugging a Container App with VS Code Docker extension
+---
+
+
+
+
+
+The VS Code Docker extension makes it easy to build, manage, debug and deploy containerized applications in Visual Studio Code.
+
+### Steps to debug a sample application running within a container
+
+1. Install and launch Rancher Desktop. Select `dockerd (moby)` as the Container Runtime from the `Kubernetes Settings` menu.
+
+
+
+2. Install and launch Visual Studio Code or Visual Studio Code Insiders. This tutorial uses Visual Studio Code.
+
+
+
+[VS Code Docker]: https://code.visualstudio.com/docs/containers/overview
+
+3. Install the VS Code Docker extension from the marketplace.
+
+
+
+4. You can use the samples provided at this Github repository, https://github.com/bwateratmsft/samples. Clone this repository and open `expressapp` folder in your VS Code session.
+
+6. Open the command palette (Ctrl+Shift+P, F1, or Cmd+Shift+P) and run "Add Docker Files to Workspace". Since this is an Express app, Select `Node.js` as the Application Platform and `3000` (or any other available port) as the `port`. As it's a simple example, select `No` for the `Include optional Docker Compose files` prompt. This step adds a `Dockerfile` and `Launch Configuration` required to debug the application.
+
+
+
+7. Insert a breakpoint in the code.
+
+
+
+8. In the Debug window at the top, switch the active debug configuration to "Docker Node.js Launch". Press `F5` to start the application container in `Debug` mode. You will see the sample application's landing page opening in your browser, and the code execution stopping at the breakpoint. From here, you can debug the application as if it's running on your host.
+
+
+
+
+
+9. Sometimes, the application might not break at the set breakpoint on the first run as the debugging process may not have started. In this case, refresh the browser to trigger the execution again to hit the breakpoint. You can also get around this behavior by setting the property `inspectMode: 'break'` in `task.json` file to prevent the app from running until the debugger attaches.
+
+10. On some machines, the firewall settings might prevent the debugging process from establishing a connection between the host and the container processes. In this case, you can add a firewall rule to allow communication between the VM where the container is running and the host where you have the VS Code session running. On Windows, you can add a firewall rule by running the below command from a privileged powershell:
+
+```powershell
+New-NetFirewallRule -Action Allow -Description 'Allow communication from WSL containers' -Direction Inbound -Enabled True -InterfaceAlias 'vEthernet (WSL)' -Name 'WSL Inbound' -DisplayName 'WSL Inbound'
+```
diff --git a/versioned_docs/version-1.14/how-to-guides/vs-code-remote-containers.md b/versioned_docs/version-1.14/how-to-guides/vs-code-remote-containers.md
new file mode 100644
index 0000000000..9d7c64c226
--- /dev/null
+++ b/versioned_docs/version-1.14/how-to-guides/vs-code-remote-containers.md
@@ -0,0 +1,59 @@
+---
+title: VS Code Remote Containers
+---
+
+
+
+
+
+The [Visual Studio Code Remote - Containers] extension lets you use a Docker container as a full-featured development environment, which helps ensure a consistent environment across developer machines and makes it easy for new team members and contributors to get up and running. Since Rancher Desktop supports Docker CLI via [Moby], you can use the Visual Studio Code Remote - Containers extension out-of-the-box.
+
+### Steps to try a sample dev container
+
+1. Install and launch Rancher Desktop. Select `dockerd (moby)` as the Container Runtime from the `Kubernetes Settings` menu.
+
+
+
+2. Install and launch Visual Studio Code or Visual Studio Code Insiders. This tutorial uses Visual Studio Code.
+
+
+
+3. Install the Remote Development extension pack.
+
+
+
+4. After the extension is installed, you will see the extension item in the side bar, and a green button at the lower left corner to show the command palette with various options/commands related to `Remote Development`.
+
+
+
+5. Microsoft provides a number of sample dev containers at this GitHub repository: https://github.com/microsoft/vscode-dev-containers.git. Clone this repository to your local machine.
+
+```
+git clone https://github.com/microsoft/vscode-dev-containers.git
+```
+
+6. Press `F1` to bring up a search bar on the command pallette to query for available commands. Begin to type in "Dev Containers: Open Folder in Container..." and click on the command `Dev Containers: Open Folder in Container...`. Browse to one of the samples in the cloned respository, e.g., `javascript-node`.
+
+
+
+
+
+
+7. On selecting a sample, you will see the progress notification  while the container is being loaded, and once the container is successfully started, the bottom left corner shows the container name. 
+
+8. Once the container is started, Press `F5` in the VS Code IDE to start the sample application. You will see that the application is started and served on `localhost:3000`.
+
+
+
+Congratulations! You have successfully loaded and run a sample dev container using Rancher Desktop and VS Code.
+
+
+### Next steps
+
+Microsoft has provided extensive documentation about using dev containers in various scenarios [here]. Please refer to the following tutorials to try a use case that's relevant to your needs.
+
+[Visual Studio Code Remote - Containers]: https://marketplace.visualstudio.com/items?itemName=ms-vscode-remote.remote-containers
+[Moby]: https://mobyproject.org/
+[here]: https://code.visualstudio.com/docs/remote/remote-overview
+
+Happy Containerizing with Rancher Desktop!
diff --git a/versioned_docs/version-1.14/img/examples/rancherUiMainPage.png b/versioned_docs/version-1.14/img/examples/rancherUiMainPage.png
new file mode 100644
index 0000000000..9b56dd35e8
Binary files /dev/null and b/versioned_docs/version-1.14/img/examples/rancherUiMainPage.png differ
diff --git a/versioned_docs/version-1.14/img/examples/rancherUiWelcomePage.png b/versioned_docs/version-1.14/img/examples/rancherUiWelcomePage.png
new file mode 100644
index 0000000000..2067d8ae63
Binary files /dev/null and b/versioned_docs/version-1.14/img/examples/rancherUiWelcomePage.png differ
diff --git a/versioned_docs/version-1.14/img/features/diagnostics-checks-table.png b/versioned_docs/version-1.14/img/features/diagnostics-checks-table.png
new file mode 100644
index 0000000000..fcdafb09e1
Binary files /dev/null and b/versioned_docs/version-1.14/img/features/diagnostics-checks-table.png differ
diff --git a/versioned_docs/version-1.14/img/how-it-works-rancher-desktop.svg b/versioned_docs/version-1.14/img/how-it-works-rancher-desktop.svg
new file mode 100644
index 0000000000..f352ca0f5b
--- /dev/null
+++ b/versioned_docs/version-1.14/img/how-it-works-rancher-desktop.svg
@@ -0,0 +1,1170 @@
+
+
+
diff --git a/versioned_docs/version-1.14/img/intro/intro.png b/versioned_docs/version-1.14/img/intro/intro.png
new file mode 100644
index 0000000000..45ee7c8bd8
Binary files /dev/null and b/versioned_docs/version-1.14/img/intro/intro.png differ
diff --git a/versioned_docs/version-1.14/img/kubernetes-cluster-progress.png b/versioned_docs/version-1.14/img/kubernetes-cluster-progress.png
new file mode 100644
index 0000000000..c318d648c8
Binary files /dev/null and b/versioned_docs/version-1.14/img/kubernetes-cluster-progress.png differ
diff --git a/versioned_docs/version-1.14/img/kubernetes-settings-main-page.png b/versioned_docs/version-1.14/img/kubernetes-settings-main-page.png
new file mode 100644
index 0000000000..41ebdb2e09
Binary files /dev/null and b/versioned_docs/version-1.14/img/kubernetes-settings-main-page.png differ
diff --git a/versioned_docs/version-1.14/img/reset-kubernetes.png b/versioned_docs/version-1.14/img/reset-kubernetes.png
new file mode 100644
index 0000000000..d994bdfab7
Binary files /dev/null and b/versioned_docs/version-1.14/img/reset-kubernetes.png differ
diff --git a/versioned_docs/version-1.14/img/tutorial/docsVersionDropdown.png b/versioned_docs/version-1.14/img/tutorial/docsVersionDropdown.png
new file mode 100644
index 0000000000..ff1cbe6889
Binary files /dev/null and b/versioned_docs/version-1.14/img/tutorial/docsVersionDropdown.png differ
diff --git a/versioned_docs/version-1.14/img/tutorial/localeDropdown.png b/versioned_docs/version-1.14/img/tutorial/localeDropdown.png
new file mode 100644
index 0000000000..d7163f9675
Binary files /dev/null and b/versioned_docs/version-1.14/img/tutorial/localeDropdown.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/rd-main.png b/versioned_docs/version-1.14/img/vscodedocker/rd-main.png
new file mode 100644
index 0000000000..6332e95765
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/rd-main.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-add-docker-files-1.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-add-docker-files-1.png
new file mode 100644
index 0000000000..739667cb16
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-add-docker-files-1.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint-hit.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint-hit.png
new file mode 100644
index 0000000000..42e5e5b6f1
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint-hit.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint.png
new file mode 100644
index 0000000000..69126d6544
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-breakpoint.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-configuration.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-configuration.png
new file mode 100644
index 0000000000..d15c01763d
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-debug-configuration.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-marketplace.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-marketplace.png
new file mode 100644
index 0000000000..2899db0eef
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-docker-marketplace.png differ
diff --git a/versioned_docs/version-1.14/img/vscodedocker/vscode-main.png b/versioned_docs/version-1.14/img/vscodedocker/vscode-main.png
new file mode 100644
index 0000000000..d990cb9977
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscodedocker/vscode-main.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/rd-main.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/rd-main.png
new file mode 100644
index 0000000000..6332e95765
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/rd-main.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-main.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-main.png
new file mode 100644
index 0000000000..d990cb9977
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-main.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-appinbrowser.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-appinbrowser.png
new file mode 100644
index 0000000000..a3d134fa0f
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-appinbrowser.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandbutton.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandbutton.png
new file mode 100644
index 0000000000..0d7b1fa8ef
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandbutton.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandpalette.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandpalette.png
new file mode 100644
index 0000000000..ba080de06e
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-commandpalette.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containerprogress.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containerprogress.png
new file mode 100644
index 0000000000..a4d853bce8
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containerprogress.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containersuccess.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containersuccess.png
new file mode 100644
index 0000000000..c93984a079
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-containersuccess.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-installed.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-installed.png
new file mode 100644
index 0000000000..a0eb1b59e7
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-installed.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-marketplace.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-marketplace.png
new file mode 100644
index 0000000000..37eafe3d33
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-marketplace.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-openfolder.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-openfolder.png
new file mode 100644
index 0000000000..3194b5cf59
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-openfolder.png differ
diff --git a/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-trysample.png b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-trysample.png
new file mode 100644
index 0000000000..9dda83c840
Binary files /dev/null and b/versioned_docs/version-1.14/img/vscoderemotecontainers/vscode-remotedevelopment-trysample.png differ
diff --git a/versioned_docs/version-1.14/references/architecture.md b/versioned_docs/version-1.14/references/architecture.md
new file mode 100644
index 0000000000..1f6da4d7fc
--- /dev/null
+++ b/versioned_docs/version-1.14/references/architecture.md
@@ -0,0 +1,11 @@
+---
+title: Architecture
+---
+
+
+
+
+
+
+
+Rancher Desktop is an electron-based application that wraps other tools while it also provides the user experience to create a simple experience. On macOS and Linux, Rancher Desktop leverages a virtual machine to run containerd or dockerd and Kubernetes. Windows Subsystem for Linux v2 is leveraged for Windows systems. All you need to do is download and run the application.
\ No newline at end of file
diff --git a/versioned_docs/version-1.14/references/bundled-utilities.md b/versioned_docs/version-1.14/references/bundled-utilities.md
new file mode 100644
index 0000000000..18da7fbf30
--- /dev/null
+++ b/versioned_docs/version-1.14/references/bundled-utilities.md
@@ -0,0 +1,36 @@
+---
+title: Bundled Utilities
+---
+
+import Version160 from '../bundled-utilities-version-info/v1.6.0.md';
+import Version170 from '../bundled-utilities-version-info/v1.7.0.md';
+import Version180 from '../bundled-utilities-version-info/v1.8.0.md';
+import Version190 from '../bundled-utilities-version-info/v1.9.0.md';
+import Version191 from '../bundled-utilities-version-info/v1.9.1.md';
+import Version110 from '../bundled-utilities-version-info/v1.10.0.md';
+import Version111 from '../bundled-utilities-version-info/v1.11.0.md';
+import Version112 from '../bundled-utilities-version-info/v1.12.0.md';
+import Version113 from '../bundled-utilities-version-info/v1.13.0.md';
+import Version114 from '../bundled-utilities-version-info/v1.14.0.md';
+
+
+
+
+
+Rancher Desktop uses several utilities/subsystems as dependencies under the hood for various purposes. For example, **docker CLI** to interact with **dockerd**, **helm** to manage charts, **trivy** for container image scanning, etc. This page provides information about the versions of the bundled utilities that go into a specific Rancher Desktop release version.
+
+| Rancher Desktop Version | Dependency Versions |
+| ------------- | ---------------- |
+| v1.14.0 | |
+| v1.13.0 | |
+| v1.12.0 | |
+| v1.11.0 | |
+| v1.10.0 | |
+| v1.9.1 | |
+| v1.9.0 | |
+| v1.8.1 | There are no updated dependencies in the 1.8.1 release |
+| v1.8.0 | |
+| v1.7.0 | |
+| v1.6.2 | There are no updated dependencies in the 1.6.2 release |
+| v1.6.1 | There are no updated dependencies in the 1.6.1 release |
+| v1.6.0 | |
diff --git a/versioned_docs/version-1.14/references/rdctl-command-reference.md b/versioned_docs/version-1.14/references/rdctl-command-reference.md
new file mode 100644
index 0000000000..fea933422c
--- /dev/null
+++ b/versioned_docs/version-1.14/references/rdctl-command-reference.md
@@ -0,0 +1,652 @@
+---
+title: "Command Reference: rdctl"
+---
+
+
+
+
+
+`rdctl` is a command-line tool, included in Rancher Desktop that enables command-line access to GUI features. `rdctl` is developed to help users with tasks such as scripting (for automation, CI/CD), troubleshooting, remote management, etc. The current version of `rdctl` supports the below commands (with support for more commands to be added in upcoming releases):
+
+:::info
+As the current version of `rdctl` is experimental, all subcommand names, their arguments, and their output are still subject to change.
+
+For many `rdctl` commands, there are corresponding `API` calls that can be applied. Listed below are the available commands shown in both formats. The `api` examples will assume `curl` as the tool being used to talk to the API.
+
+Additionally, some examples make use of credentials which can be found in these locations across platforms:
+
+- Linux: ~/.local/share/rancher-desktop/
+- macOS: ~/Library/Application Support/rancher-desktop/
+- Windows: %LOCALAPPDATA%\rancher-desktop\
+
+:::
+
+:::caution warning
+
+The Rancher Desktop application must be running for the following commands:
+
+
+Command List
+
+* rdctl list-settings
+* rdctl set
+* rdctl shutdown
+
+
+:::
+
+## rdctl or rdctl help
+
+Run `rdctl` or `rdctl help` to see the list of available commands.
+
+
+Example Output
+
+``` autoupdate=true
+> rdctl help
+The eventual goal of this CLI is to enable any UI-based operation to be done from the command-line as well.
+
+Usage:
+ rdctl [command]
+
+Available Commands:
+ api Run API endpoints directly
+ completion Generate the autocompletion script for the specified shell
+ create-profile Generate a deployment profile in either macOS plist or Windows registry format
+ extension Manage extensions
+ factory-reset Clear all the Rancher Desktop state and shut it down.
+ help Help about any command
+ list-settings Lists the current settings.
+ set Update selected fields in the Rancher Desktop UI and restart the backend.
+ shell Run an interactive shell or a command in a Rancher Desktop-managed VM
+ shutdown Shuts down the running Rancher Desktop application
+ snapshot Manage Rancher Desktop snapshots
+ start Start up Rancher Desktop, or update its settings.
+ version Shows the CLI version.
+
+Flags:
+ --config-path string config file (default ~/$HOME/rancher-desktop/rd-engine.json)
+ -h, --help help for rdctl
+ --host string default is 127.0.0.1; most useful for WSL
+ --password string overrides the password setting in the config file
+ --port string overrides the port setting in the config file
+ --user string overrides the user setting in the config file
+
+Use "rdctl [command] --help" for more information about a command.
+```
+
+
+
+## rdctl api
+
+Run `rdctl api /` to list all endpoints globally.
+
+
+Example Output
+
+``` autoupdate=true
+$ rdctl api / | jq -r .[]
+GET /
+GET /v0
+GET /v1
+GET /v1/about
+GET /v1/backend_state
+PUT /v1/backend_state
+GET /v1/diagnostic_categories
+GET /v1/diagnostic_checks
+POST /v1/diagnostic_checks
+GET /v1/diagnostic_ids
+GET /v1/extensions
+POST /v1/extensions/install
+POST /v1/extensions/uninstall
+PUT /v1/factory_reset
+PUT /v1/propose_settings
+GET /v1/settings
+PUT /v1/settings
+GET /v1/settings/locked
+PUT /v1/shutdown
+POST /v1/snapshot/restore
+GET /v1/snapshots
+DELETE /v1/snapshots
+POST /v1/snapshots
+GET /v1/transient_settings
+PUT /v1/transient_settings
+```
+
+
+
+## rdctl api /vX
+
+Run `rdctl api /v1` to list all endpoints in version 1.
+
+
+Example Output
+
+``` autoupdate=true
+$ rdctl api /v1 | jq -r .[]
+GET /v1
+GET /v1/about
+GET /v1/backend_state
+PUT /v1/backend_state
+GET /v1/diagnostic_categories
+GET /v1/diagnostic_checks
+POST /v1/diagnostic_checks
+GET /v1/diagnostic_ids
+GET /v1/extensions
+POST /v1/extensions/install
+POST /v1/extensions/uninstall
+PUT /v1/factory_reset
+PUT /v1/propose_settings
+GET /v1/settings
+PUT /v1/settings
+GET /v1/settings/locked
+PUT /v1/shutdown
+POST /v1/snapshot/restore
+GET /v1/snapshots
+DELETE /v1/snapshots
+POST /v1/snapshots
+GET /v1/transient_settings
+PUT /v1/transient_settings
+```
+
+
+
+## rdctl api /v1/settings
+
+`rdctl api [endpoints]` are commands that are most useful for users working directly with the API itself, and therefore they would not be for everyday use, such as `rdctl set` might be. For example,
+
+a command such as
+
+```console
+rdctl api /v1/settings --method PUT --body '{"kubernetes": {"enabled": false}}'
+```
+
+is the same as
+
+```console
+rdctl set --kubernetes-enabled=false
+```
+
+but less concise and user-friendly.
+
+## rdctl create-profile
+
+Generates a deployment profile for Rancher Desktop settings in either macOS `.plist` or Windows `.reg` format.
+
+```console
+rdctl create-profile
+```
+
+
+Options & Example Command
+
+**Options**
+
+```console
+--input [FILE] File containing a JSON document.
+--body [JSON] Command-line option containing a JSON document
+--from-settings Use current settings.
+--output [plist, reg] An output of .plist files for macOS and .reg files for Windows.
+
+Additional options for --output reg:
+--type [locked, defaults] The locked field is set as default, otherwise the default type can be specified.
+--hive [hklm, hkcu] The hklm field is set as default, otherwise hkcu can be specified.
+```
+
+**Example**
+
+```console
+rdctl create-profile --output reg --hive=Hkcu --from-settings
+```
+
+
+
+## rdctl extension install
+
+Installs a Rancher Desktop extension.
+
+```console
+rdctl extension install
+```
+
+
+Options & Example Output
+
+**Options**
+
+```console
+--force Avoids any interactivity.
+: The is optional, e.g. splatform/epinio-docker-desktop:latest.
+```
+
+**Example**
+
+``` autoupdate=true
+$ rdctl extension install docker/logs-explorer-extension:0.2.2
+Installing image docker/logs-explorer-extension:0.2.2: Created
+```
+
+
+
+## rdctl extension ls
+
+Lists currently installed images.
+
+```console
+rdctl extension ls
+```
+
+
+Example Output
+
+**Example**
+
+``` autoupdate=true
+$ rdctl extension ls
+Extension IDs
+
+docker/logs-explorer-extension:0.2.2
+```
+
+
+
+## rdctl extension uninstall
+
+Uninstalls a Rancher Desktop extension.
+
+```console
+rdctl extension uninstall
+```
+
+
+Options & Example Output
+
+**Options**
+
+```console
+: The is optional, e.g. splatform/epinio-docker-desktop:latest.
+```
+
+**Example**
+
+``` autoupdate=true
+$ rdctl extension uninstall docker/logs-explorer-extension:0.2.2
+Uninstalling image docker/logs-explorer-extension:0.2.2: Deleted docker/logs-explorer-extension:0.2.2
+```
+
+
+
+## rdctl list-settings
+
+
+
+
+Run `rdctl list-settings` to see the current active configuration.
+
+
+Options & Example Output
+
+**Options**
+
+``` autoupdate=true
+
+> rdctl list-settings --help
+Lists the current settings in JSON format.
+
+Usage:
+ rdctl list-settings [flags]
+
+Flags:
+ -h, --help help for list-settings
+
+Global Flags:
+ --config-path string config file (default ~/HOME/rancher-desktop/rd-engine.json)
+ --host string default is 127.0.0.1; most useful for WSL
+ --password string overrides the password setting in the config file
+ --port string overrides the port setting in the config file
+ --user string overrides the user setting in the config file
+```
+
+**Example Output Using macOS Environment**
+
+``` autoupdate=true
+> rdctl list-settings
+{
+ "version": 10,
+ "application": {
+ "adminAccess": true,
+ "debug": false,
+ "extensions": {
+ "allowed": {
+ "enabled": false,
+ "list": []
+ },
+ "installed": {}
+ },
+ "pathManagementStrategy": "rcfiles",
+ "telemetry": {
+ "enabled": true
+ },
+ "updater": {
+ "enabled": true
+ },
+ "autoStart": false,
+ "startInBackground": false,
+ "hideNotificationIcon": false,
+ "window": {
+ "quitOnClose": false
+ }
+ },
+ "containerEngine": {
+ "allowedImages": {
+ "enabled": false,
+ "patterns": [],
+ "locked": false
+ },
+ "name": "containerd"
+ },
+ "virtualMachine": {
+ "memoryInGB": 4,
+ "numberCPUs": 2,
+ "hostResolver": true
+ },
+ "WSL": {
+ "integrations": {}
+ },
+ "kubernetes": {
+ "version": "1.28.2",
+ "port": 6443,
+ "enabled": true,
+ "options": {
+ "traefik": true,
+ "flannel": true
+ },
+ "ingress": {
+ "localhostOnly": false
+ }
+ },
+ "portForwarding": {
+ "includeKubernetesServices": false
+ },
+ "images": {
+ "showAll": true,
+ "namespace": "k8s.io"
+ },
+ "diagnostics": {
+ "showMuted": true,
+ "mutedChecks": {
+ "STATIC_FALSE": true
+ }
+ },
+ "experimental": {
+ "virtualMachine": {
+ "type": "vz",
+ "useRosetta": false,
+ "socketVMNet": true,
+ "mount": {
+ "type": "reverse-sshfs",
+ "9p": {
+ "securityModel": "none",
+ "protocolVersion": "9p2000.L",
+ "msizeInKib": 128,
+ "cacheMode": "mmap"
+ }
+ },
+ "networkingTunnel": false,
+ "proxy": {
+ "enabled": false,
+ "address": "",
+ "password": "",
+ "port": 3128,
+ "username": "",
+ "noproxy": [
+ "0.0.0.0/8",
+ "10.0.0.0/8",
+ "127.0.0.0/8",
+ "169.254.0.0/16",
+ "172.16.0.0/12",
+ "192.168.0.0/16",
+ "224.0.0.0/4",
+ "240.0.0.0/4"
+ ]
+ }
+ }
+ }
+}
+
+```
+
+
+
+
+
+
+Run the following API call to see the current active configuration:
+
+
+Example Command
+
+```console
+curl -s -H "Authorization: Basic $AUTH" http://localhost:6107/v1/settings -X GET
+```
+
+
+
+**Note:** Using `-X GET` is optional. You could also just use the preceding command by itself.
+
+
+
+
+## rdctl set
+
+
+
+
+Run `rdctl set [flags]` to set properties. In most of the cases, Kubernetes would be reset on running the `set` command. You can set multiple properties by chaining in a single command. See some examples below.
+
+
+Example Command
+
+```console
+> rdctl set --kubernetes-enabled=false
+> rdctl set --container-engine docker --kubernetes-version 1.21.2
+```
+
+
+
+
+
+
+Run the following API call to set properties:
+
+
+Example Command
+
+```console
+curl -s -H "Authorization: Basic $AUTH" http://localhost:6107/v1/settings -d '{ "kubernetes": { "containerEngine": "docker", "enabled": false, "version":"1.23.5" }}' -X PUT
+```
+
+
+
+
+
+
+## rdctl shutdown
+
+
+
+
+Run `rdctl shutdown` to gracefully shut down Rancher Desktop.
+
+
+Example Output
+
+```console
+> rdctl shutdown
+Shutting down.
+```
+
+
+
+
+
+
+Run the following API call to shut down Rancher Desktop:
+
+
+Example Command
+
+```shell
+curl -s -H "Authorization: Basic $AUTH" http://localhost:6107/v1/shutdown -X PUT
+```
+
+
+
+
+
+
+## rdctl snapshot
+
+Run `rdctl snapshot` to store the current configuration of your virtual machine and all associated settings as a snapshot.
+
+
+Options & Example Commands
+
+**Options**
+
+```text
+Usage:
+ rdctl snapshot [command]
+
+Available Commands:
+ create Create a snapshot
+ delete Delete a snapshot
+ list List snapshots
+ restore Restore a snapshot
+ unlock Remove snapshot lock
+
+Flags:
+ -h, --help help for snapshot
+
+Global Flags:
+ --config-path string config file (default /Users/[username]/Library/Application Support/rancher-desktop/rd-engine.json)
+ --host string default is 127.0.0.1; most useful for WSL
+ --password string overrides the password setting in the config file
+ --port string overrides the port setting in the config file
+ --user string overrides the user setting in the config file
+
+Use "rdctl snapshot [command] --help" for more information about a command.
+```
+
+**Example**
+
+``` autoupdate=true
+
+
+
+$ rdctl snapshot create example_snapshot
+$ rdctl snapshot delete example_snapshot
+$ rdctl snapshot list --json
+{"created":"2023-10-23T13:11:45.311273-07:00","name":"Snap_2023-10-23_13_11_25","description":""}
+{"created":"2023-10-23T13:13:34.439465-07:00","name":"Example_Snapshot_1","description":"Snapshot descriptions can be entered in this field."}
+```
+
+
+
+## rdctl start
+
+
+
+
+Run `rdctl start` to ensure that Rancher Desktop is running and configured as requested.
+
+
+Options & Example Command
+
+**Options:**
+
+```console
+Usage:
+ rdctl start [flags]
+
+Flags:
+ --application.admin-access enable privileged operations
+ --application.auto-start start app when logging in
+ --application.debug generate more verbose logging
+ --application.hide-notification-icon don't show notification icon
+ --application.path-management-strategy string update PATH to include ~/.rd/bin (allowed values: [manual, rcfiles])
+ --application.start-in-background start app without window
+ --application.telemetry.enabled allow collection of anonymous statistics
+ --application.updater.enabled automatically update to the latest release
+ --application.window.quit-on-close terminate app when the main window is closed
+ --container-engine.allowed-images.enabled only allow images to be pulled that match the allowed patterns
+ --container-engine.name string set engine (allowed values: [containerd, docker, moby])
+ --diagnostics.show-muted unhide muted diagnostics
+ --experimental.virtual-machine.mount.9p.cache-mode string (allowed values: [none, loose, fscache, mmap])
+ --experimental.virtual-machine.mount.9p.msize-in-kib int maximum packet size
+ --experimental.virtual-machine.mount.9p.protocol-version string (allowed values: [9p2000, 9p2000.u, 9p2000.L])
+ --experimental.virtual-machine.mount.9p.security-model string (allowed values: [passthrough, mapped-xattr, mapped-file, none])
+ --experimental.virtual-machine.mount.type string how directories are shared (allowed values: [reverse-sshfs, 9p, virtiofs])
+ --experimental.virtual-machine.socket-vmnet use socket-vmnet instead of vde-vmnet
+ --experimental.virtual-machine.type string (allowed values: [qemu, vz])
+ --experimental.virtual-machine.use-rosetta
+ -h, --help help for start
+ --images.namespace string select only images from this namespace (containerd only)
+ --images.show-all show system images on Images page
+ --kubernetes.enabled run Kubernetes
+ --kubernetes.options.flannel use flannel networking; disable to install your own CNI
+ --kubernetes.options.traefik install and run traefik
+ --kubernetes.port int apiserver port
+ --kubernetes.version string choose which version of Kubernetes to run
+ --no-modal-dialogs avoid displaying dialog boxes
+ -p, --path string path to main executable
+ --port-forwarding.include-kubernetes-services show Kubernetes system services on Port Forwarding page
+ --virtual-machine.memory-in-gb int reserved RAM size
+ --virtual-machine.number-cpus int reserved number of CPUs
+
+Global Flags:
+ --config-path string config file (default /Users/{username}/Library/Application Support/rancher-desktop/rd-engine.json)
+ --host string default is localhost; most useful for WSL
+ --password string overrides the password setting in the config file
+ --port string overrides the port setting in the config file
+ --user string overrides the user setting in the config file
+```
+
+**Example:**
+
+```console
+> rdctl start --container-runtime dockerd -- kubernetes-version 1.19.3
+```
+
+
+
+
+
+
+Run the following API call to ensure Rancher Desktop is running and configured, making sure to fill in your respective user and password values:
+
+
+Example Command
+
+```shell
+curl -s -H "Authorization: Basic $(echo -n "user:PASSWORD" | base64)"
+```
+
+
+
+
+
+
+## rdctl version
+
+Run `rdctl version` to see the current rdctl CLI version.
+
+
+Example Output
+
+``` autoupdate=true
+> rdctl version
+rdctl client version: 1.1.0, targeting server version: v1
+```
+
+
diff --git a/versioned_docs/version-1.14/troubleshooting-tips.md b/versioned_docs/version-1.14/troubleshooting-tips.md
new file mode 100644
index 0000000000..01860adcbc
--- /dev/null
+++ b/versioned_docs/version-1.14/troubleshooting-tips.md
@@ -0,0 +1,117 @@
+---
+title: Troubleshooting Tips
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+This page provides tips to troubleshoot issues you may have with Rancher Desktop.
+
+### API
+
+#### Q: Rancher Desktop is stuck on `Waiting for Kubernetes API`, what do I do?
+
+**A:** The cause is hard to determine without additional information. Navigate to the Troubleshooting tab and use the button to access the logs. Then go to the [Rancher Desktop GitHub] page and file an issue with the logs attached.
+
+[Rancher Desktop Github]:
+https://github.com/rancher-sandbox/rancher-desktop/issues
+
+### Containers
+
+#### Q: How can I fix the Docker error when starting a container using the VS Code dev-containers extension with version >`v0.266`?
+
+**A:** There is a current workaround for users experiencing a Docker error when starting a container using the dev-containers extension for VS code versioned `v0.266` or later and Rancher Desktop `v1.8.1`. Disabling Wayland in the user settings will allow the container to spin up successfully. This can be accomplished by unchecking the box in the `Settings` > `Extensions` > `Dev Containers` tab labelled `Dev > Containers: Mount Wayland Socket (Applies to All Profiles)`.
+
+#### Q: How do I fix `FATA[0005] subnet 10.4.0.0/24 overlaps with other one on this address space` when running a container using `nerdctl run`?
+
+**A:** You will see this error if there's a route rule with an IP address from a conflicting subnet on the Iptables. The conflicting routes could be either from the host network (bridge mode) or the Kubernetes network. A quick workaround to this issue is to shutdown WSL via the command `wsl --shutdown`.
+
+**:warning: Please note that shutting down WSL will stop all other distros along with the `rancher-desktop` distro.**
+
+### Installation
+
+
+#### Q: I'm using Homebrew to install Rancher Desktop, but `brew install rancher-desktop` is failing, why?
+
+**A:** Due to the Homebrew cask naming conventions, the `-desktop` suffix is dropped from the cask formula name. Use `brew install rancher` instead.
+
+#### Q: How do I fix `kubectl: command not found` issue on Linux?
+
+**A:** By default, Rancher Desktop creates symlinks of `kubectl`, `docker`, `helm` and `nerdctl` binaries in the `/home//.local/bin` directory on Linux. To be able to call these commands directly from the console you may add the directory to your `PATH` environment variable by executing the following command in console and performing logout and login:
+
+```bash
+echo "export PATH=\$PATH:/home/$(whoami)/.local/bin" >> ~/.bashrc
+```
+
+#### Q: How do I fix the `Installation Aborted` error while downgrading from an existing MSI installation to an older EXE version (1.6.x or earlier) on Windows?
+
+**A:** You will see this error if the Windows registry key `HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\EventLog\Application\RancherDesktopPrivilegedService` that is supposed to be deleted during the MSI uninstallation process is not deleted for some reason. Please manually delete the registry key and try installing the EXE version. You can run the below command in a privileged shell to delete the registry key.
+
+```
+reg.exe delete HKLM\System\CurrentControlSet\Services\EventLog\Application\RancherDesktopPrivilegedService /reg:64 /f
+```
+
+
+#### Q: I can no longer run `docker compose` after installing Rancher Desktop and uninstalling Docker Desktop, what happened?
+
+**A:** This was an issue related to earlier versions (prior to 1.1.0) of Rancher Desktop. Rancher Desktop version 1.1.0 and above comes bundled with `docker-compose` for you, and makes the cli plugins available at `~/.docker/cli-plugins`. We strongly recommend you to be on the latest version of Rancher Desktop.
+
+If you still don't see `docker-compose` available then please file a bug on [Github](https://github.com/rancher-sandbox/rancher-desktop/issues/new?assignees=&labels=kind%2Fbug&template=bug_report.yml).
+
+#### Q: I do not see an entry for Rancher Desktop when running `kubectl config get-contexts`, where is it?
+
+**A:** Rancher Desktop places its configuration in the default location, `~/.kube/config,` and uses that. Your `KUBECONFIG` environment variable may be set to look elsewhere for configuration files.
+
+### Networking
+
+#### Q: Why do I see a blank screen when I launch the Cluster Dashboard?
+
+**A:** The Cluster Dashboard may not be running correctly because another process on your machine is using ports `9080` or `9443` that the Dashboard process (`steve`) depends on. To solve this, identify and terminate the process using those ports. You can use the command below to identify processes using a specific port on your host machine. Note that on macOS and Linux, the Rancher Dashboard process is named `steve`, while on Windows, it's `steve.exe`. If `steve` is the only process using ports 9080 or 9443, do not terminate it.
+
+Command to find processes using a specific port.
+
+
+
+
+```
+netstat -ano | findstr :9443
+```
+
+
+
+
+```
+lsof -nP -iTCP -sTCP:LISTEN | grep 9443
+```
+
+
+
+
+```
+lsof -nP -iTCP -sTCP:LISTEN | grep 9443
+```
+
+
+
+
+### WSL
+
+#### Q: Why do I not see my WSL distro under Rancher Desktop's WSL Integration page?
+
+**A:** You are likely using a WSL 1 distro. Rancher Desktop supports only WSL 2 distros. You can convert your WSL 1 distro into a WSL 2 distro by running the command `wsl --set-version 2`. You can also run the command `wsl --set-default-version 2` to set all the future distributions you might install to use WSL 2.
+
+
+#### Q: How do I fix `permission denied` errors when trying to use Docker on WSL?
+
+**A:** You need write-permission to access the docker socket. There are many ways to go about that, but this is one of the more common approaches. Using the Ubuntu WSL command-line:
+
+```bash
+sudo groupadd docker
+sudo adduser $USER docker
+sudo chown root:docker /var/run/docker.sock
+sudo chmod g+w /var/run/docker.sock
+newgrp docker
+```
diff --git a/versioned_docs/version-1.14/tutorials/using-persistent-storage.md b/versioned_docs/version-1.14/tutorials/using-persistent-storage.md
new file mode 100644
index 0000000000..8ce3189955
--- /dev/null
+++ b/versioned_docs/version-1.14/tutorials/using-persistent-storage.md
@@ -0,0 +1,172 @@
+---
+title: Using Persistent Storage
+---
+
+
+
+
+
+Containers are, by design, ephemeral and stateless. However, most real-world use cases require containers to produce or consume data that often needs to be persisted. To address this challenge, container engines offer mechanisms such as **Bind mounts** and **Volumes**. Both the docker and nerdctl CLIs provide options `-v` and `--mount` to start a container with a bind mount or a volume.
+
+## Bind mount
+
+**Bind mount** mounts a file or directory on the host machine into a container. For example, to mount the current directory of the host machine to `/app/src` directory of a container, you can use `-v` or the slightly verbose `--mount` as shown below.
+
+### Using `-v`
+
+#### macOS & Linux
+
+
+
+
+```console
+nerdctl container run --rm -it -v $(pwd)/src:/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+docker container run --rm -it -v $(pwd)/src:/app/src alpine:latest /bin/sh
+```
+
+
+
+#### Windows
+
+
+
+
+```console
+// Cmd
+nerdctl container run --rm -it -v %cd%/src:/app/src alpine:latest /bin/sh
+
+// Powershell
+nerdctl container run --rm -it -v ${pwd}/src:/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+// Cmd
+docker container run --rm -it -v %cd%/src:/app/src alpine:latest /bin/sh
+
+// Powershell
+docker container run --rm -it -v ${pwd}/src:/app/src alpine:latest /bin/sh
+```
+
+
+
+### Using `--mount`
+
+#### macOS & Linux
+
+
+
+
+```console
+nerdctl container run --rm -it --mount=type=bind,source=$(pwd)/src,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+docker container run --rm -it --mount=type=bind,source=$(pwd)/src,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+#### Windows
+
+
+
+
+```console
+// Cmd
+nerdctl container run --rm -it --mount=type=bind,source=%cd%/src,target=/app/src alpine:latest /bin/sh
+
+// Powershell
+nerdctl container run --rm -it --mount=type=bind,source=${pwd}/src,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+// Cmd
+docker container run --rm -it --mount=type=bind,source=%cd%/src,target=/app/src alpine:latest /bin/sh
+
+// Powershell
+docker container run --rm -it --mount=type=bind,source=${pwd}/src,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+If `/app/src` is not available on the host machine then the command creates it. Anything you create inside the directory `/app/src` on the host machine is available at `/app/src` inside the container and vice versa. Try adding or modifying content inside `/app/src` in the container and exit the container by typing `exit` in the shell. On restarting the container, you will notice that the content of `/app/src` is persisted and same would be the case for container engine, and host machine restarts.
+.
+
+:::info
+
+Currently, Rancher Desktop allows creating bind mounts only on the following directories by default: `/Users/$USER` on macOS, `/home/$USER` on Linux, and `/tmp/rancher-desktop` on both. For Windows, all files are automatically shared via WSL2.
+
+If you want to change the behavior of the mounts, you can use provisioning scripts as described in the [thread](https://github.com/rancher-sandbox/rancher-desktop/issues/1209#issuecomment-1370181132).
+
+:::
+
+## Volume
+
+**Volume** is an another mechanism to achieve persistance for container workloads. While Bind mounts link to the host's file system, volumes on the otherhand are managed by the container engine and provide data persistence and isolation from the host. For example, to create a named volume and start a container using the volume, you can use `-v` or the slightly verbose `--mount` as shown below.
+
+
+- Create a named volume
+
+
+
+
+```console
+nerdctl volume create my-persistent-data
+```
+
+
+
+```console
+docker volume create my-persistent-data
+```
+
+
+
+- Start a container using the named volume created in the previous step
+
+### Using `-v`
+
+
+
+
+```console
+nerdctl container run --rm -it -v my-persistent-data:/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+docker container run --rm -it -v my-persistent-data:/app/src alpine:latest /bin/sh
+```
+
+
+
+### Using `--mount`
+
+
+
+
+```console
+nerdctl container run --rm -it --mount=type=volume,source=my-persistent-data,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+```console
+docker container run --rm -it --mount=type=volume,source=my-persistent-data,target=/app/src alpine:latest /bin/sh
+```
+
+
+
+Try adding or modifying content inside `/app/src` in the container and exit the container by typing `exit` in the shell. On restarting the container, you will notice that the content of `/app/src` is persisted and same would be the case for container engine, and host machine restarts.
diff --git a/versioned_docs/version-1.14/tutorials/working-with-containers.md b/versioned_docs/version-1.14/tutorials/working-with-containers.md
new file mode 100644
index 0000000000..87a4ede053
--- /dev/null
+++ b/versioned_docs/version-1.14/tutorials/working-with-containers.md
@@ -0,0 +1,209 @@
+---
+title: Working with Containers
+---
+
+
+
+
+
+`nerdctl` is a Docker-compatible CLI for containerd. The primary goal of `nerdctl` is to facilitate experimenting with cutting-edge features of containerd that are not present in Docker.
+
+[Moby](https://github.com/moby/moby) is an open-source project that was created by Docker to enable and accelerate software containerization. Components include container build tools, a container registry, orchestration tools, and a runtime, and more. The Docker CLI uses the Moby runtime.
+
+## Running Containers
+
+To run a container with the default `bridge` CNI network (10.4.0.0/24):
+
+
+
+
+```
+nerdctl run -it --rm alpine
+```
+
+
+
+
+```
+docker run -it --rm alpine
+```
+
+
+
+To build an image using BuildKit:
+
+
+
+
+```
+nerdctl build -t foo /some-dockerfile-directory
+nerdctl run -it --rm foo
+```
+
+
+
+
+ ```
+docker build -t foo /some-dockerfile-directory
+docker run -it --rm foo
+```
+
+
+
+To build and send output to a local directory using BuiltKit:
+
+
+
+
+```
+nerdctl build -o type=local,dest=. /some-dockerfile-directory
+```
+
+
+
+```
+docker build -o type=local,dest=. /some-dockerfile-directory
+```
+
+
+
+## Docker Compose
+
+Docker Compose is a tool for defining and running multi-container Docker applications.
+
+
+
+
+The `nerdctl-compose` CLI is designed to be compatible with `docker-compose`:
+```
+nerdctl compose up -d
+nerdctl compose down
+```
+
+
+
+The `compose` command in the Docker CLI supports most of the `docker-compose` commands and flags. It is expected to be a drop-in replacement for `docker-compose`.
+```
+docker compose up -d
+docker compose down
+```
+
+
+
+## Exposing a Port
+
+To expose port 8000 for a container:
+
+
+
+
+```
+nerdctl run -d -p 8000:80 nginx
+```
+
+
+
+```
+docker run -d -p 8000:80 nginx
+```
+
+
+
+You can then access the container via the browser here: [http://localhost:8000/](http://localhost:8000/).
+
+*Note: By default the exposed ports are accessible on all network interfaces on macOS and Linux. However, on Windows, the exposed ports are currently only accessible through the localhost network interface (see issue [#1180](https://github.com/rancher-sandbox/rancher-desktop/issues/1180)). As a workaround, you can [configure a `portproxy` on the windows host](https://github.com/rancher-sandbox/rancher-desktop/issues/1180#issuecomment-1005514200) to expose the port to additional network interfaces.*
+
+```
+netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=8080 connectaddress=localhost
+```
+### Exposing the port of a running container
+
+If you forgot to expose the port as part of the `run` command, you can follow the steps below to start a proxy container that forwards traffic to the original container. This hack helps you avoid restarting the container and is especially useful when dealing with containerized services with longer startup times. With full disclosure, this hack is based on the suggestions in this [stackoverflow discussion](https://stackoverflow.com/questions/19897743/exposing-a-port-on-a-live-docker-container) and this [blog post](https://iximiuz.com/en/posts/docker-publish-port-of-running-container/).
+
+1. Let's say you ran a container without publishing the port (by mistake).
+
+
+
+
+```
+nerdctl run -d --name rd-nginx nginx
+```
+
+
+
+```
+docker run -d --name rd-nginx nginx
+```
+
+
+
+2. Set port variables to be used in the subsequent commands.
+
+```
+# Powershell
+$HOST_PORT=8080
+$CONTAINER_PORT=80
+
+# Bash
+export HOST_PORT=8080
+export CONTAINER_PORT=80
+```
+
+3. Get the container IP address. If you did not give a name to the container at the time of starting it, you can pass the container id in place of the container name `rd-nginx` in the commands below.
+
+
+
+
+```
+# Powershell
+$CONTAINER_IP=$(nerdctl inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' rd-nginx)
+
+# Bash
+export CONTAINER_IP=$(nerdctl inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' rd-nginx)
+```
+
+
+
+```
+# Powershell
+$CONTAINER_IP=$(docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' rd-nginx)
+
+# Bash
+export CONTAINER_IP=$(docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' rd-nginx)
+```
+
+
+
+4. Start a proxy container to forward traffic to the original container.
+
+
+
+
+```
+nerdctl run --rm -p ${HOST_PORT}:${CONTAINER_PORT} alpine/socat TCP-LISTEN:${CONTAINER_PORT},fork TCP-CONNECT:${CONTAINER_IP}:${CONTAINER_PORT}
+```
+
+
+
+```
+docker run --rm -p ${HOST_PORT}:${CONTAINER_PORT} alpine/socat TCP-LISTEN:${CONTAINER_PORT},fork TCP-CONNECT:${CONTAINER_IP}:${CONTAINER_PORT}
+```
+
+
+
+5. Once the proxy container is successfully run, you can access the NGINX server at `localhost:8080` from your host machine.
+
+## Targeting a Kubernetes Namespace
+
+You may also target a Kubernetes namespace with the `--namespace` parameter with `containerd`. Please note that `docker` doesn't use namespaces.
+
+
+
+
+```
+nerdctl --namespace k8s.io build -t demo:latest /code/demos/rd/anvil-app
+nerdctl --namespace k8s.io ps
+```
+
+
+
diff --git a/versioned_docs/version-1.14/tutorials/working-with-images.md b/versioned_docs/version-1.14/tutorials/working-with-images.md
new file mode 100644
index 0000000000..a573ccf761
--- /dev/null
+++ b/versioned_docs/version-1.14/tutorials/working-with-images.md
@@ -0,0 +1,187 @@
+---
+title: Working with Images
+---
+
+
+
+
+
+Rancher Desktop provides the ability to build, push, and pull images via the
+[NERDCTL](https://github.com/containerd/nerdctl) project and the Docker CLI.
+
+Note, both `nerdctl` and `docker` are put into the path automatically. This occurs during the installer on Windows, and upon first run on macOS and Linux.
+
+## General Usage
+
+Using either tool requires Rancher Desktop to be running with the appropriate container runtime. For `nerdctl`, use the containerd runtime. For `docker`, use the Moby runtime.
+
+You can learn about all of the command options and display the help documentation by running:
+
+
+
+
+```console
+nerdctl -h
+```
+
+Unlike Docker, containerd features its own namespaces. By default, nerdctl images are stored in the `default` namespace. If you want your images available for use by Kubernetes, use the `--namespace k8s.io` or `-n k8s.io` CLI argument. You can also switch to a namespace called `default` or any other name using the option `--namespace `. Note that nerdctl namespaces are separate and independent from Kubernetes and `kubectl` namespaces.
+
+
+
+
+```console
+docker --help
+```
+
+
+
+## Listing Images
+
+To see the images currently available, run the following command:
+
+
+
+
+```console
+nerdctl images
+```
+
+
+
+```console
+docker images
+```
+
+
+
+## Building Images
+
+
+
+
+Building images has a similar feel to existing tools. For example, consider
+running `nerdctl` from a directory with a `Dockerfile` where the `Dockerfile` is
+using a scratch image.
+
+```console
+nerdctl build .
+[+] Building 0.1s (4/4) FINISHED
+ => [internal] load build definition from Dockerfile
+ => => transferring dockerfile: 31B
+ => [internal] load .dockerignore
+ => => transferring context: 2B
+ => [internal] load build context
+ => => transferring context: 33B
+ => CACHED [1/1] ADD anvil-app /
+ ```
+
+`nerdctl` has options for tagging at the same time as building and other options you've
+come to expect.
+
+```console
+nerdctl build -t TAG .
+```
+
+To build an image for use with Kubernetes, specify the `k8s.io` namespace as follows:
+```console
+nerdctl build -n k8s.io .
+```
+
+
+
+
+Consider running `docker` from a directory with a `Dockerfile` where the `Dockerfile` is
+using a scratch image.
+
+```console
+docker build .
+Sending build context to Docker daemon 13.93MB
+Step 1/5 : FROM some-repo/some-image
+ ---> e57ace221dff
+...
+ ---> fd984c4cbf97
+Successfully built fd984c4cbf97
+```
+
+`docker` has options for tagging at the same time as building and other options you've
+come to expect.
+
+```console
+docker build -t TAG .
+```
+
+
+
+### Building Local Images
+
+In order to demonstrate the steps to build local images and run apps, a sample nodejs app is provided within the [Rancher Desktop docs repository](https://github.com/rancher-sandbox/docs.rancherdesktop.io.git). To get started, clone the repository and cd into `assets/express-sample` in a terminal.
+
+Run the following command to build image from Dockerfile:
+
+
+
+
+```
+nerdctl --namespace k8s.io build -t expressapp:v1.0 .
+```
+
+
+
+
+```
+docker build -t expressapp:v1.0 .
+```
+
+
+
+
+Run the following command to run container:
+
+```
+kubectl run --image expressapp:v1.0 expressapp
+kubectl port-forward pods/expressapp 3000:3000
+```
+
+**Note:** When adding the `latest` tag, be sure to also specify the following:
+```
+imagePullPolicy: Never
+```
+
+## Tagging Images
+
+If you want to tag an existing image you've built you can use the following
+command:
+
+
+
+
+```console
+nerdctl tag SOURCE_IMAGE[:TAG] TARGET_IMAGE[:TAG]
+```
+
+
+
+```console
+docker tag SOURCE_IMAGE[:TAG] TARGET_IMAGE[:TAG]
+```
+
+
+
+## Removing Images
+
+To remove an image, run the following command:
+
+
+
+
+```console
+nerdctl rmi IMAGE
+```
+
+
+
+```console
+docker rmi IMAGE
+```
+
+
\ No newline at end of file
diff --git a/versioned_docs/version-1.14/tutorials/working-with-webassembly.md b/versioned_docs/version-1.14/tutorials/working-with-webassembly.md
new file mode 100644
index 0000000000..b533066a45
--- /dev/null
+++ b/versioned_docs/version-1.14/tutorials/working-with-webassembly.md
@@ -0,0 +1,292 @@
+---
+title: Working with WebAssembly
+---
+
+
+
+
+
+Rancher Desktop 1.13.0 added experimental support for running WebAssembly (Wasm) applications. This feature needs to be enabled in [Preferences > Container Engine > General](../ui/preferences/container-engine/general.md).
+
+:::caution warning
+Note that when using the `moby` container engine, enabling the Wasm feature switches to a different image store, so previously built or downloaded images will not be available and must be built or downloaded again. The images are not lost; Rancher Desktop will switch back to the old image store when Wasm is disabled again.
+:::
+
+## Managing containerd Wasm shims
+
+Running WebAssembly applications on a container runtime requires a specific containerd "shim" for each Wasm runtime/framework used.
+
+Rancher Desktop 1.13 comes bundled with the `containerd-spin-shim-v2` shim preinstalled. Future releases are expected to download additional shims automatically when the feature is enabled.
+
+For now additional shims can be installed by the user into the `containerd-shims` cache directory on the host. The location is
+
+- Linux: `~/.local/share/rancher-desktop/containerd-shims`
+- macOS: `~/Library/Application Support/rancher-desktop/containerd-shims`
+- Windows: `%LOCALAPPDATA%\rancher-desktop\containerd-shims`
+
+Any shim installed there will automatically be copied into the VM and configured for the container engine when Rancher Desktop is started (installing a newer version of the `spin` shim will override the bundled version).
+
+## Developing Wasm Applications with Rancher Desktop
+
+Developing Wasm applications on your local machine on top of Rancher Desktop typically involves below steps:
+
+- Create an application in your programming language of choice. You can compile code written in many languages, such as C, C++, Rust, Go, and others, into Wasm modules
+- Compile the code into a Wasm module
+- Package the Wasm module as a OCI container image and push to a container registry
+- Run the Wasm container and/or
+- Deploy the Wasm container into Kubernetes
+
+### Creating a Simple App and Compiling It Into a Wasm Module
+
+You can use the Spin framework from Fermyon to quickly bootstrap a simple Wasm app. Install Spin on your machine following the instructions on the [Installing Spin](https://developer.fermyon.com/spin/v2/install) page.
+
+Once you have successfully installed Spin, create a new app via the command `spin new`.
+
+Select the language you would like to use for development.
+```console
+$spin new
+Pick a template to start your application with:
+ http-js (HTTP request handler using Javascript)
+> http-ts (HTTP request handler using Typescript)
+```
+
+Give a name to your app
+```console
+$spin new
+Pick a template to start your application with: http-ts (HTTP request handler using Typescript)
+Enter a name for your new application: rd-spin-hello-world
+```
+
+Provide an optional description and leave the API route path to default
+```console
+$spin new
+Pick a template to start your application with: http-ts (HTTP request handler using Typescript)
+Enter a name for your new application: rd-spin-hello-world
+Description []: This is a simple typescript app that will be compiled into a Wasm module and run as a Wasm container
+HTTP path: /...
+```
+
+Once the command ran successfully, you should see a directory created with the boilerplate code for the Spin app.
+
+Update the `index.ts` file to return a different message than the default.
+
+```console
+import { HandleRequest, HttpRequest, HttpResponse } from "@fermyon/spin-sdk"
+
+export const handleRequest: HandleRequest = async function (request: HttpRequest): Promise {
+ return {
+ status: 200,
+ headers: { "content-type": "text/plain" },
+ body: "Hello from Wasm container!"
+ }
+}
+```
+
+Change to the app directory and run the `spin build` command to compile the app code into a Wasm module.
+
+```console
+$spin build
+Building component rd-spin-hello-world with `npm run build`
+
+$ rd-spin-hello-world@1.0.0 build
+$ npx webpack --mode=production && mkdir -p target && spin js2wasm -o target/rd-spin-hello-world.wasm dist/spin.js
+
+asset spin.js 4.57 KiB [compared for emit] (name: main)
+runtime modules 670 bytes 3 modules
+./src/index.ts 2.86 KiB [built] [code generated]
+webpack 5.91.0 compiled successfully in 1355 ms
+
+Starting to build Spin compatible module
+Spin compatible module built successfully
+Finished building all Spin components
+```
+
+Once the build command ran successfully, you should see the `rd-spin-hello-world.wasm` module created inside the `target` directory.
+
+### Package the Wasm Module as an OCI Container Image and Push to a Container Registry
+
+Create a `Dockerfile` with below code to package the `Wasm` module as a docker image.
+
+```console
+FROM scratch
+COPY spin.toml /spin.toml
+COPY /target/rd-spin-hello-world.wasm /target/rd-spin-hello-world.wasm
+```
+
+Run the command below to package the Wasm module as a container image.
+
+
+
+
+```console
+nerdctl build \
+ --namespace k8s.io \
+ --platform wasi/wasm \
+ -t ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0 .
+```
+
+
+
+
+```console
+docker buildx build \
+ --load \
+ --platform wasi/wasm \
+ --provenance=false \
+ -t ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0 .
+```
+
+
+
+
+Push the image to the container registry
+
+
+
+
+```console
+nerdctl push ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0
+```
+
+
+
+
+```console
+docker push ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0
+```
+
+
+
+
+### Running the Wasm Container
+
+Running a Wasm container directly is currently only supported with the `moby` container engine; there is a bug in `nerdctl` that prevents it from working with `containerd`. Ensure you have selected `dockerd(moby)` as the container engine under [Preferences > Container Engine > General](../ui/preferences/container-engine/general.md) to work through the steps in this section.
+
+
+The following command runs the `rd-spin-hello-world` sample `spin` application, built in the previous section, on the `moby` engine (note the final `/` on the last line; it is the command to run, and `docker run` will fail if it is omitted):
+
+```console
+docker run \
+ --detach \
+ --name spin-demo \
+ --runtime io.containerd.spin.v2 \
+ --platform wasi/wasm \
+ --publish 8080:80 \
+ ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0 \
+ /
+```
+
+The internal port `80` has been mapped to `8080` and can be tested from the host:
+
+```console
+$ curl http://localhost:8080/
+Hello from Wasm container!
+```
+
+### Running Wasm Apps with Kubernetes
+
+Running WebAssembly applications on Kubernetes is currently only supported with the `containerd` runtime; it doesn't work with the `cri-dockerd` shim used to run Kubernetes on top of `moby`.
+
+Create a deployment for the sample Wasm container image built in the previous section:
+
+```console
+kubectl apply --filename - <kubectl get service traefik --namespace kube-system --output "jsonpath={.status.loadBalancer.ingress[0].ip}"
+192.168.127.2
+```
+
+The `sslip.io` "magic" DNS service can be used to create a corresponding DNS name for it: `192.168.127.2.sslip.io`. This name should be used instead of `localhost` in the Ingress spec `host` field.
+
+After deploying the deployment, service, and ingress the app should be available under this domain name:
+
+```
+C:\>curl http://192.168.127.2.sslip.io/hello
+Hello world from Spin!
+```
diff --git a/versioned_docs/version-1.14/ui/containers.md b/versioned_docs/version-1.14/ui/containers.md
new file mode 100644
index 0000000000..78979e2e77
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/containers.md
@@ -0,0 +1,69 @@
+---
+sidebar_label: Containers
+title: Containers
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+:::caution warning
+
+This is an **experimental** feature.
+
+:::
+
+The **Containers** tab offers quick access to manage containers and view key information such as:
+
+ - `State`:
+ The container state(s) will be listed in this field, and by default running containers are presented first.
+- `Name`:
+ The container name(s) will be listed in this field and can be sorted.
+- `Image`:
+ All image names will be listed in this field and can be sorted.
+- `Port(s)`:
+ Ports are listed in this field and can be clicked for quick access to a localhost port.
+- `Started`:
+ Container start-up times will be listed in this field and can be sorted.
+
+The listed information can be sorted in ascending or descending order. Containers can also be filtered with input text in the `Filter` field located at the top right. Bulk selection is available for managing multiple instances at once.
+
+Additionally, when using the `containerd` engine, you can use the `Namespace` dropdown selector to help with filtering containers. The dropdown will be located next to the `Filter` field and shows namespaces in your cluster when clicked.
+
+### Container Management
+
+The buttons located at the top of the page will be highlighted when a container is selected and depend on the container's state.
+
+Bulk selection and actions can also be performed on instances with the same state.
+
+The following actions are available:
+
+- `Stop`:
+ You can terminate container instances using the `Stop` button.
+- `Start`:
+ You can initiate container instances using the `Start` button.
+- `Delete`:
+ You can delete container instances from your system entirely by using the `Delete` button.
+- `⋮`:
+ This button is located on the right side of the tab view. You can start, stop, or delete container instances depending on their state using the `⋮` button.
diff --git a/versioned_docs/version-1.14/ui/diagnostics.md b/versioned_docs/version-1.14/ui/diagnostics.md
new file mode 100644
index 0000000000..962c6ebef1
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/diagnostics.md
@@ -0,0 +1,36 @@
+---
+sidebar_label: Diagnostics
+title: Diagnostics
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+The **Diagnostics** feature runs several checks in the background to detect common problems such as missing minimum requirements, misconfigurations, etc., in your environment to help you self-troubleshoot and fix Rancher Desktop application issues.
+
+**Note:** Rancher Desktop *doesn't* send the diagnostics data to any remote server for processing or storing.
+
+
+
+
+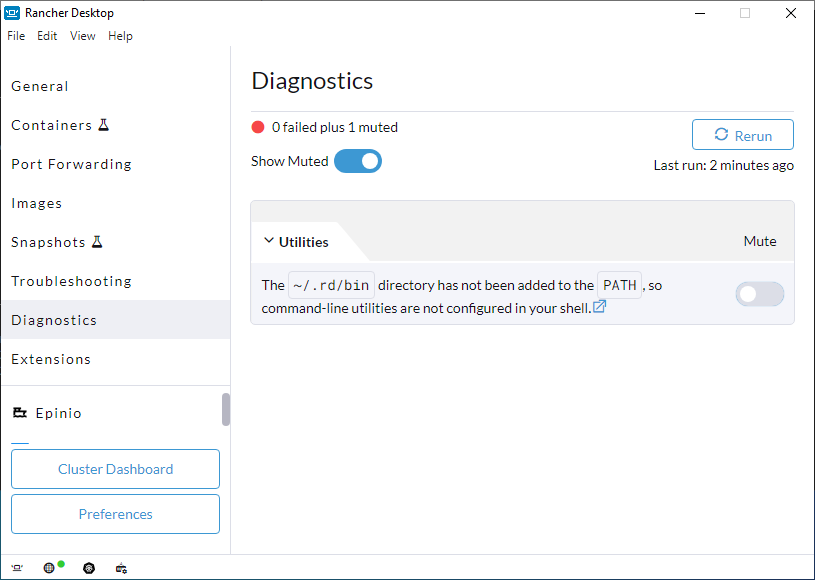
+
+
+
+
+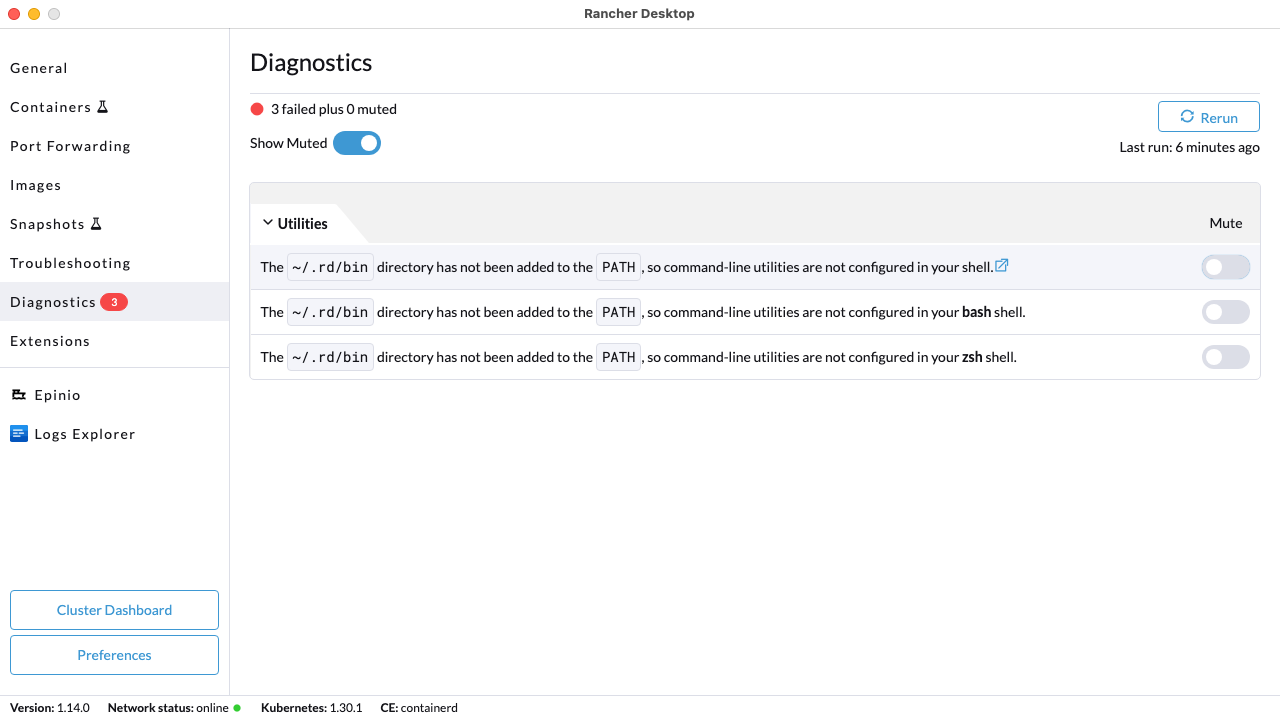
+
+
+
+
+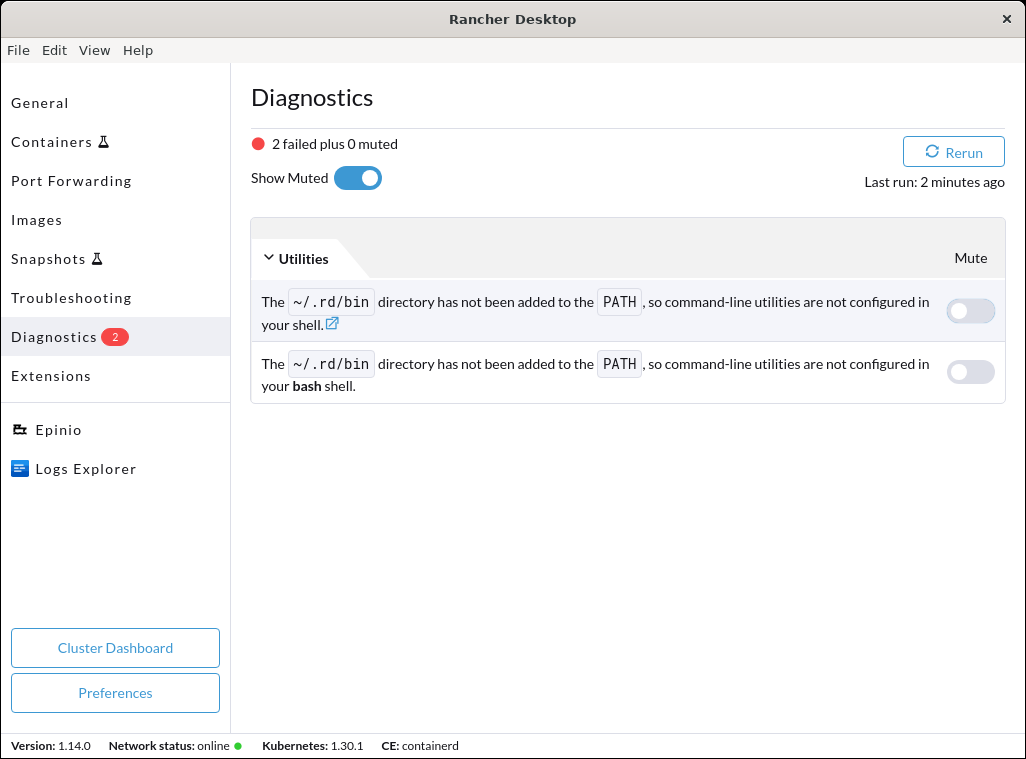
+
+
+
+
+The diagnostics checks are run every time when the application launches. If there are any problems identified then the count of failed checks is shown next to the *Diagnostics* menu text in the left navigation bar, indicating that something needs your attention. The *Diagnostics* tab displays the results of the diagnostics tests, highlighting areas that need attention, and guides you to resolve problems.
+
+On this tab you can mute/unmute individual checks if you have a non-standard setup and know that these checks don't apply to your situation. You can also rerun the diagnostics anytime to verify that changes you have made to your environment have rectified the problem.
diff --git a/versioned_docs/version-1.14/ui/extensions.md b/versioned_docs/version-1.14/ui/extensions.md
new file mode 100644
index 0000000000..f33cd23f0f
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/extensions.md
@@ -0,0 +1,66 @@
+---
+sidebar_label: Extensions
+title: Extensions
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+### Catalog
+
+The **Catalog** tab acts as a marketplace for available Rancher Desktop Extensions. Users can view and click on extensions for further description and the ability to install extensions directly through the UI.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+#### Search
+
+Users can make use of the **Search** functionality to query through available extensions.
+
+### Installed
+
+The **Installed** tab is a view for all installed extensions on your Rancher Desktop application.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+#### Name
+
+A list of names of installed extensions. Users can directly uninstall extensions by clicking the **Remove** button for the respective extension on the right hand side.
+
+### Remote Debugging Extensions
+
+The Chrome remote debugger allows you to debug Electron apps using Chrome Developer Tools. This tool can be used to also debug Docker extensions in Rancher Desktop. Please follow these instructions on [remote debugging an extension](https://github.com/rancher-sandbox/rancher-desktop/#remote-debugging-an-extension) installed in the application.
diff --git a/versioned_docs/version-1.14/ui/general.md b/versioned_docs/version-1.14/ui/general.md
new file mode 100644
index 0000000000..ba75bba503
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/general.md
@@ -0,0 +1,30 @@
+---
+sidebar_label: General
+title: General
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+The **General** tab provides information on communication channels where users can connect with the Rancher Desktop team and community to ask questions, report bugs, or discuss Rancher Desktop in general.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
diff --git a/versioned_docs/version-1.14/ui/images.md b/versioned_docs/version-1.14/ui/images.md
new file mode 100644
index 0000000000..92463a0dcf
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/images.md
@@ -0,0 +1,89 @@
+---
+sidebar_label: Images
+title: Images
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+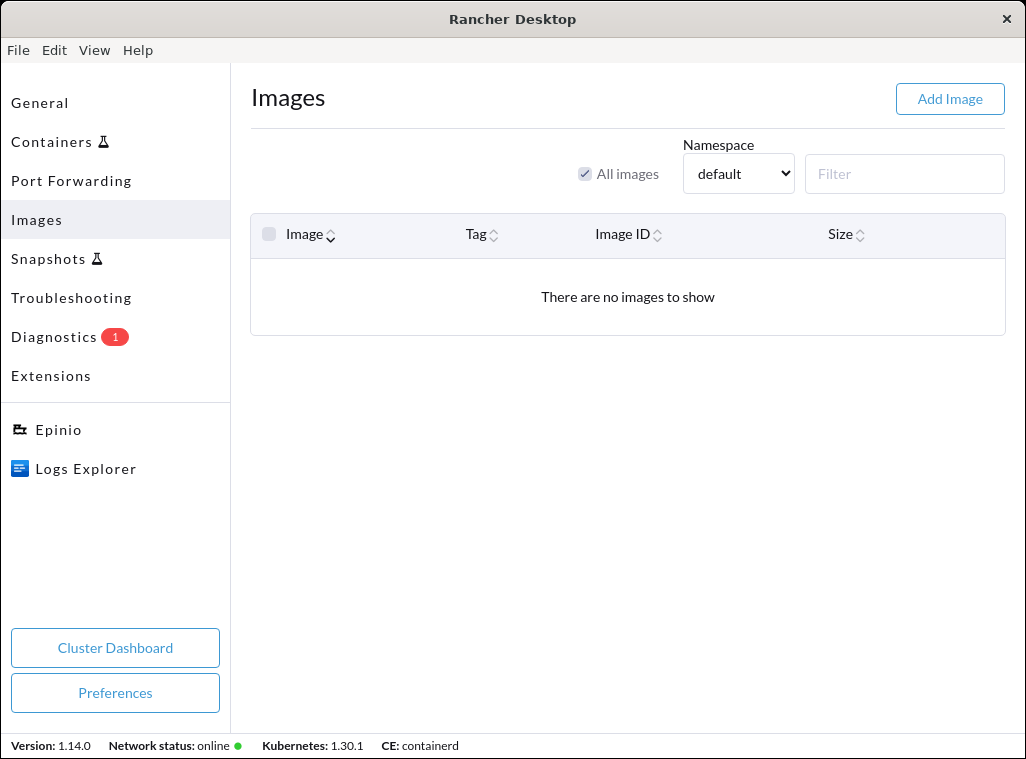
+
+
+
+
+The **Images** tab allows you to manage local container images via the application Graphical User Interface. Depending on the container engine selected, the options include:
+
+- Building container images from a local Dockerfile.
+- Pull images from a registry and push images to a registry.
+- Delete, and scan local images.
+
+To view how to manage container images using the command line, refer to the [Images section](../tutorials/working-with-images.md) in the Tutorials.
+
+### Image Management Options
+
+- `Delete`: This option is only available using the container engine `dockerd (moby)`. Images can be selected from the display view and deleted using the `Delete` button.
+
+- `All Images`: This option is only available using the container engine `containerd (nerdctl)` and `k8s.io` namespace. This checkbox can be marked to list all images including default application images in the `Rancher` resource group.
+
+- `Namespace`: This option is only available using the container engine `containerd (nerdctl)`. You can select a specific namespace in the cluster via the dropdown, which will then display the associated images.
+
+- `Filter`: Accepts either text or numbered input to display filtered images.
+
+### Scanning Images
+
+This feature uses [Trivy] to scan your images for vulnerabilities and configuration issues.
+
+To scan an image:
+
+1. From the image list, find the image you want to scan.
+1. Click **⋮ > Scan**.
+1. A summary of the vulnerabilities, sorted by the level of severity, are displayed.
+1. Click **>** to view the details of each vulnerability, including reference links to learn more about the particular vulnerability.
+
+[Trivy]:
+https://github.com/aquasecurity/trivy
+
+### Adding Images
+
+#### Pulling Images
+
+Use this option to pull images from a registry to your virtual machine.
+
+To pull an image:
+
+1. Click the **Add Image** button in the top-right corner.
+1. Click on the **Pull** tab.
+1. Enter the name of the image to pull.
+ > Note: By default, images are pulled from [Docker Hub] which uses the `repo/image[:tag]` format. To pull from other registries, include the hostname `registry.example.com/repo/image[:tag]`.
+1. Click **Pull**.
+
+[Docker Hub]:
+https://hub.docker.com/
+
+#### Building Images
+
+Use this option to build an image and add it to your virtual machine.
+
+To build an image:
+
+1. Click the **Add Image** button in the top-right corner.
+1. Click on the **Build** tab.
+1. Enter a name for the image being built. E.g., `repo/image`, `repo/image:tag`, `registry.example.com/repo/image`, or `registry.example.com/repo/image:tag`.
+1. Click **Build**.
+1. In the file browser, select the Dockerfile to build an image with.
diff --git a/versioned_docs/version-1.14/ui/port-forwarding.md b/versioned_docs/version-1.14/ui/port-forwarding.md
new file mode 100644
index 0000000000..1a8a515f3c
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/port-forwarding.md
@@ -0,0 +1,47 @@
+---
+sidebar_label: Port Forwarding
+title: Port Forwarding
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+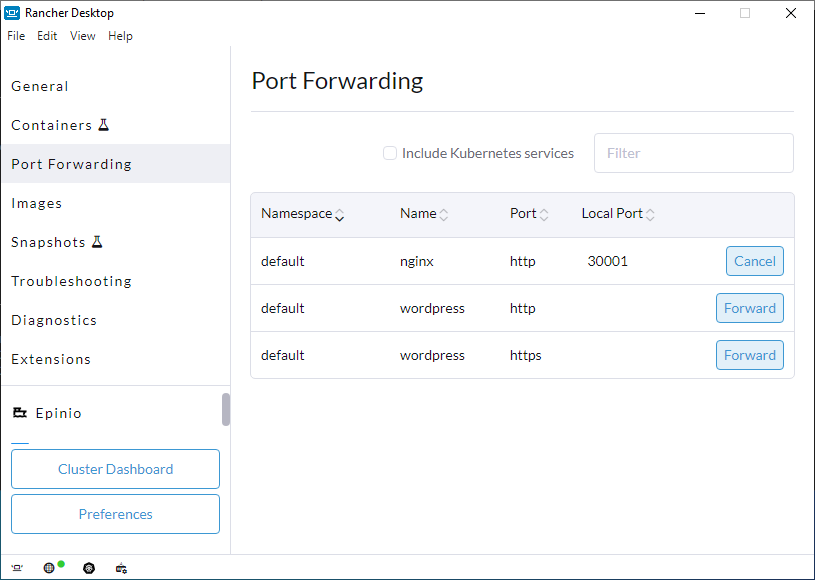
+
+
+
+
+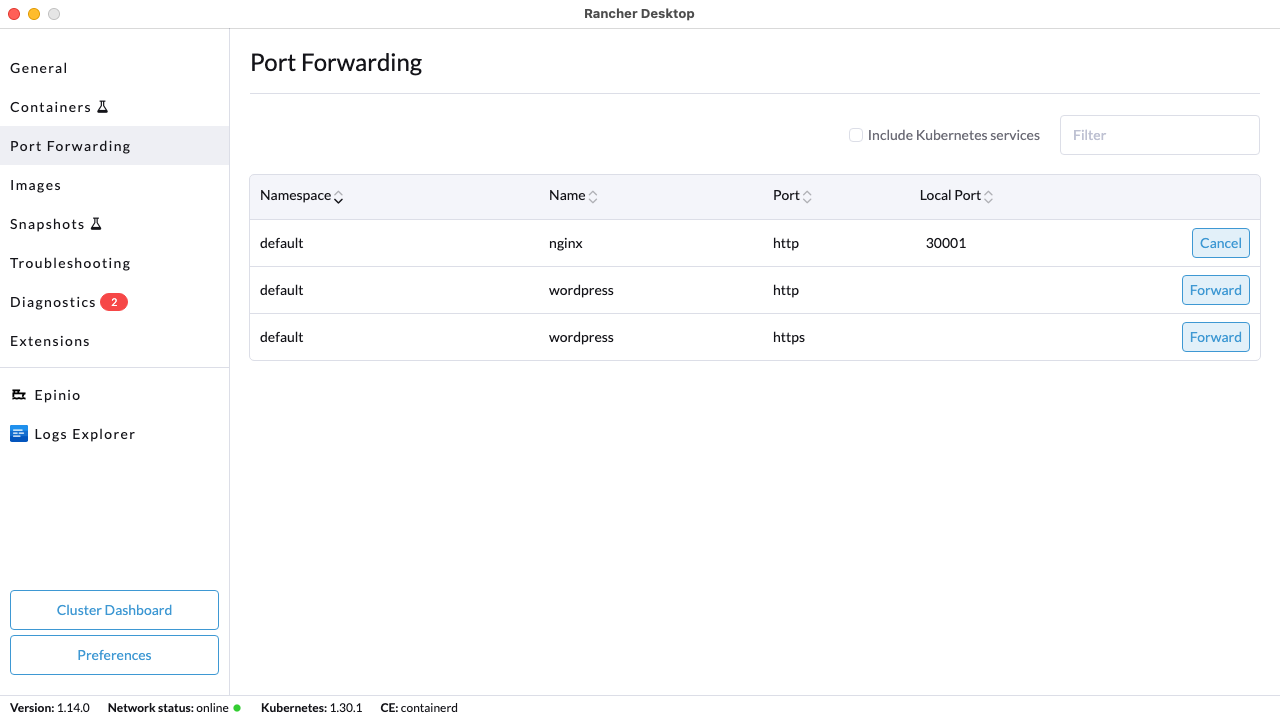
+
+
+
+
+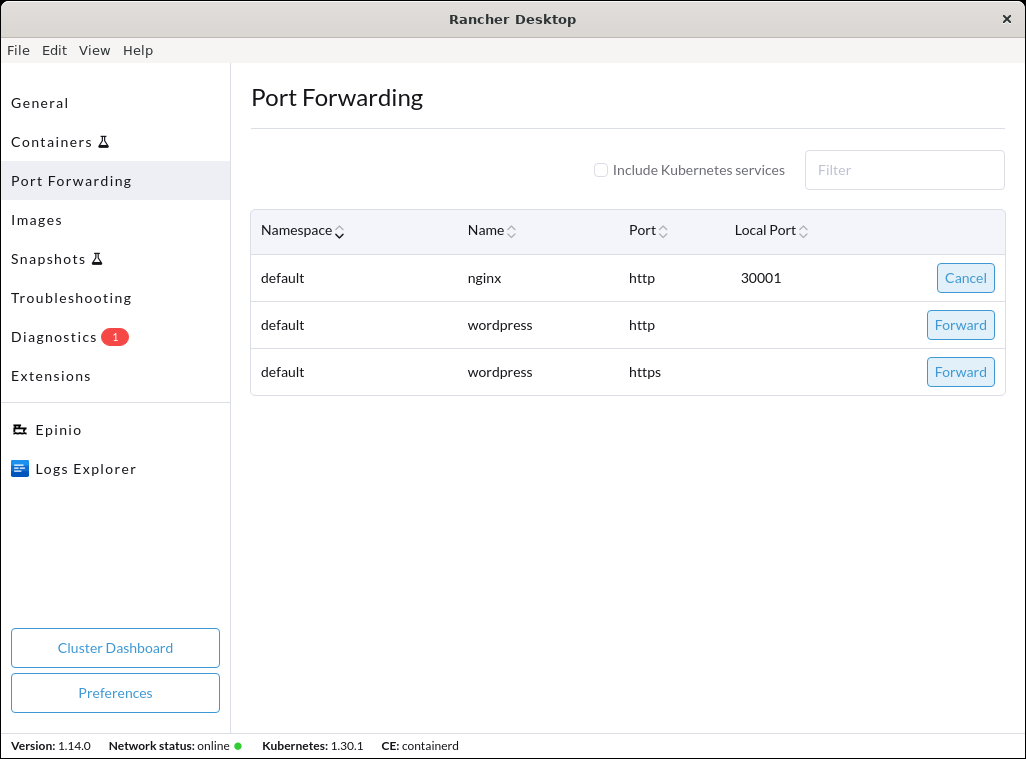
+
+
+
+
+### How to Forward a Port
+
+The steps below outline how to forward a port:
+
+1. Find the service and click **Forward**.
+1. Specify a port to use or use the randomly assigned port.
+1. Click the ✓ button to confirm your selection.
+1. Optional: click **Cancel** to remove the port assigned.
+
+### Admin vs Non-Admin Port Mappings
+
+Rancher Desktop includes automated port forwarding for versions `1.9` and later. For non-admin port access, port mappings are configured to the localhost and unprivileged ports `> 1024`. Privileged port mappings can also be configured by users with admin permissions for ports `<= 1024`.
+
+:::note
+
+Please see [Traefik Port Binding Access](../getting-started/installation.md#traefik-port-binding-access) to configure ports at the operating system level.
+
+:::
diff --git a/versioned_docs/version-1.14/ui/preferences/application/behavior.md b/versioned_docs/version-1.14/ui/preferences/application/behavior.md
new file mode 100644
index 0000000000..bae2c87703
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/application/behavior.md
@@ -0,0 +1,90 @@
+---
+sidebar_label: Behavior
+title: Behavior
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Allows for configuration of application behavior upon startup, background process behavior, and notification icon display.
+
+
+
+
+
+
+#### Startup
+
+Rancher Desktop can automatically be started as part of the user login process. This will take all other behavior settings from the page into account as well.
+
+#### Background
+
+When Rancher Desktop is started in the background, it will not have an application window, nor an entry in the task switcher or task bar. The application window can still be opened via the context menu of the notification icon.
+
+When Rancher Desktop is launched again while already running in the background then the application window is shown and the application is added to the task switcher and task bar. This can be used to gain access to the background application again when the notification icon is unavailable as well.
+
+Rancher Desktop normally remains running in the background even when the main application window is closed (and the application therefore removed from the task switcher and task bar), but can be configured to terminate the application as well when the main window is closed.
+
+#### Notification Icon
+
+Rancher Desktop shows the application status with a notification icon. The context menu of the icon provides more status information and provides quick access to other functionality of the application. This options will disable the creation of the notification icon.
+
+#### Known Issues and Limitations
+
+* For Ubuntu operating systems and specifically versions >= 20.04.5 LTS, there is a known issue with hiding the tray icon in the preferences settings. Please see this [issue comment](https://github.com/rancher-sandbox/rancher-desktop/issues/4205#issuecomment-1533750167) for further information.
+
+
+
+
+
+
+#### Startup
+
+Rancher Desktop can automatically be started as part of the user login process. This will take all other behavior settings from the page into account as well.
+
+#### Background
+
+When Rancher Desktop is started in the background, it will not have an application window, nor an entry in the app switcher or the dock. The application window can still be opened via the context menu of the notification icon in the menu bar.
+
+When Rancher Desktop is launched again while already running in the background then the application window is shown and the application is added to the app switcher and the dock. This can be used to gain access to the background application again when the notification icon is unavailable as well.
+
+Rancher Desktop normally remains running in the background even when the main application window is closed (and the application therefore removed from the app switcher and the dock), but can be configured to terminate the application as well when the main window is closed.
+
+#### Notification Icon
+
+Rancher Desktop shows the application status with a notification icon in the menu bar. The context menu of the icon provides more status information and provides quick access to other functionality of the application. This options will disable the creation of the notification icon.
+
+#### Known Issues and Limitations
+
+* For Ubuntu operating systems and specifically versions >= 20.04.5 LTS, there is a known issue with hiding the tray icon in the preferences settings. Please see this [issue comment](https://github.com/rancher-sandbox/rancher-desktop/issues/4205#issuecomment-1533750167) for further information.
+
+
+
+
+
+
+#### Startup
+
+Rancher Desktop can automatically be started as part of the user login process. This will take all other behavior settings from the page into account as well.
+
+#### Background
+
+When Rancher Desktop is started in the background, it will not have an application window, nor an entry in the task switcher or task bar. The application window can still be opened via the context menu of the notification icon.
+
+When Rancher Desktop is launched again while already running in the background then the application window is shown and the application is added to the task switcher and task bar. This can be used to gain access to the background application again when the notification icon is unavailable as well.
+
+Rancher Desktop normally remains running in the background even when the main application window is closed (and the application therefore removed from the task switcher and task bar), but can be configured to terminate the application as well when the main window is closed.
+
+#### Notification Icon
+
+Rancher Desktop shows the application status with a notification icon. The context menu of the icon provides more status information and provides quick access to other functionality of the application. This options will disable the creation of the notification icon.
+
+#### Known Issues and Limitations
+
+* For Ubuntu operating systems and specifically versions >= 20.04.5 LTS, there is a known issue with hiding the tray icon in the preferences settings. Please see this [issue comment](https://github.com/rancher-sandbox/rancher-desktop/issues/4205#issuecomment-1533750167) for further information.
+
+
+
diff --git a/versioned_docs/version-1.14/ui/preferences/application/environment.md b/versioned_docs/version-1.14/ui/preferences/application/environment.md
new file mode 100644
index 0000000000..f6c3dcadf5
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/application/environment.md
@@ -0,0 +1,47 @@
+---
+sidebar_label: Environment
+title: Environment
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Allows for configuration of the `$PATH` variable in the users shell in order to interact with Rancher Desktop installed utilities.
+
+
+
+
+
+
+#### Configure PATH
+
+A Rancher Desktop installation comes with command-line utilities that are used to interface with its various features. Some examples of these utilities are `docker`, `nerdctl`, `kubectl`, and `helm`. These utilities are located in `~/.rd/bin` - you may see which utilities are included in your installation by running `ls ~/.rd/bin`.
+
+In order to use the utilities, `~/.rd/bin` must be in the `PATH` variable in your shell.
+
+There are two options for doing this:
+
+- **Automatic**: `PATH` management will add `~/.rd/bin` to your `PATH` by modifying your shell .rc files for you.
+- **Manual**: `PATH` management does not change anything - in this mode, you must add `~/.rd/bin` to your `PATH` yourself.
+
+
+
+
+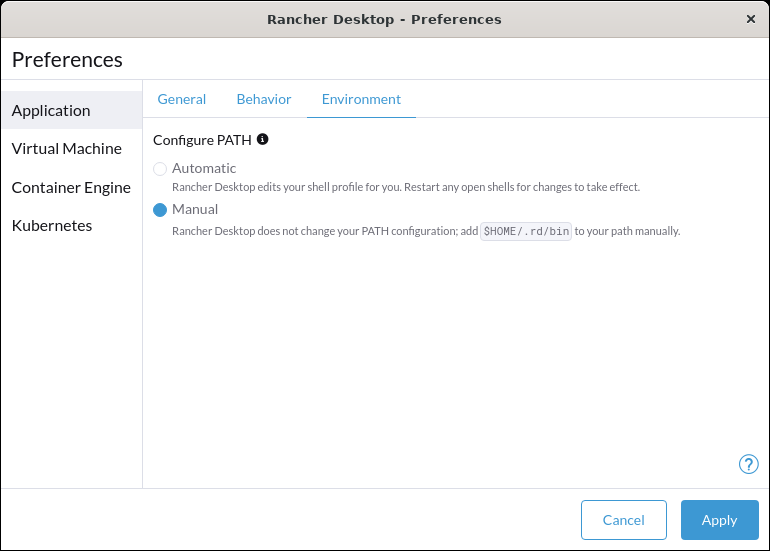
+
+#### Configure PATH
+
+A Rancher Desktop installation comes with command-line utilities that are used to interface with its various features. Some examples of these utilities are `docker`, `nerdctl`, `kubectl`, and `helm`. These utilities are located in `~/.rd/bin` - you may see which utilities are included in your installation by running `ls ~/.rd/bin`.
+
+In order to use the utilities, `~/.rd/bin` must be in the `PATH` variable in your shell.
+
+There are two options for doing this:
+
+- **Automatic**: `PATH` management will add `~/.rd/bin` to your `PATH` by modifying your shell .rc files for you.
+- **Manual**: `PATH` management does not change anything - in this mode, you must add `~/.rd/bin` to your `PATH` yourself.
+
+
+
diff --git a/versioned_docs/version-1.14/ui/preferences/application/general.md b/versioned_docs/version-1.14/ui/preferences/application/general.md
new file mode 100644
index 0000000000..0a1d928bc8
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/application/general.md
@@ -0,0 +1,68 @@
+---
+sidebar_label: General
+title: General
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Allows for enablement of automatic updates, as well as an optional field to allow Rancher Desktop to collect anonymous statistics to help improve the application.
+
+
+
+
+
+
+#### Automatic Updates
+
+Ensure you have the setting checked and enabled on the `Preferences > Application > General` tab. You will need to click `Apply` once selected, and then manually restart the application for the settings to update.
+
+If a new release is available, it will be downloaded upon restart and you will see a section denoted `Update Available` from the main [General](../../../ui/general.md) tab with a `Restart` button that can be clicked to have the newest version applied. A copy of the latest version’s release notes will be displayed via dropdown as well.
+
+#### Statistics
+
+This option allows Rancher Desktop to collect information on how you interact with the Rancher Desktop application. Information such as what workloads you run are not collected.
+
+
+
+
+
+
+#### Administrative Access
+
+Allows Rancher Desktop to acquire administrative access (sudo access) when starting for some operations. This allows for enhanced functionality, including bridged networking and default docker socket support. Changes will only be applied next time Rancher Desktop starts.
+
+#### Automatic Updates
+
+Ensure you have the setting checked and enabled on the `Preferences > Application > General` tab. You will need to click `Apply` once selected, and then manually restart the application for the settings to update.
+
+If a new release is available, it will be downloaded upon restart and you will see a section denoted `Update Available` from the main [General](../../../ui/general.md) tab with a `Restart` button that can be clicked to have the newest version applied. A copy of the latest version’s release notes will be displayed via dropdown as well.
+
+#### Statistics
+
+This option allows Rancher Desktop to collect information on how you interact with the Rancher Desktop application. Information such as what workloads you run are not collected.
+
+
+
+
+
+
+#### Administrative Access
+
+Allows Rancher Desktop to acquire administrative access (sudo access) when starting for some operations. This allows for enhanced functionality, including bridged networking and default docker socket support. Changes will only be applied next time Rancher Desktop starts.
+
+#### Automatic Updates
+
+Ensure you have the setting checked and enabled on the `Preferences > Application > General` tab. You will need to click `Apply` once selected, and then manually restart the application for the settings to update.
+
+If a new release is available, it will be downloaded upon restart and you will see a section denoted `Update Available` from the main [General](../../../ui/general.md) tab with a `Restart` button that can be clicked to have the newest version applied. A copy of the latest version’s release notes will be displayed via dropdown as well.
+
+#### Statistics
+
+This option allows Rancher Desktop to collect information on how you interact with the Rancher Desktop application. Information such as what workloads you run are not collected.
+
+
+
diff --git a/versioned_docs/version-1.14/ui/preferences/container-engine/allowed-images.md b/versioned_docs/version-1.14/ui/preferences/container-engine/allowed-images.md
new file mode 100644
index 0000000000..514e9fbb76
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/container-engine/allowed-images.md
@@ -0,0 +1,58 @@
+---
+sidebar_label: Allowed Images
+title: Allowed Images
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+The `Allowed Images` tab lets you control which registry artifacts you can access within Rancher Desktop. For example, you may want to pull container images only from your organization's private registry or only from your department-specific namespace in your organization's registry, etc. You can specify image name patterns to allow accessing images only from specific registries and/or repositories.
+
+
+
+
+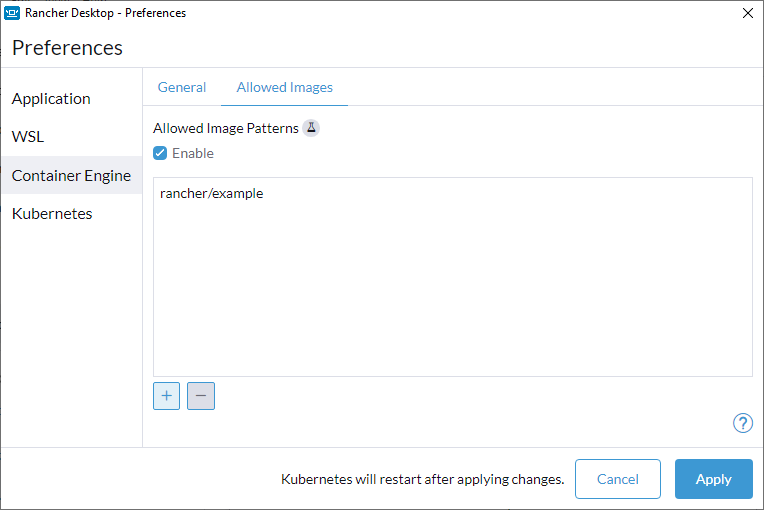
+
+
+
+
+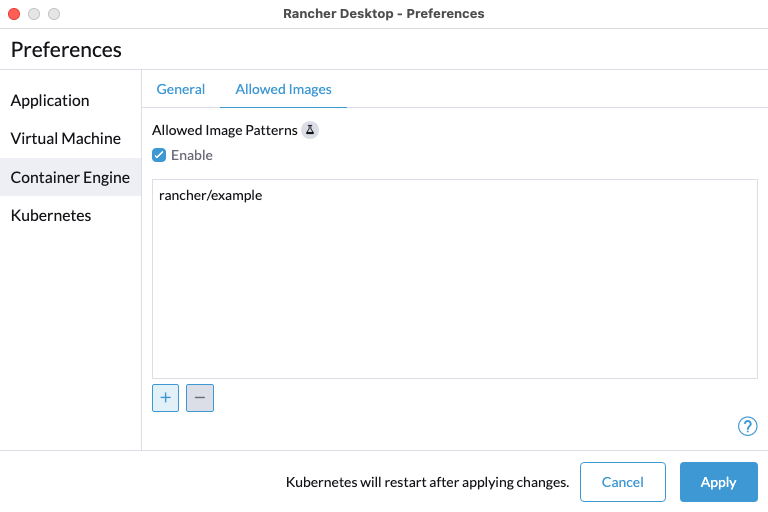
+
+
+
+
+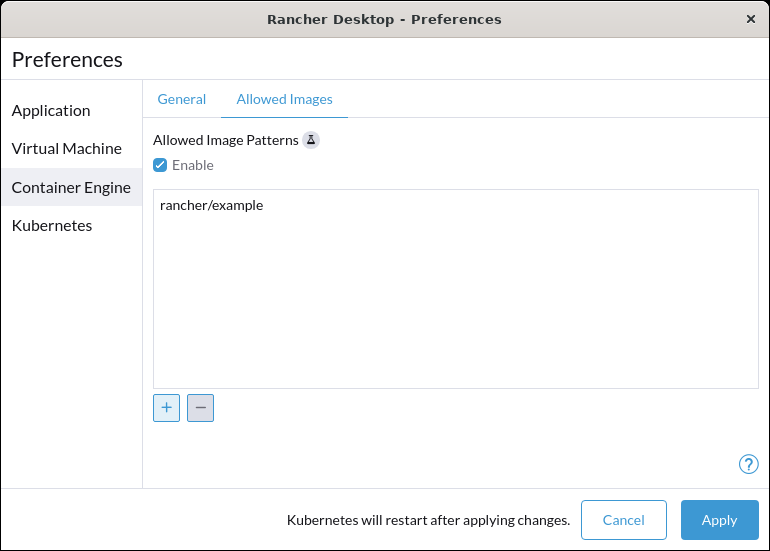
+
+
+
+
+#### Allowed image patterns
+
+Check the **Enable** checkbox to enable Rancher Desktop to apply the specified patterns while pulling or pushing images, which means only images whose names match at least one of the specified patterns will be allowed.
+
+You can use the **+** and **-** buttons to add/remove image name patterns.
+
+##### How to specify Allowed Image patterns
+
+You can specify Allowed Image patterns using the format `[registry/][:port/][organization/]repository[:tag]`.
+
+> If not specified in an Allowed Image pattern,
+> * `registry` defaults to Docker Hub (`docker.io`).
+> * `port` defaults to 443.
+> * `organization` for Docker Hub defaults to `library`, and does not apply to other registries.
+> * `tag` defaults to anything and **not** just to `latest`.
+
+**Note:** Filtering by `tag` does not actually work; the corresponding digests (`repository@digest`) will have to be added to the allow list as well, making this impractical. Please file a Github issue if you have a use-case that requires filtering based on tags!
+
+#### Examples
+
+| Pattern | Meaning |
+|---------------------------|---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
+| `busybox` | Allow the `busybox` repository in the `library` organization of the `docker.io` registry. |
+| `suse/` | Allow any image in the `suse` organization of the `docker.io` registry. **Note:** A trailing slash at the end of the repository means a single segment follows, e.g. `suse/nginx`, but not `suse/cap/uaa`. |
+| `suse//` | Allow any image in the `suse` organization of the `docker.io` registry. **Note:** A trailing double slash at the end of the repository means one or more segments follow, e.g. `suse/cap/uaa`. |
+| `registry.internal:5000` | Allow any image from the `registry.internal:5000` registry. |
+| `registry.suse.com/nginx` | Allow the image `nginx` from the `registry.suse.com` registry. **Note:** Non-DockerHub registries do not have the concept of organizations at the top level, so no default `library` organization is implied. |
diff --git a/versioned_docs/version-1.14/ui/preferences/container-engine/general.md b/versioned_docs/version-1.14/ui/preferences/container-engine/general.md
new file mode 100644
index 0000000000..9d3401c41e
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/container-engine/general.md
@@ -0,0 +1,61 @@
+---
+sidebar_label: General
+title: General
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+Set the [container runtime] for Rancher Desktop. Users have the option of [containerd] which provides namespaces for containers and the use of nerdctl or [dockerd (moby)] which enables the Docker API and the use of the Docker CLI. Only one container runtime will function at a time.
+
+
+
+
+
+
+
+
+
+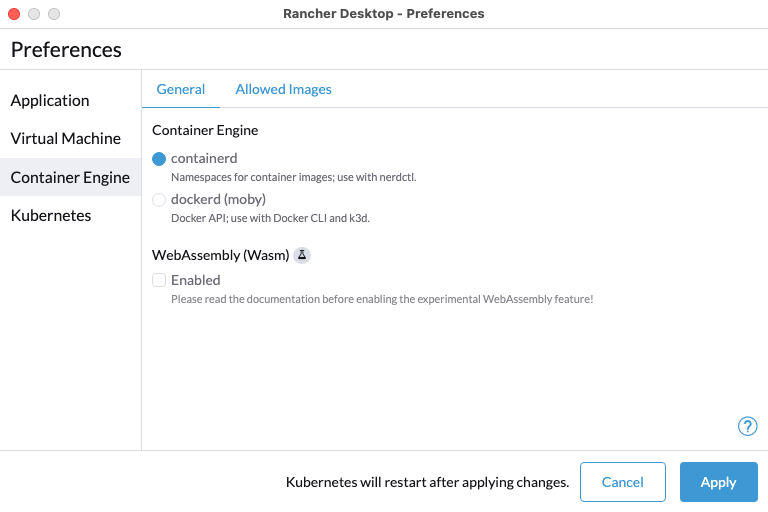
+
+
+
+
+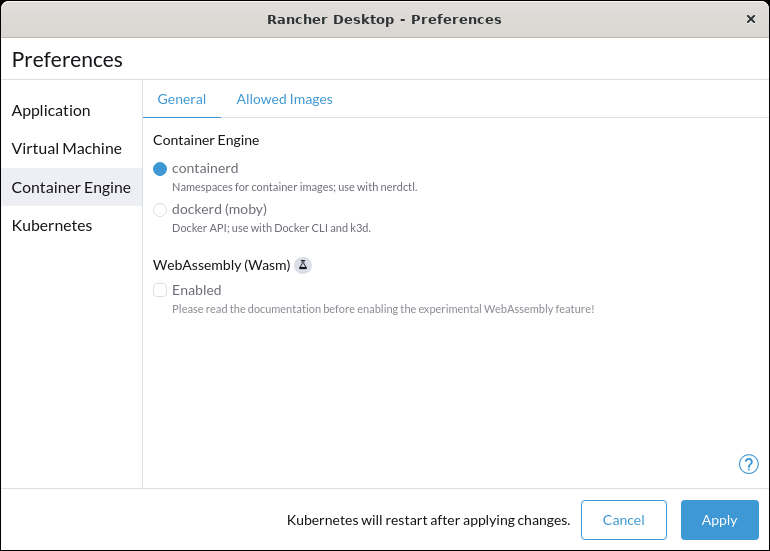
+
+
+
+
+#### Container Engine
+
+When switching to a different container runtime: Workloads and images that have been built or pulled using the current container runtime are not available on the container runtime being switched to.
+
+#### WebAssembly (Wasm)
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+The Wasm feature allows running WebAssembly application as containers, either directly with the container engine, or via Kubernetes. Details are available in the [Working with WebAssembly](../../../tutorials/working-with-webassembly.md) tutorial.
+
+:::caution warning
+Note that when using the `moby` container engine, enabling the Wasm feature switches to a different image store, so previously built or downloaded images will not be available and must be built or downloaded again. The images are not lost; Rancher Desktop will switch back to the old image store when Wasm is disabled again.
+:::
+
+:::info
+If the machine has a [Locked Deployment Profile](../../../getting-started/deployment.md) installed, then the Wasm feature will be disabled and locked unless the profile uses schema version `11` or later.
+:::
+
+[container runtime]:
+https://kubernetes.io/docs/setup/production-environment/container-runtimes/
+
+[containerd]:
+https://containerd.io/
+
+[dockerd (moby)]:
+https://mobyproject.org/
diff --git a/versioned_docs/version-1.14/ui/preferences/kubernetes.md b/versioned_docs/version-1.14/ui/preferences/kubernetes.md
new file mode 100644
index 0000000000..38146b7183
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/kubernetes.md
@@ -0,0 +1,84 @@
+---
+sidebar_label: Kubernetes
+title: Kubernetes
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+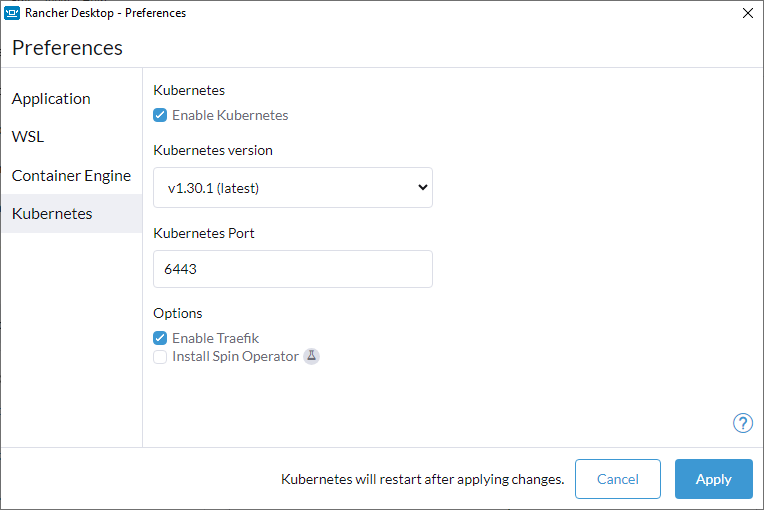
+
+
+
+
+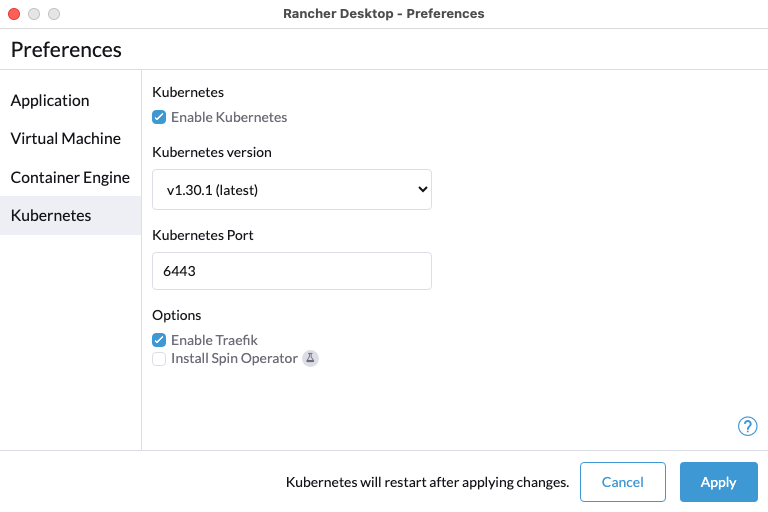
+
+
+
+
+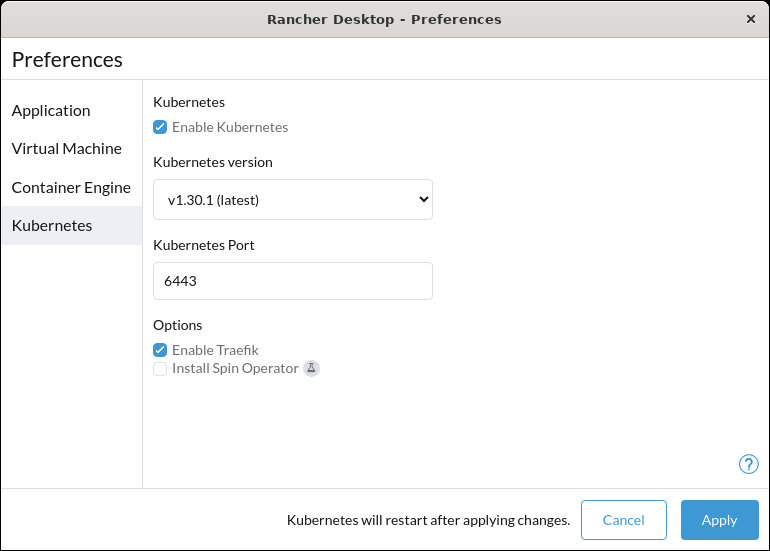
+
+
+
+
+#### Enable Kubernetes
+
+This option allows you to enable or disable Kubernetes. By disabling Kubernetes, you can run just `containerd` or `dockerd` by itself for reduced resource consumption. By default, Kubernetes is enabled.
+
+To enable/disable Kubernetes, just check/uncheck the `Enable Kubernetes` checkbox. The app will be restarted when you enable/disable Kubernetes. Disabling Kubernetes will not delete existing resources and they will be available again when you enable Kubernetes again.
+
+#### Kubernetes Version
+
+This option presents a list of Kubernetes versions that your Rancher Desktop instance can use.
+
+When upgrading:
+
+- A check is performed to see if the target Kubernetes version is available locally. If not, it downloads the files.
+- Workloads are retained.
+- Images are retained.
+
+When downgrading:
+
+- Workloads are removed.
+- Images are retained.
+
+To switch versions:
+
+1. Click the **Kubernetes version** drop-down menu.
+1. Select the version you want to change to.
+
+#### Kubernetes Port
+
+Set the port Kubernetes is exposed on. Use this setting to avoid port collisions if multiple instances of K3s are running.
+
+#### Options
+
+##### Enable Traefik
+
+This option allows you to enable or disable Traefik. By disabling Traefik, you can free up port 80 and 443 for alternate ingress configuration. By default, Traefik is enabled.
+
+Disabling Traefik will not delete existing resources.
+
+##### Install Spin Operator
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+This option will install the [spinkube](https://www.spinkube.dev/) operator with the `cert-manager` prerequisite, and configure it with the `spin` RuntimeClass.
+
+This option requires that the [WebAssembly](./container-engine/general.md) support is enabled.
+
+:::note
+
+Rancher Desktop automatically installs the [spin cli](https://developer.fermyon.com/spin/v2/index) and the [kube plugin](https://github.com/spinkube/spin-plugin-kube) to help develop and deploy Spin applications on Kubernetes.
+
+:::
diff --git a/versioned_docs/version-1.14/ui/preferences/virtual-machine/emulation.md b/versioned_docs/version-1.14/ui/preferences/virtual-machine/emulation.md
new file mode 100644
index 0000000000..1665fbebf8
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/virtual-machine/emulation.md
@@ -0,0 +1,28 @@
+---
+sidebar_label: Emulation
+title: Emulation (macOS)
+---
+
+
+
+
+
+### QEMU
+
+ 
+
+The [**QEMU**](https://www.qemu.org/documentation/) option is enabled by default and turns on a guest operating system. You can switch the virtual machine type after the first run.
+
+### VZ
+
+ 
+
+:::caution warning
+
+This is an *experimental* setting. The setting is available for ARM machines on macOS 13.3 or later, and Intel machines on macOS 13.0 or later.
+
+:::
+
+You can also enable the **VZ** option to use the native macOS [Virtualization.Framework](https://developer.apple.com/documentation/virtualization) for running a guest machine.
+
+The suboption **VZ option** can also be enabled if using **VZ** as your virtual machine type. The suboption enables [Rosetta support](https://developer.apple.com/documentation/virtualization/running_intel_binaries_in_linux_vms_with_rosetta) and allows users to run applications that contain x86_64 instructions on Apple hardware.
diff --git a/versioned_docs/version-1.14/ui/preferences/virtual-machine/hardware.md b/versioned_docs/version-1.14/ui/preferences/virtual-machine/hardware.md
new file mode 100644
index 0000000000..d813e1884a
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/virtual-machine/hardware.md
@@ -0,0 +1,31 @@
+---
+sidebar_label: Hardware
+title: Hardware (macOS & Linux)
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+### Memory
+
+The amount of memory to allocate to Rancher Desktop. The selectable range is based on your system. The red area within the range indicates an allocation that may affect system services.
+
+### CPUs
+
+The number of CPUs to allocate to Rancher Desktop. The selectable range is based on your system. The red area within the range indicates an allocation that may affect system services.
diff --git a/versioned_docs/version-1.14/ui/preferences/virtual-machine/network.md b/versioned_docs/version-1.14/ui/preferences/virtual-machine/network.md
new file mode 100644
index 0000000000..39158d4b62
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/virtual-machine/network.md
@@ -0,0 +1,30 @@
+---
+sidebar_label: Network
+title: Network (macOS)
+---
+
+
+
+
+
+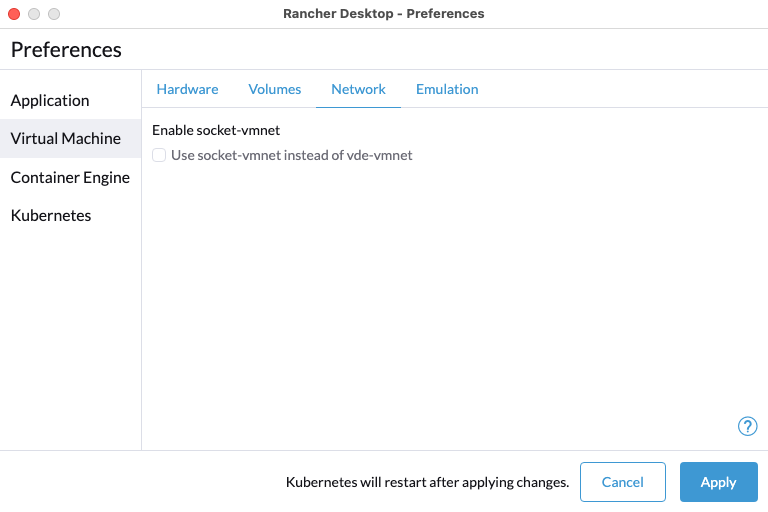
+
+### Enable `socket-vmnet`
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+Network settings can be enabled or disabled from this view. Users have the initial option of enabling `socket-vmnet` which will allow for adding another guest IP that is accessible from the host and other guests. The enabled option also provides [`vmnet` framework](https://developer.apple.com/documentation/vmnet) support for QEMU and does not depend on VDE.
+
+### `vmnet` and `mDNSResponder`
+
+When using the `vmnet` framework with Rancher Desktop, the macOS component [`mDNSResponder`](https://github.com/apple-oss-distributions/mDNSResponder#mdns-responder-daemon) will automatically start and make use of your machine's port `53`. The port is used to get a routable IP address for the virtual machine running the application's container engine.
+
+If you need access to port `53`, or do not wish to make use of routable IP addresses, then you can achieve this by disabling [`Administrative Access`](../../../ui/preferences/application/general.md#administrative-access) from the *Preferences* dialog. Using `vmnet` requires starting a daemon via `sudo`, and with administrative access removed this will free port `53` from the `mDNSResponder` daemon.
+
+:::caution warning
+Please note that with `Administrative Access` disabled, Rancher Desktop will no longer be able to create the Docker socket in the default location at `/var/run/docker.sock`. Instead, the application will create a [`docker context`](https://docs.docker.com/engine/context/working-with-contexts/) called `rancher-desktop` and switch to it automatically. Please be aware of this in the event you are running software that expects the default location and may not know about `docker contexts`.
+:::
diff --git a/versioned_docs/version-1.14/ui/preferences/virtual-machine/volumes.md b/versioned_docs/version-1.14/ui/preferences/virtual-machine/volumes.md
new file mode 100644
index 0000000000..6ab5093fc6
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/virtual-machine/volumes.md
@@ -0,0 +1,87 @@
+---
+sidebar_label: Volumes
+title: Volumes (macOS & Linux)
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+## Mount Type
+
+### reverse-sshfs
+
+
+
+
+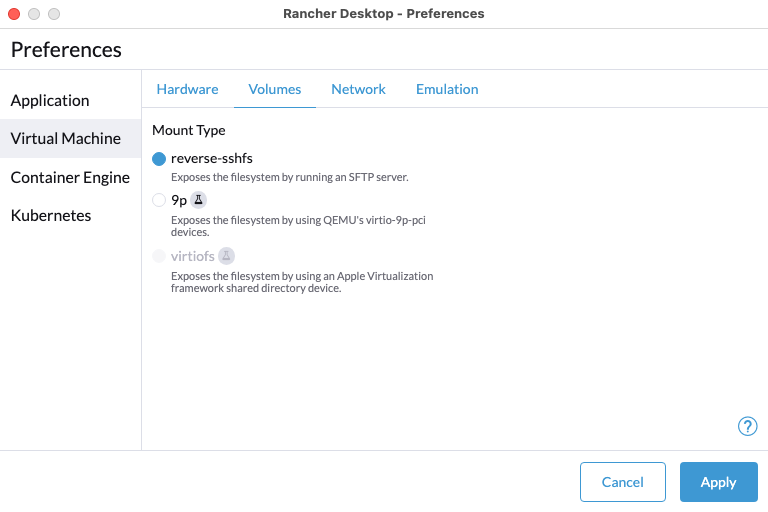
+
+
+
+
+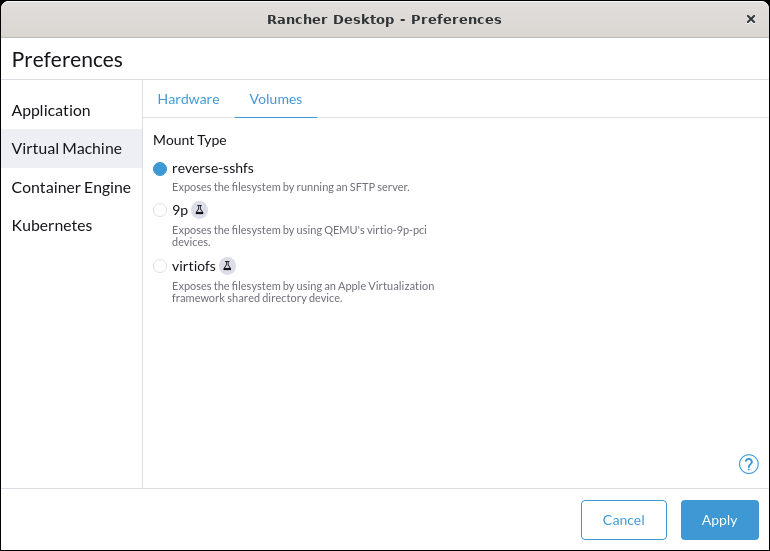
+
+
+
+
+Users can enable the "[reverse-sshfs](https://github.com/lima-vm/lima/blob/master/docs/mount.md#reverse-sshfs)" mount type from the `Volumes` tab. This exposes the filesystem by running an SFTP server on the host. The host instance will then intitiate an SSH connection into the guest allowing it to connect to the SFTP server. This is the default mount type used in the application.
+
+### 9p
+
+
+
+
+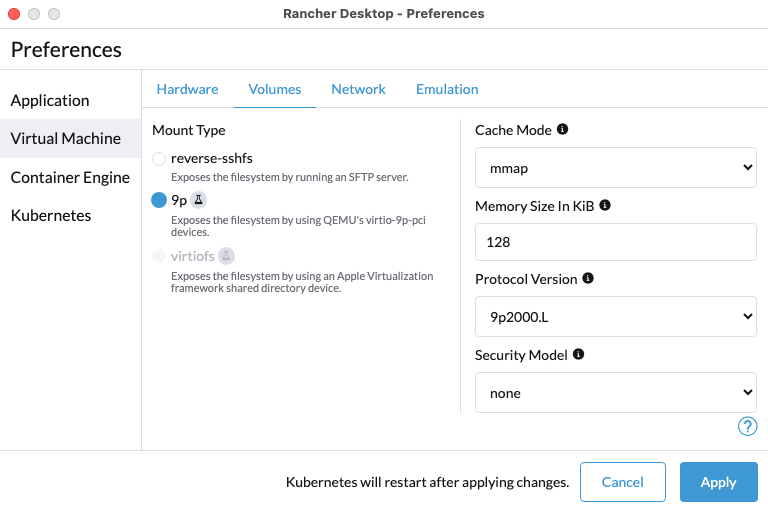
+
+
+
+
+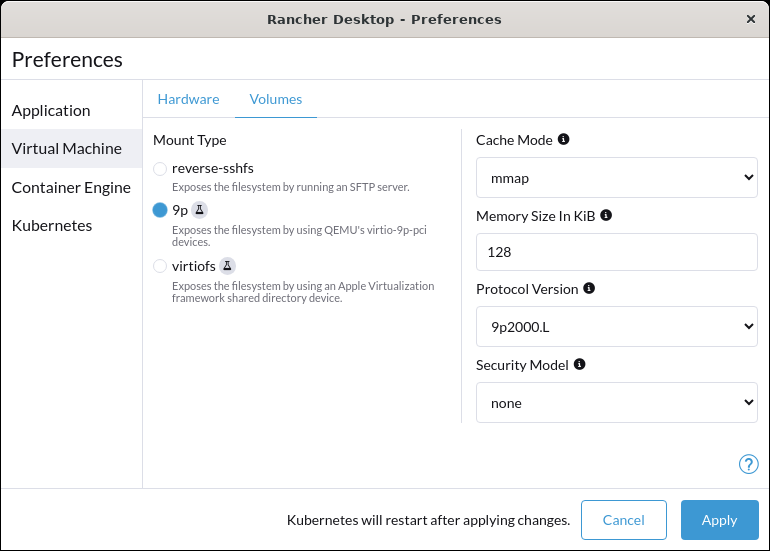
+
+
+
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+Users can enable the "[9p](https://www.kernel.org/doc/Documentation/filesystems/9p.txt)" mount type from the `Volumes` tab. This will expose the filesystem by using QEMU's `virtio-9p-pci` devices.
+
+* Cache Mode:
+Specifies a caching policy that has a default setting as `mmap`. The caching options are `[none, loose, fscache, mmap]`.
+
+* Memory Size In KiB:
+Users can specify the number of bytes to use for the "9p" packet size. The minimum value is 4 KiB and the default size is 128 KiB.
+
+* Protocol Version:
+Users can select the "9p" protocol version. The options include `[9p2000, 9p2000.u, 9p2000.L]` and the default protocol setting is `9p200.L`.
+
+* Security Model:
+Users can select a supported security model with options being `[passthrough, mapped-xattr, mapped-file, none]`. The default security setting value is `none`.
+
+### virtiofs
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+Users can enable the [`virtiofs`](https://virtio-fs.gitlab.io/) mount type from the `Volumes` tab. This is implemented using the Apple `Virtualization.Framework` shared directory device.
diff --git a/versioned_docs/version-1.14/ui/preferences/wsl/integrations.md b/versioned_docs/version-1.14/ui/preferences/wsl/integrations.md
new file mode 100644
index 0000000000..87114b0cae
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/wsl/integrations.md
@@ -0,0 +1,33 @@
+---
+sidebar_label: Integrations
+title: Integrations
+---
+
+
+
+
+
+The Integrations tab allows for the option to make the Rancher Desktop Kubernetes configuration accessible to any Linux distributions configured for WSL. Once enabled, you can communicate with the Rancher Desktop Kubernetes cluster using tools like `kubectl` from within the WSL distribution.
+
+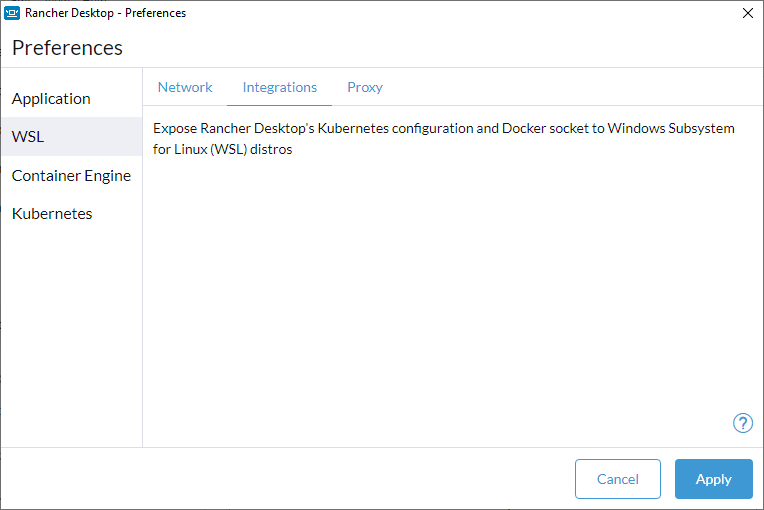
+
+With WSL, memory and CPU allocation is configured globally across all Linux distributions. Refer to the [WSL documentation] for instructions.
+
+[WSL documentation]:
+https://docs.microsoft.com/en-us/windows/wsl/wsl-config#options-for-wslconfig
+
+### `~/.kube/config`
+
+Rancher Desktop will create a symlink from `~/.kube/config` inside the distro to the corresponding `%USERPROFILE%\.kube\config` file on the Windows filesystem.
+
+If the `~/.kube/config` file already exists inside the distro and contains only `rancher-desktop` contexts, users, and clusters then it will be deleted and replaced with the symlink.
+
+If it contains any other information then the file will not be modified and the user has to update the Rancher Desktop cluster information manually. In that case the "Kubernetes context" menu entry for the notification icon will show (and change) the context for the Win32 side only. The contexts inside distributions will need to be managed manually from a command prompt.
+
+:::caution info
+
+In Rancher Desktop `1.11.1` and `1.12.*` the `~/.kube/config` file was converted from a symlink into a regular file because the network tunnelling option required a different Kubernetes endpoint inside WSL clusters than on the host.
+
+Rancher Desktop `1.13.0` added a network proxy between the cluster and the other distros, so the endpoint is the same again as on the host. If the `~/.kube/config` file only references the `rancher-desktop` cluster then it will automatically be converted into a symlink again. Otherwise the user need to consolidate the different files manually.
+
+:::
diff --git a/versioned_docs/version-1.14/ui/preferences/wsl/network.md b/versioned_docs/version-1.14/ui/preferences/wsl/network.md
new file mode 100644
index 0000000000..eb25c3a0bc
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/wsl/network.md
@@ -0,0 +1,14 @@
+---
+sidebar_label: Network
+title: Network (Windows)
+---
+
+
+
+
+
+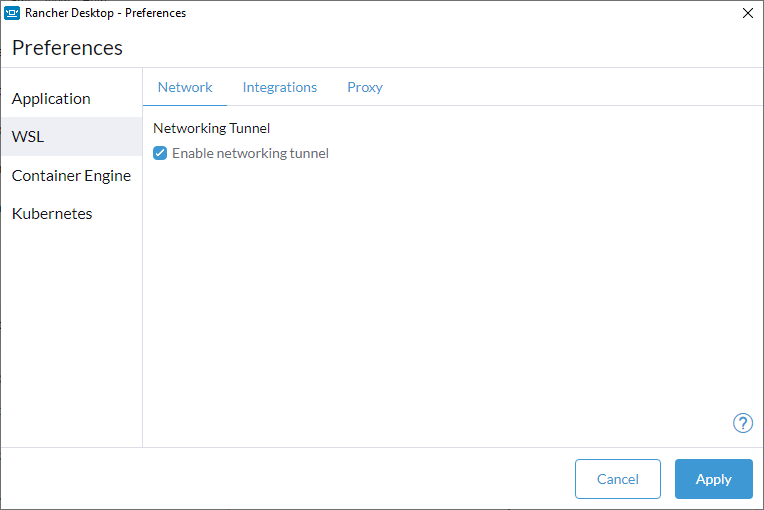
+
+### Networking Tunnel
+
+Users can enable or disable the networking tunnel from the `Network` view. After changes are applied, Kubernetes will be restarted. Please see [developer notes](https://github.com/rancher-sandbox/rancher-desktop-networking) for more information on the experimental Rancher Desktop Network.
diff --git a/versioned_docs/version-1.14/ui/preferences/wsl/proxy.md b/versioned_docs/version-1.14/ui/preferences/wsl/proxy.md
new file mode 100644
index 0000000000..3698326a34
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/preferences/wsl/proxy.md
@@ -0,0 +1,32 @@
+---
+sidebar_label: Proxy
+title: Proxy
+---
+
+
+
+
+
+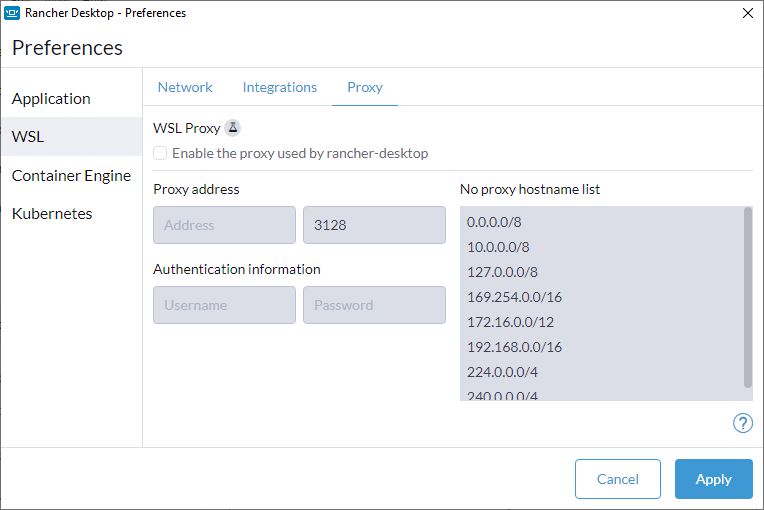
+
+### WSL Proxy
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+Rancher Desktop now allows local, corporate, or VPN proxy server support for Windows users. The implementation can be enabled or disabled through the `Proxy` tab to capture network traffic and forward it to an http proxy. Once all information has been input, click the `Apply` button to have changes immediately take effect.
+
+### Proxy address
+
+Users can input their proxy IP address and port number in the `Proxy address` fields.
+
+### Authentication information
+
+If your proxy requires authentication then users can input their username and password in the `Authentication information` fields.
+
+### No proxy hostname list
+
+Default hostnames that should not be proxied will be displayed in this text area.
diff --git a/versioned_docs/version-1.14/ui/snapshots.md b/versioned_docs/version-1.14/ui/snapshots.md
new file mode 100644
index 0000000000..67b33cf606
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/snapshots.md
@@ -0,0 +1,63 @@
+---
+sidebar_label: Snapshots
+title: Snapshots
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+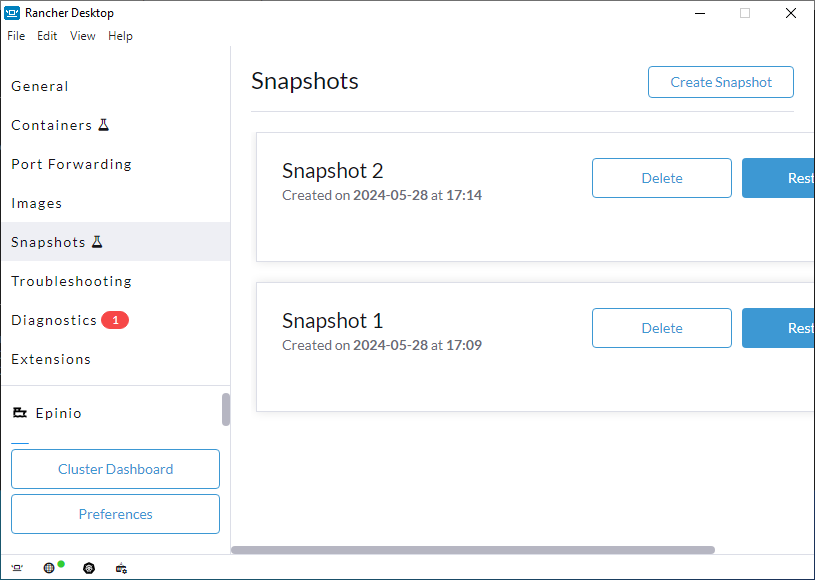
+
+
+
+
+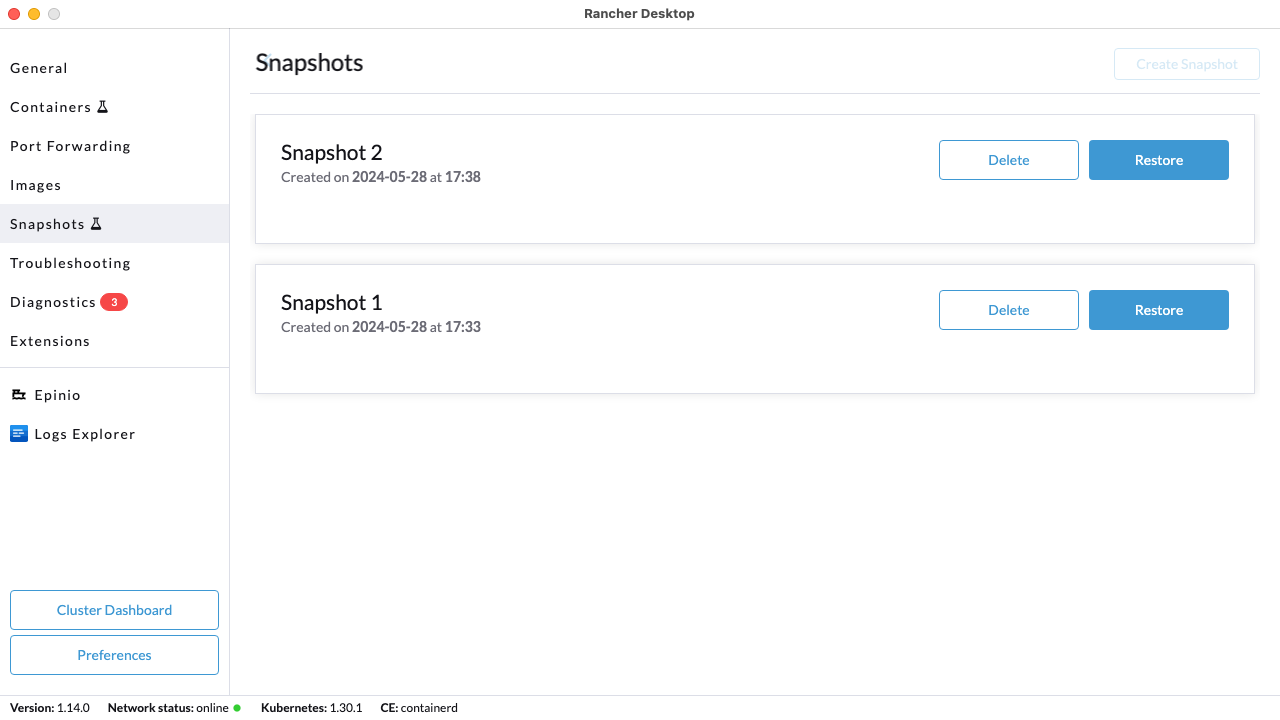
+
+
+
+
+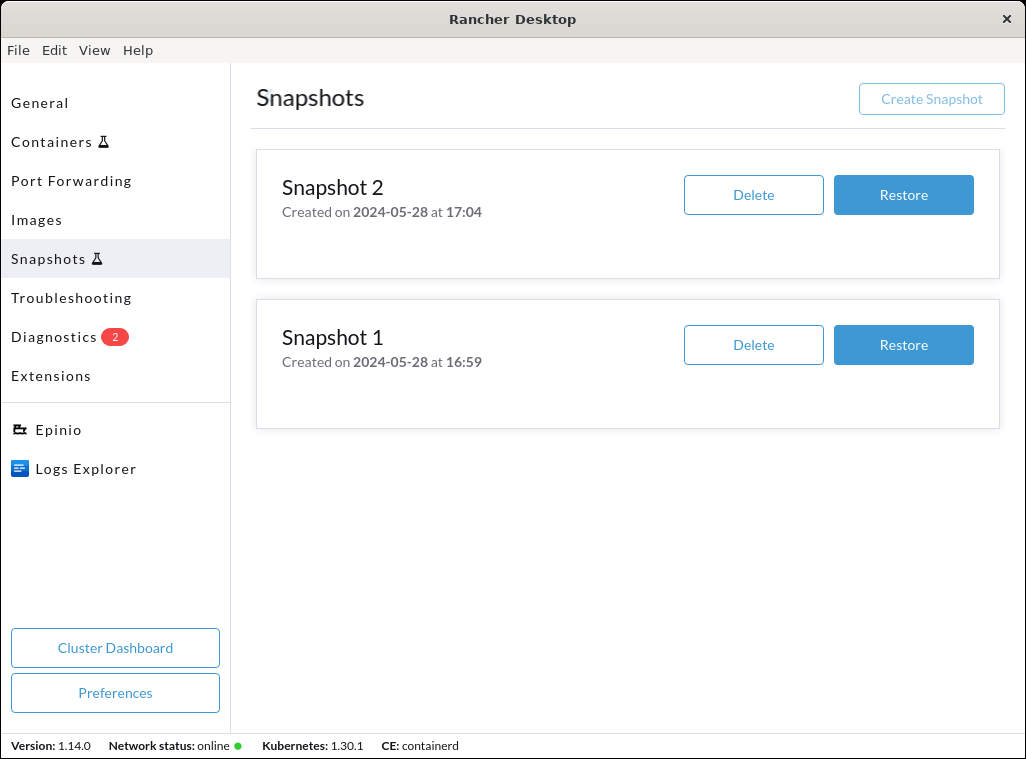
+
+
+
+
+:::caution warning
+
+This is an **experimental** feature.
+
+:::
+
+A snapshot can be used to store the current configuration of your virtual machine and all associated settings. Snapshots are stored in a `snapshots` directory which are created at the below paths respective to your operating system:
+
+- macOS: `~/Library/Application Support/rancher-desktop/snapshots`
+- Linux: `~/.local/share/rancher-desktop/snapshots`
+- Windows: `%LOCALAPPDATA%\rancher-desktop\snapshots`
+
+The `snapshots` directory may be moved by creating a symlink from your system's default path to your preferred location.
+
+### Snapshot Management
+
+The following actions can be taken on the tab:
+
+- `Create Snapshot`:
+ You can choose to create a snapshot through the user interface from the Snapshots tab by clicking the `Create Snapshot` button. This will launch a dialog and provides a note alerting that Rancher Desktop will be unavailable during the creation of a new Snapshot.
+ - `Snapshot Name`:
+ Text can be entered into this field to name your snapshot.
+ - `Description`:
+ Text can be entered into the Description field that describes your snapshot.
+
+- `Restore`:
+ The `Restore` button can be used to restore a snapshot and will replace your current snapshot installation including preference settings. Rancher Desktop will be unavailable while this process is running.
+
+- `Delete`:
+ The `Delete` button can be used to remove snapshots permanently.
+
+### Command Line - `rdctl snapshot`
+
+All commands available through the user interface are also available using the `rdctl snapshot` command. Please see the [reference page](../references/rdctl-command-reference.md) for more information.
diff --git a/versioned_docs/version-1.14/ui/troubleshooting.md b/versioned_docs/version-1.14/ui/troubleshooting.md
new file mode 100644
index 0000000000..59686f38bd
--- /dev/null
+++ b/versioned_docs/version-1.14/ui/troubleshooting.md
@@ -0,0 +1,58 @@
+---
+sidebar_label: Troubleshooting
+title: Troubleshooting
+---
+
+
+
+
+
+import TabsConstants from '@site/core/TabsConstants';
+
+
+
+
+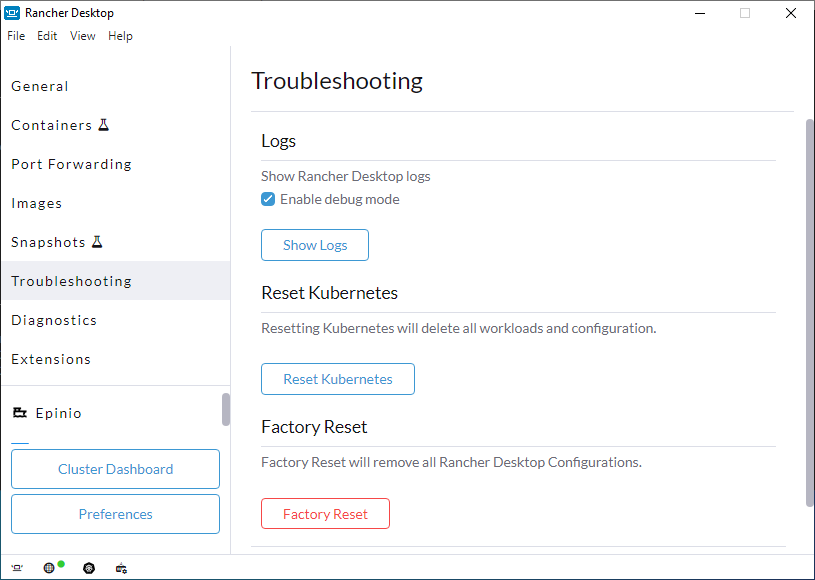
+
+
+
+
+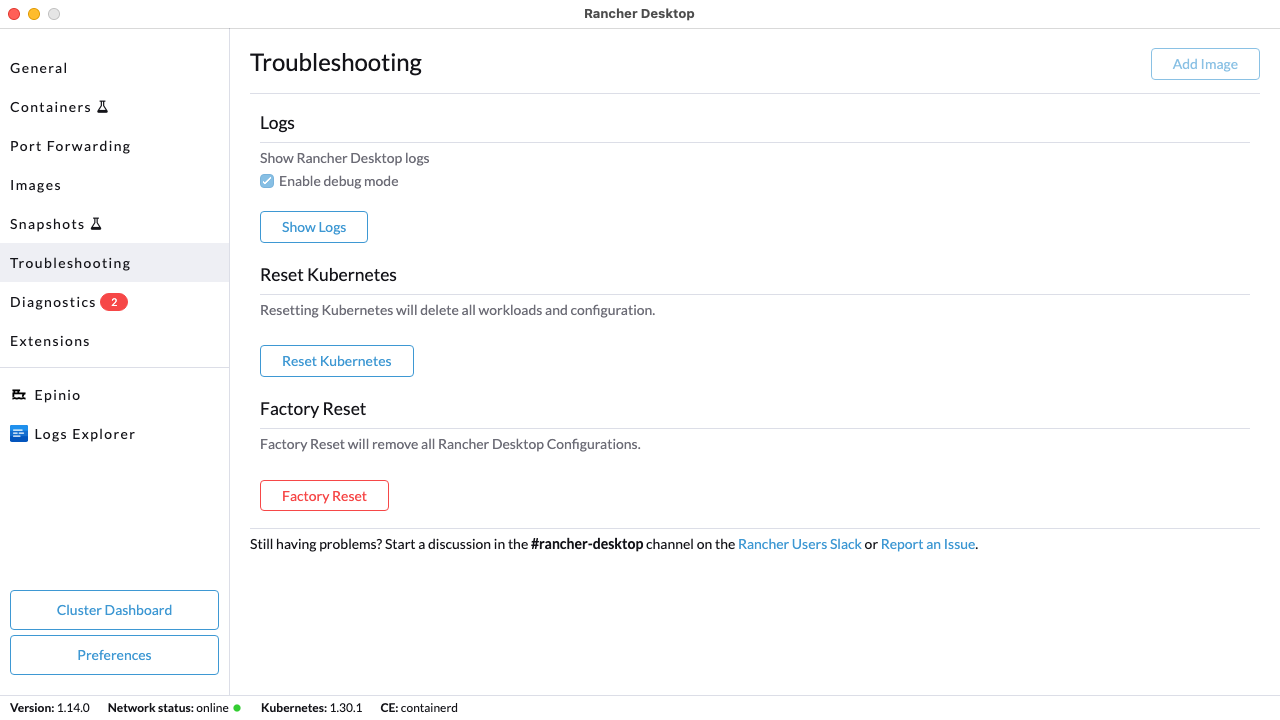
+
+
+
+
+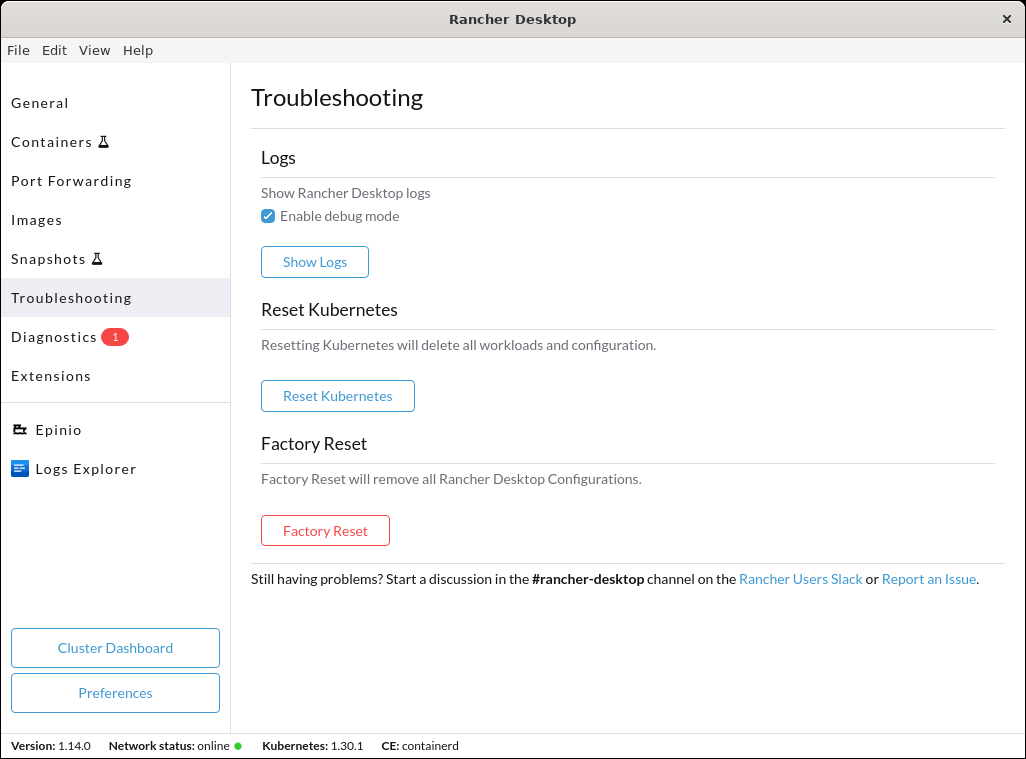
+
+
+
+
+### Show Logs
+
+Use this option to open the folder containing all Rancher Desktop log files.
+
+#### Enable Debug Mode
+
+Enable debug level logging.
+
+### Reset Kubernetes
+
+Reset Kubernetes and remove all workloads and configurations. Before the reset occurs, users are presented with a confirmation and the option to also delete container images.
+
+To reset Kubernetes:
+
+1. Click **Reset Kubernetes**. A confirmation window appears.
+1. Optional: select whether to also delete container images.
+1. Click **Reset** to proceed. Kubernetes stops and starts again.
+
+### Factory Reset
+
+Remove the cluster and all other Rancher Desktop settings. To continue The initial setup procedure must be done again.
+
+To perform a factory reset:
+
+1. Click **Reset**. A confirmation window appears.
+1. Optional: select whether cached Kubernetes images are kept.
+1. Click **Factory Reset** to proceed. Kubernetes stops and Rancher Desktop closes.
+1. Optional: start Rancher Desktop again.
+
diff --git a/versioned_docs/version-latest/bundled-utilities-version-info/v1.13.0.md b/versioned_docs/version-latest/bundled-utilities-version-info/v1.13.0.md
index f9574b9722..43969ecec8 100644
--- a/versioned_docs/version-latest/bundled-utilities-version-info/v1.13.0.md
+++ b/versioned_docs/version-latest/bundled-utilities-version-info/v1.13.0.md
@@ -6,4 +6,5 @@ docker-credential-helpers: 0.8.1
helm: 3.14.2
kuberlr: 0.4.5
nerdctl: 1.7.3
+spin-shim: 0.11.1
trivy: 0.49.1
diff --git a/versioned_docs/version-latest/bundled-utilities-version-info/v1.14.0.md b/versioned_docs/version-latest/bundled-utilities-version-info/v1.14.0.md
new file mode 100644
index 0000000000..0658b36f0a
--- /dev/null
+++ b/versioned_docs/version-latest/bundled-utilities-version-info/v1.14.0.md
@@ -0,0 +1,12 @@
+amazon-ecr-credential-helper: 0.8.0
+docker: 26.1.0
+docker-buildx: 0.14.1
+docker-compose: 2.27.1
+docker-credential-helpers: 0.8.2
+helm: 3.15.1
+kuberlr: 0.4.5
+nerdctl: 1.7.6
+spin: 2.5.1
+spin-shim: 0.14.1
+spinkube: 0.2.0
+trivy: 0.51.4
diff --git a/versioned_docs/version-latest/getting-started/deployment.md b/versioned_docs/version-latest/getting-started/deployment.md
index 011d5cd0b5..4bc8accdb0 100644
--- a/versioned_docs/version-latest/getting-started/deployment.md
+++ b/versioned_docs/version-latest/getting-started/deployment.md
@@ -63,23 +63,23 @@ For versions `1.9` and later of Rancher Desktop, all preferences values can be l
-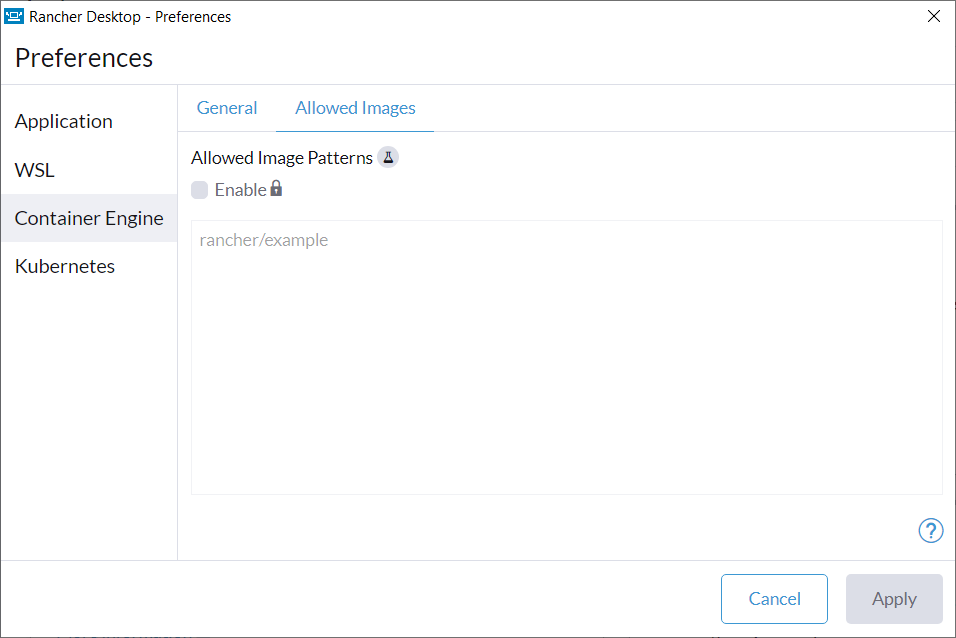
+
-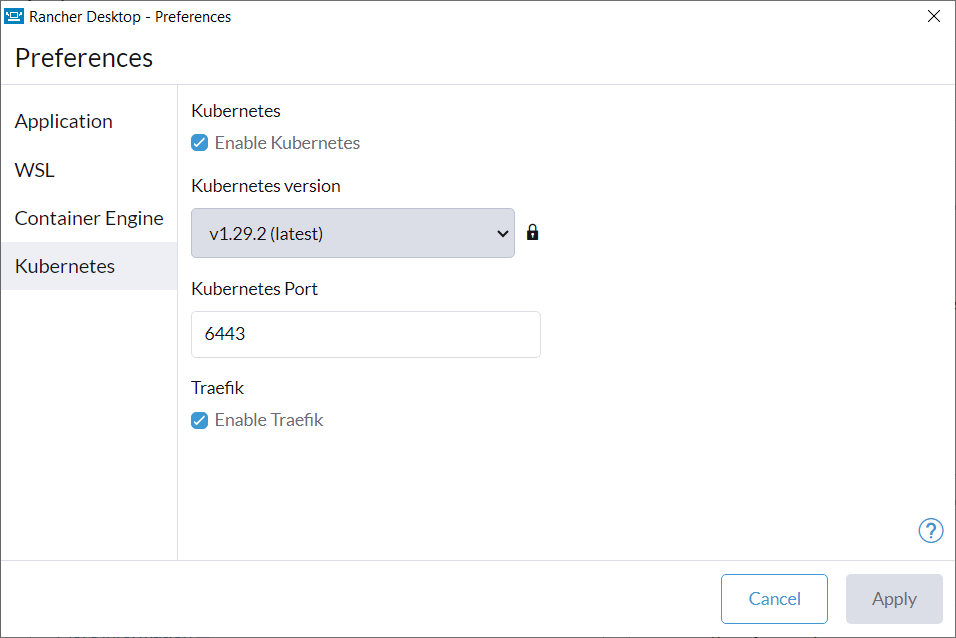
+
-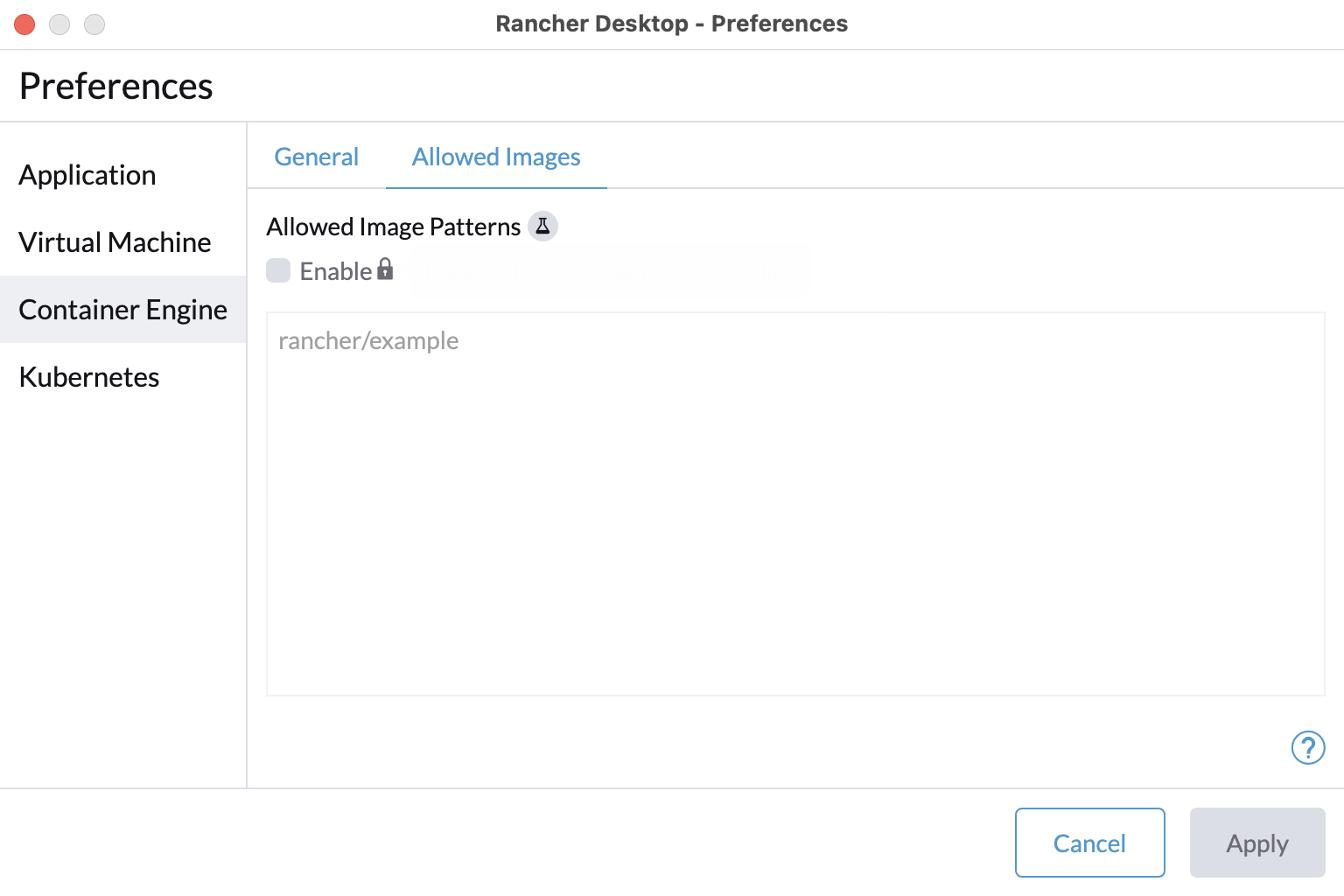
+
-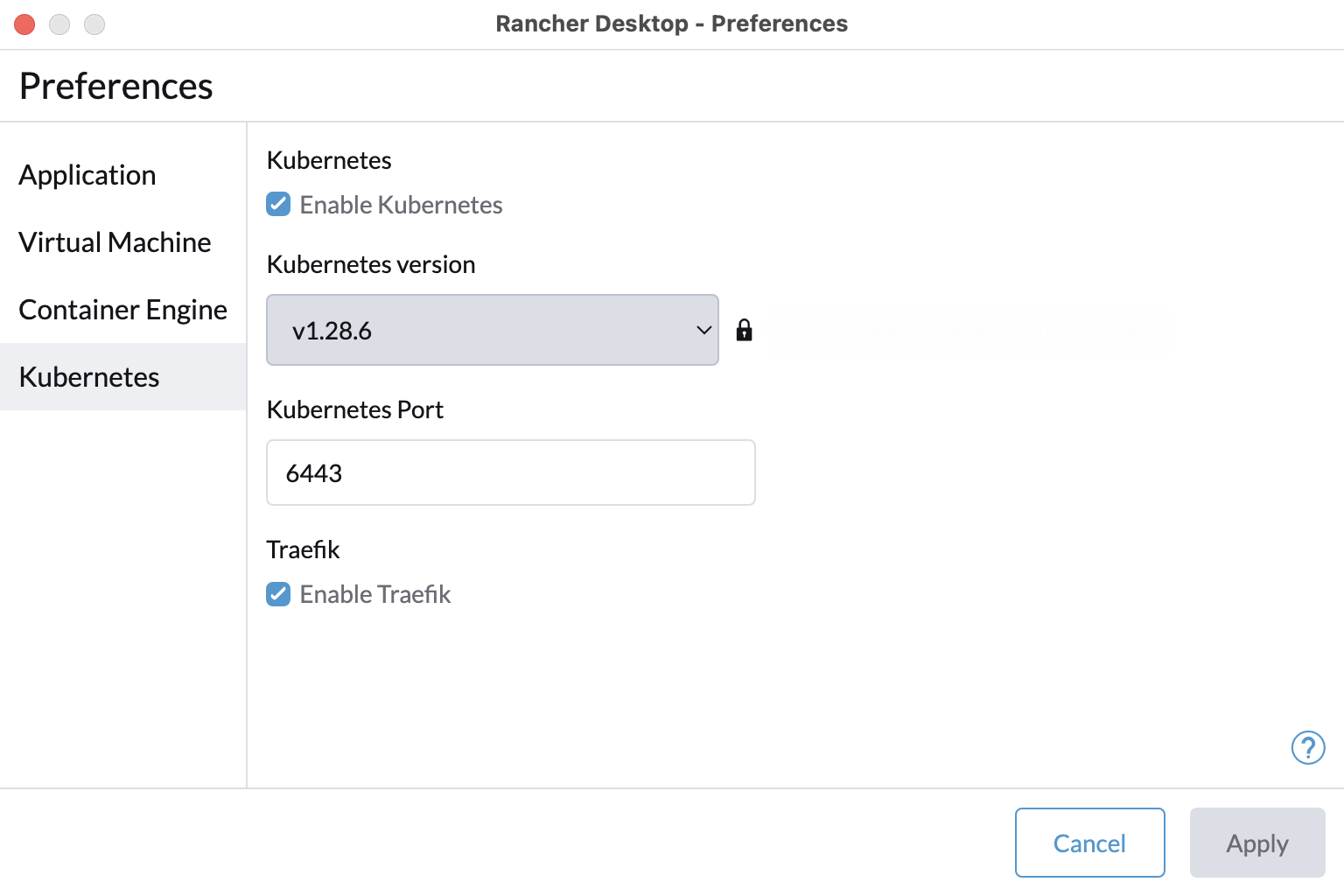
+
-
+
-
+
diff --git a/versioned_docs/version-latest/getting-started/introduction.md b/versioned_docs/version-latest/getting-started/introduction.md
index 451d91c74e..2c6f0899df 100644
--- a/versioned_docs/version-latest/getting-started/introduction.md
+++ b/versioned_docs/version-latest/getting-started/introduction.md
@@ -11,7 +11,7 @@ import TabsConstants from '@site/core/TabsConstants';
Rancher Desktop is an app that provides container management and Kubernetes on the desktop. It is available for Mac (both on Intel and Apple Silicon), Windows, and Linux.
-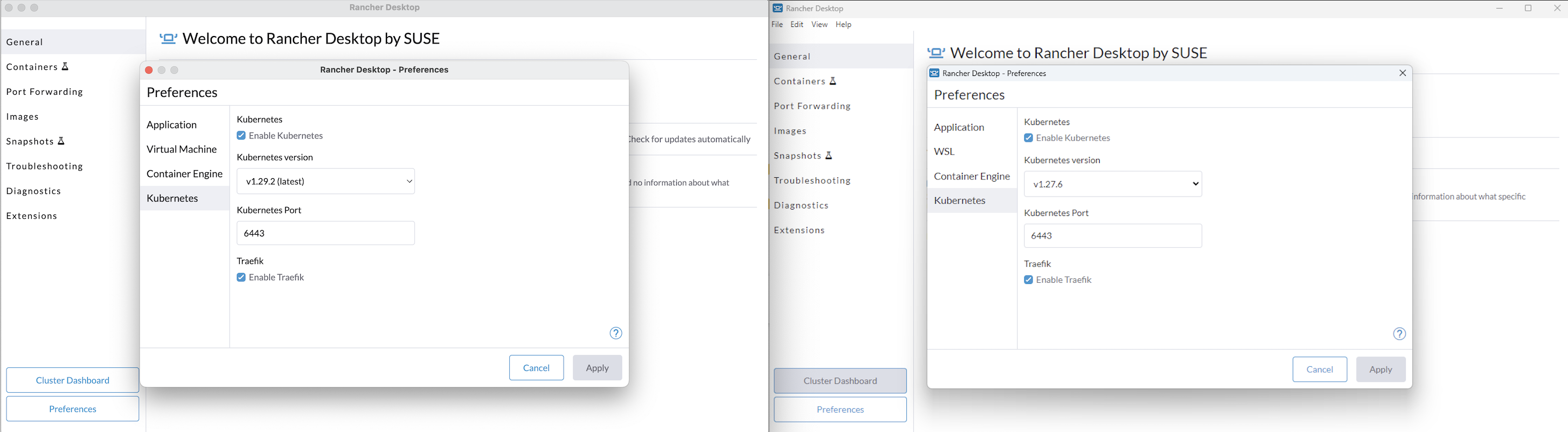
+
_The above image shows Kubernetes settings on Mac on the left and Windows on the right._
diff --git a/versioned_docs/version-latest/how-to-guides/installing-uninstalling-extensions.md b/versioned_docs/version-latest/how-to-guides/installing-uninstalling-extensions.md
index 27d0d00b0f..985bbeee28 100644
--- a/versioned_docs/version-latest/how-to-guides/installing-uninstalling-extensions.md
+++ b/versioned_docs/version-latest/how-to-guides/installing-uninstalling-extensions.md
@@ -25,7 +25,7 @@ There are two ways in which you can install extensions, a method using the UI an
Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
-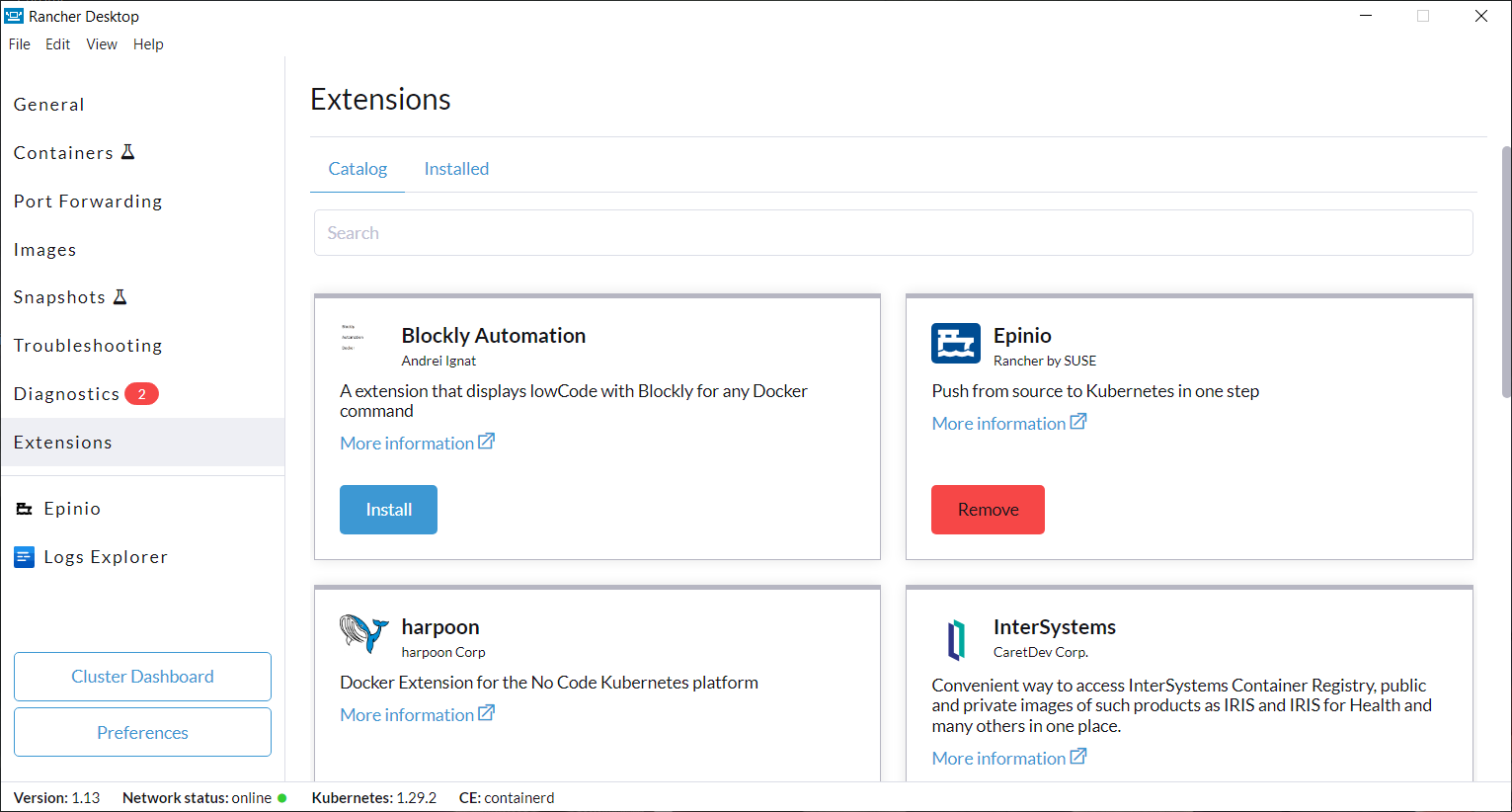
+
#### Using the Command Line
@@ -48,7 +48,7 @@ rdctl extension install :
Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
-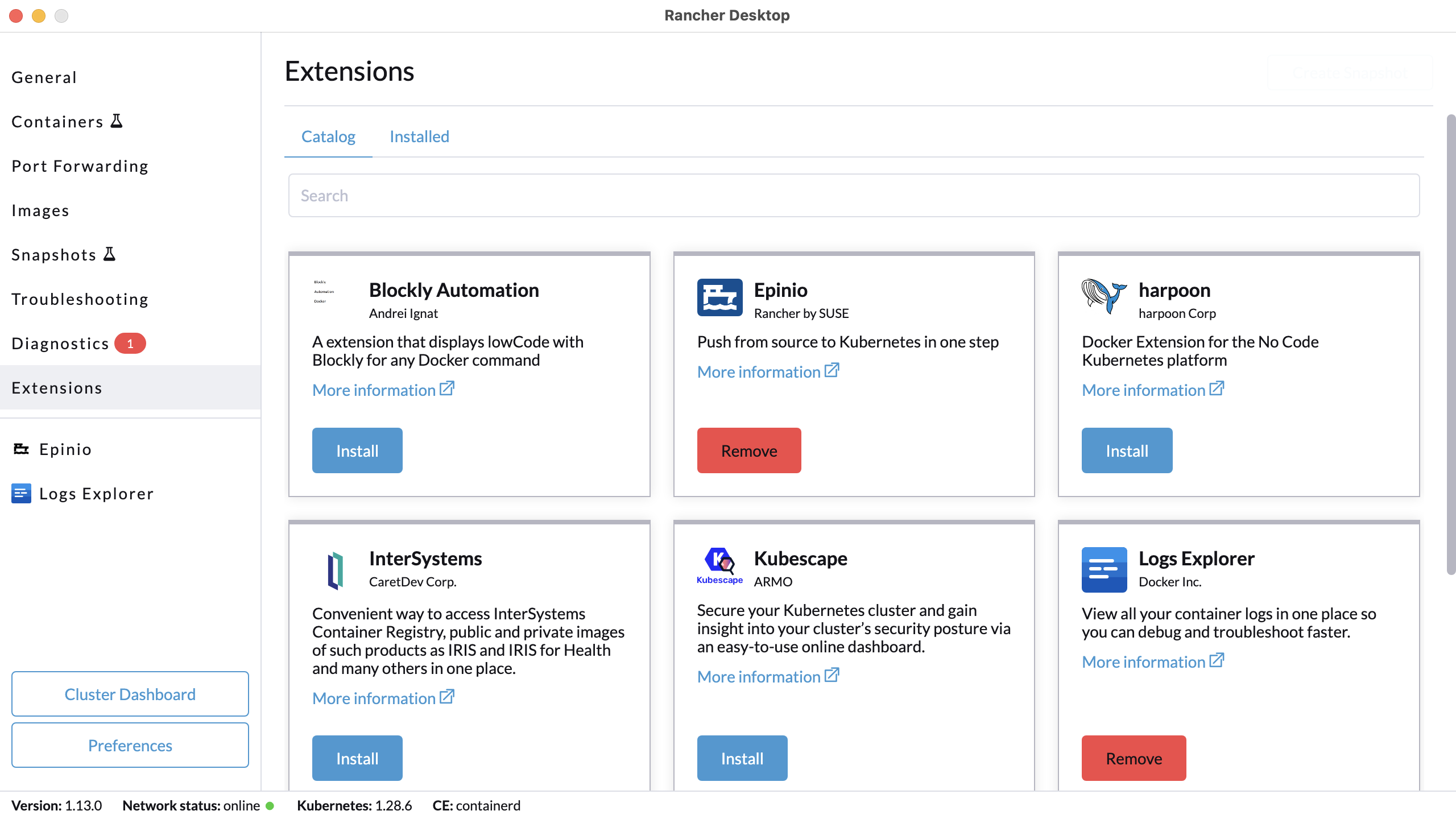
+
#### Using the Command Line
@@ -71,7 +71,7 @@ rdctl extension install :
Click **Extensions** from the main UI to navigate to the **Catalog** tab. Here you can search through extensions available for use which can be downloaded and installed using the **Install** button.
-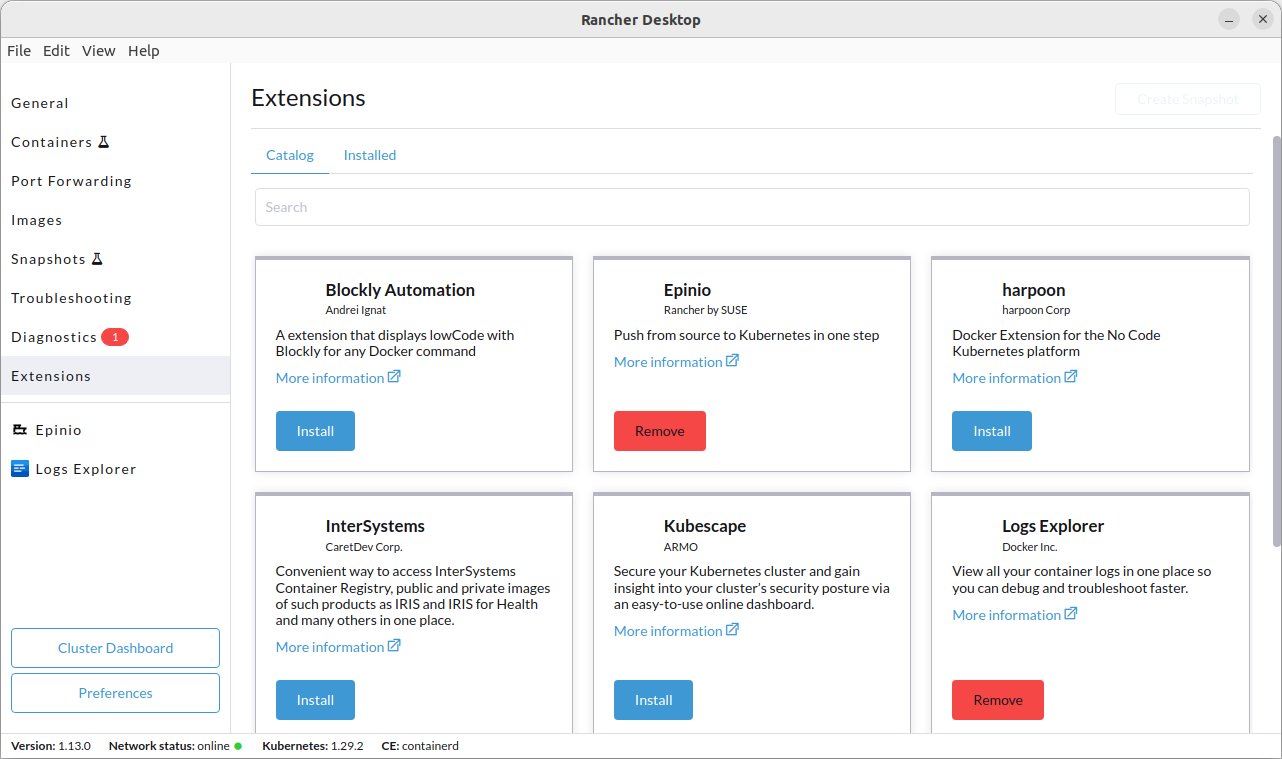
+
#### Using the Command Line
@@ -104,12 +104,12 @@ Click **Extensions** from the main UI to navigate to the **Catalog** tab. On thi
-
+
-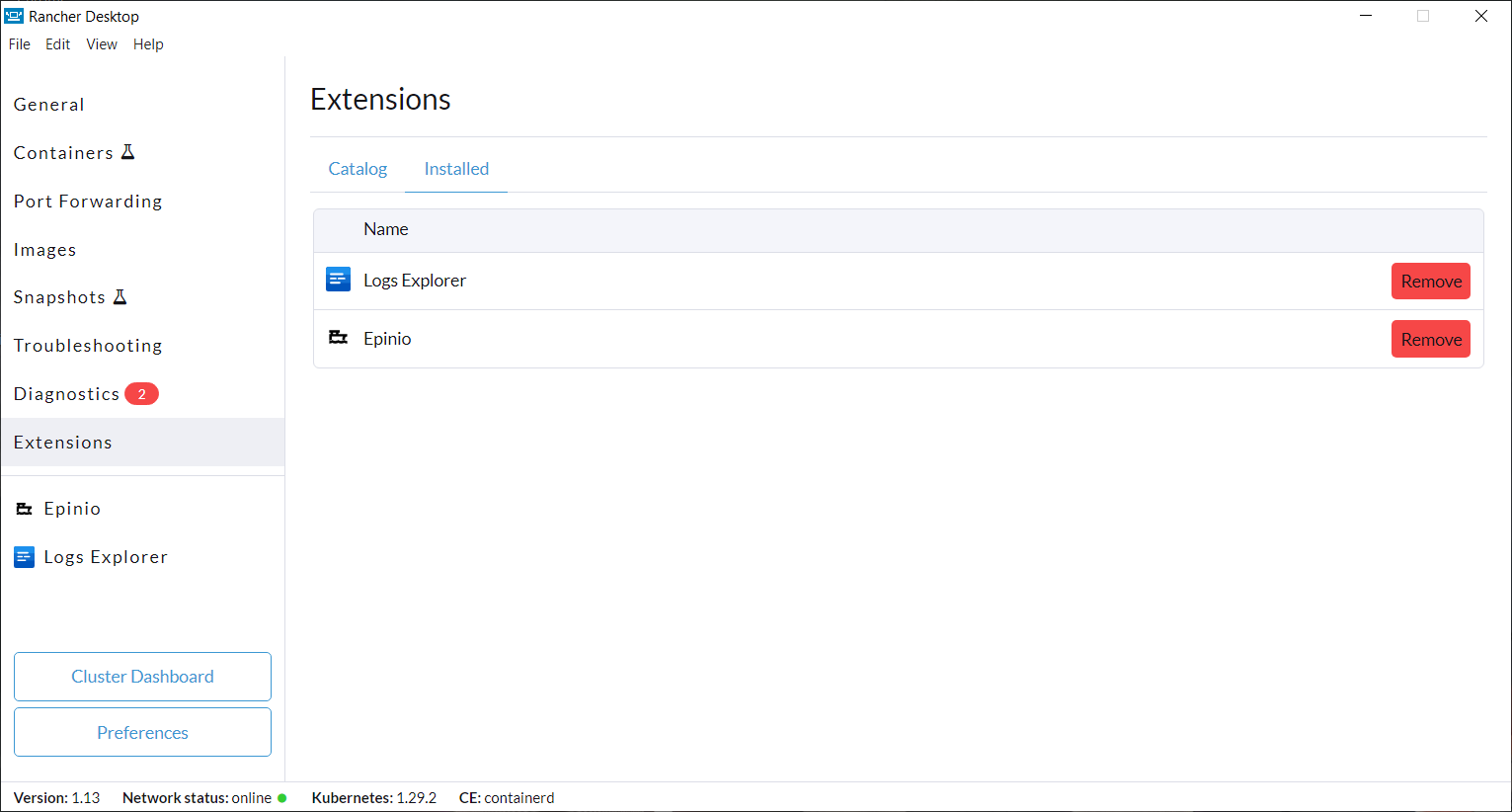
+
@@ -138,12 +138,12 @@ Click **Extensions** from the main UI to navigate to the **Catalog** tab. On thi
-
+
-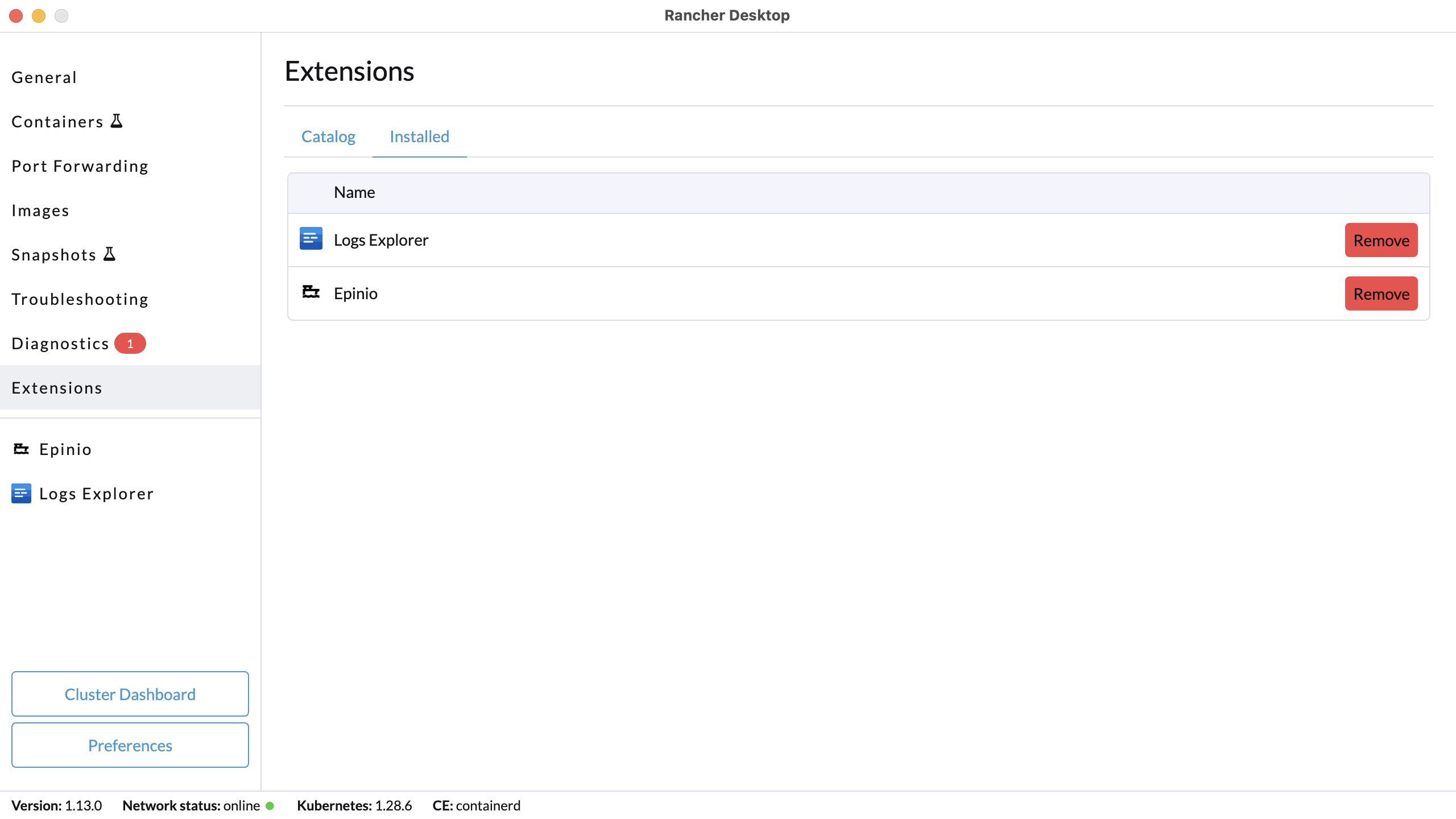
+
@@ -172,12 +172,12 @@ Click **Extensions** from the main UI to navigate to the **Catalog** tab. On thi
-
+
-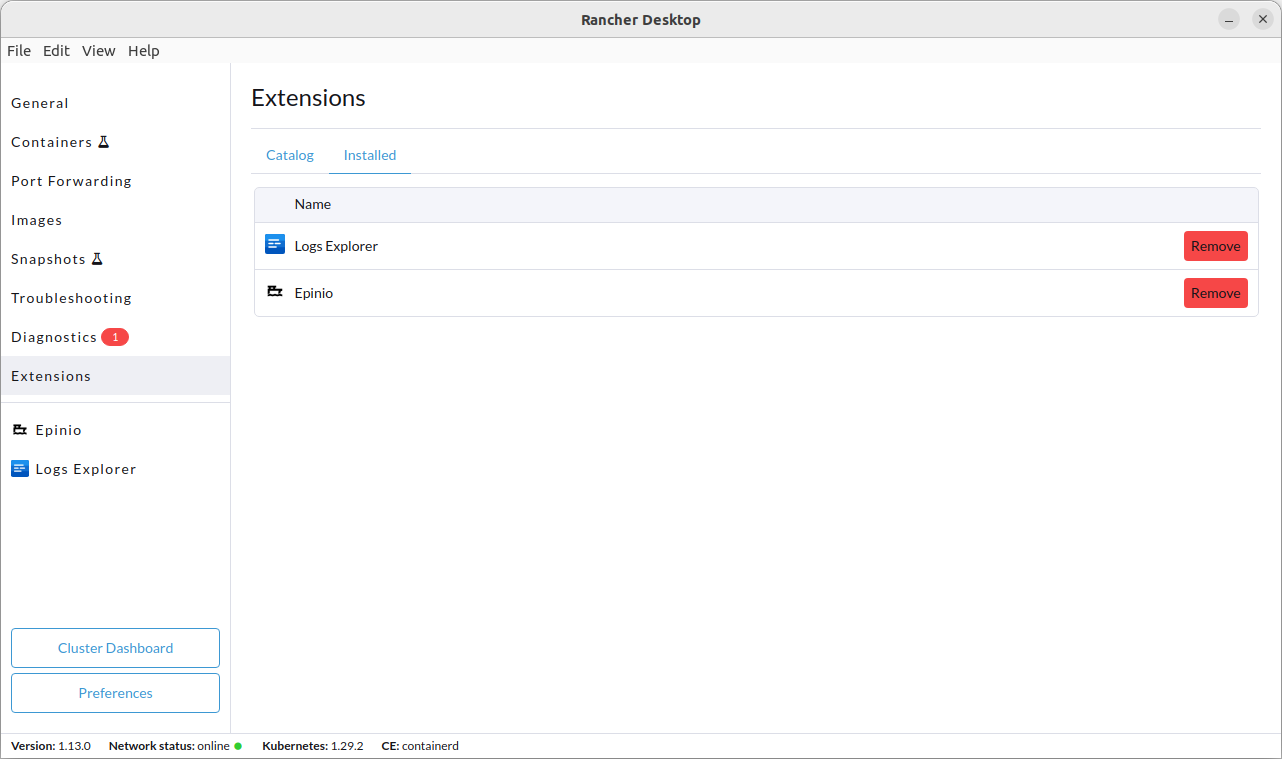
+
diff --git a/versioned_docs/version-latest/how-to-guides/mirror-private-registry.md b/versioned_docs/version-latest/how-to-guides/mirror-private-registry.md
index b4424949bc..5eb9b460da 100644
--- a/versioned_docs/version-latest/how-to-guides/mirror-private-registry.md
+++ b/versioned_docs/version-latest/how-to-guides/mirror-private-registry.md
@@ -13,7 +13,7 @@ Rancher Desktop can be configured to mirror private registries using either cont
-Below is an example [provisioning script](/how-to-guides/provisioning-scripts#macos--linux) that can be used to mirror private registries.
+Below is an example [provisioning script](../how-to-guides/provisioning-scripts.md#macOS--Linux) that can be used to mirror private registries.
Check if you have the `override.yaml` file in the path below, otherwise you can create the file in the path with the suggested provisioning commands.
@@ -45,7 +45,7 @@ rdctl shell -- cat /etc/rancher/k3s/registries.yaml
-Below is an example [provisioning script](/how-to-guides/provisioning-scripts#macos--linux) that can be used to mirror private registries.
+Below is an example [provisioning script](../how-to-guides/provisioning-scripts.md#macOS--Linux) that can be used to mirror private registries.
Check if you have the `override.yaml` file in the path below, otherwise you can create the file in the path with the suggested provisioning commands.
@@ -78,7 +78,7 @@ rdctl shell -- cat /etc/rancher/k3s/registries.yaml
-Ensure that you have initialized the application with a first run in order to create the `\provisioning\` directory. Once created, [provisioning scripts](/how-to-guides/provisioning-scripts#windows) can be utilized to mirror private registries using a `.start` file.
+Ensure that you have initialized the application with a first run in order to create the `\provisioning\` directory. Once created, [provisioning scripts](../how-to-guides/provisioning-scripts.md#Windows) can be utilized to mirror private registries using a `.start` file.
The file path and example provisioning script are provided below. After you have created the file with the appropriate configuration, restart the Rancher Desktop application for the provisioning script to take effect.
diff --git a/versioned_docs/version-latest/how-to-guides/traefik-ingress-example.md b/versioned_docs/version-latest/how-to-guides/traefik-ingress-example.md
index a737cc53a2..8a2e6f0ba9 100644
--- a/versioned_docs/version-latest/how-to-guides/traefik-ingress-example.md
+++ b/versioned_docs/version-latest/how-to-guides/traefik-ingress-example.md
@@ -30,7 +30,7 @@ Rancher Desktop uses `K3s` under the hood, which in turn uses [Traefik](https://
1. Create a `whoami` example with basic deployment, service, and Ingress objects defined:
:::note
- Some Linux distributions don't allow listening to privileged ports by default, please see the documentation on [Traefik port binding access](/getting-started/installation#traefik-port-binding-access) to authorize ports if necessary.
+ Some Linux distributions don't allow listening to privileged ports by default, please see the documentation on [Traefik port binding access](../getting-started/installation.md#traefik-port-binding-access) to authorize ports if necessary.
:::
```bash
diff --git a/versioned_docs/version-latest/references/bundled-utilities.md b/versioned_docs/version-latest/references/bundled-utilities.md
index ea05d11ea0..18da7fbf30 100644
--- a/versioned_docs/version-latest/references/bundled-utilities.md
+++ b/versioned_docs/version-latest/references/bundled-utilities.md
@@ -11,6 +11,7 @@ import Version110 from '../bundled-utilities-version-info/v1.10.0.md';
import Version111 from '../bundled-utilities-version-info/v1.11.0.md';
import Version112 from '../bundled-utilities-version-info/v1.12.0.md';
import Version113 from '../bundled-utilities-version-info/v1.13.0.md';
+import Version114 from '../bundled-utilities-version-info/v1.14.0.md';
@@ -20,6 +21,7 @@ Rancher Desktop uses several utilities/subsystems as dependencies under the hood
| Rancher Desktop Version | Dependency Versions |
| ------------- | ---------------- |
+| v1.14.0 | |
| v1.13.0 | |
| v1.12.0 | |
| v1.11.0 | |
diff --git a/versioned_docs/version-latest/tutorials/working-with-webassembly.md b/versioned_docs/version-latest/tutorials/working-with-webassembly.md
index 9391633e5a..b533066a45 100644
--- a/versioned_docs/version-latest/tutorials/working-with-webassembly.md
+++ b/versioned_docs/version-latest/tutorials/working-with-webassembly.md
@@ -26,24 +26,24 @@ For now additional shims can be installed by the user into the `containerd-shims
Any shim installed there will automatically be copied into the VM and configured for the container engine when Rancher Desktop is started (installing a newer version of the `spin` shim will override the bundled version).
-## Developing Wasm applications with Rancher Desktop
+## Developing Wasm Applications with Rancher Desktop
Developing Wasm applications on your local machine on top of Rancher Desktop typically involves below steps:
- Create an application in your programming language of choice. You can compile code written in many languages, such as C, C++, Rust, Go, and others, into Wasm modules
- Compile the code into a Wasm module
-- Package the Wasm module as a OCI contianer image and push to a container registry
+- Package the Wasm module as a OCI container image and push to a container registry
- Run the Wasm container and/or
- Deploy the Wasm container into Kubernetes
-### Creating a simple app and compiling it into a Wasm module
+### Creating a Simple App and Compiling It Into a Wasm Module
You can use the Spin framework from Fermyon to quickly bootstrap a simple Wasm app. Install Spin on your machine following the instructions on the [Installing Spin](https://developer.fermyon.com/spin/v2/install) page.
Once you have successfully installed Spin, create a new app via the command `spin new`.
-Select the lanaguage you would like to use for development.
-```
+Select the language you would like to use for development.
+```console
$spin new
Pick a template to start your application with:
http-js (HTTP request handler using Javascript)
@@ -51,14 +51,14 @@ Pick a template to start your application with:
```
Give a name to your app
-```
+```console
$spin new
Pick a template to start your application with: http-ts (HTTP request handler using Typescript)
Enter a name for your new application: rd-spin-hello-world
```
Provide an optional description and leave the API route path to default
-```
+```console
$spin new
Pick a template to start your application with: http-ts (HTTP request handler using Typescript)
Enter a name for your new application: rd-spin-hello-world
@@ -70,7 +70,7 @@ Once the command ran successfully, you should see a directory created with the b
Update the `index.ts` file to return a different message than the default.
-```
+```console
import { HandleRequest, HttpRequest, HttpResponse } from "@fermyon/spin-sdk"
export const handleRequest: HandleRequest = async function (request: HttpRequest): Promise {
@@ -82,9 +82,9 @@ export const handleRequest: HandleRequest = async function (request: HttpRequest
}
```
-Change to the app diretory and run the `spin build` command to compile the app code into a Wasm module.
+Change to the app directory and run the `spin build` command to compile the app code into a Wasm module.
-```
+```console
$spin build
Building component rd-spin-hello-world with `npm run build`
@@ -103,11 +103,11 @@ Finished building all Spin components
Once the build command ran successfully, you should see the `rd-spin-hello-world.wasm` module created inside the `target` directory.
-### Package the Wasm module as a OCI contianer image and push to a container registry
+### Package the Wasm Module as an OCI Container Image and Push to a Container Registry
Create a `Dockerfile` with below code to package the `Wasm` module as a docker image.
-```
+```console
FROM scratch
COPY spin.toml /spin.toml
COPY /target/rd-spin-hello-world.wasm /target/rd-spin-hello-world.wasm
@@ -118,7 +118,7 @@ Run the command below to package the Wasm module as a container image.
-```
+```console
nerdctl build \
--namespace k8s.io \
--platform wasi/wasm \
@@ -128,7 +128,7 @@ nerdctl build \
-```
+```console
docker buildx build \
--load \
--platform wasi/wasm \
@@ -144,28 +144,28 @@ Push the image to the container registry
-```
+```console
nerdctl push ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0
```
-```
+```console
docker push ghcr.io/rancher-sandbox/rd-spin-hello-world:0.1.0
```
-### Running the Wasm container
+### Running the Wasm Container
Running a Wasm container directly is currently only supported with the `moby` container engine; there is a bug in `nerdctl` that prevents it from working with `containerd`. Ensure you have selected `dockerd(moby)` as the container engine under [Preferences > Container Engine > General](../ui/preferences/container-engine/general.md) to work through the steps in this section.
The following command runs the `rd-spin-hello-world` sample `spin` application, built in the previous section, on the `moby` engine (note the final `/` on the last line; it is the command to run, and `docker run` will fail if it is omitted):
-```
+```console
docker run \
--detach \
--name spin-demo \
@@ -178,12 +178,12 @@ docker run \
The internal port `80` has been mapped to `8080` and can be tested from the host:
-```
+```console
$ curl http://localhost:8080/
Hello from Wasm container!
```
-### Running Wasm apps with Kubernetes
+### Running Wasm Apps with Kubernetes
Running WebAssembly applications on Kubernetes is currently only supported with the `containerd` runtime; it doesn't work with the `cri-dockerd` shim used to run Kubernetes on top of `moby`.
diff --git a/versioned_docs/version-latest/ui/containers.md b/versioned_docs/version-latest/ui/containers.md
index 9f4325e57f..78979e2e77 100644
--- a/versioned_docs/version-latest/ui/containers.md
+++ b/versioned_docs/version-latest/ui/containers.md
@@ -13,17 +13,17 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-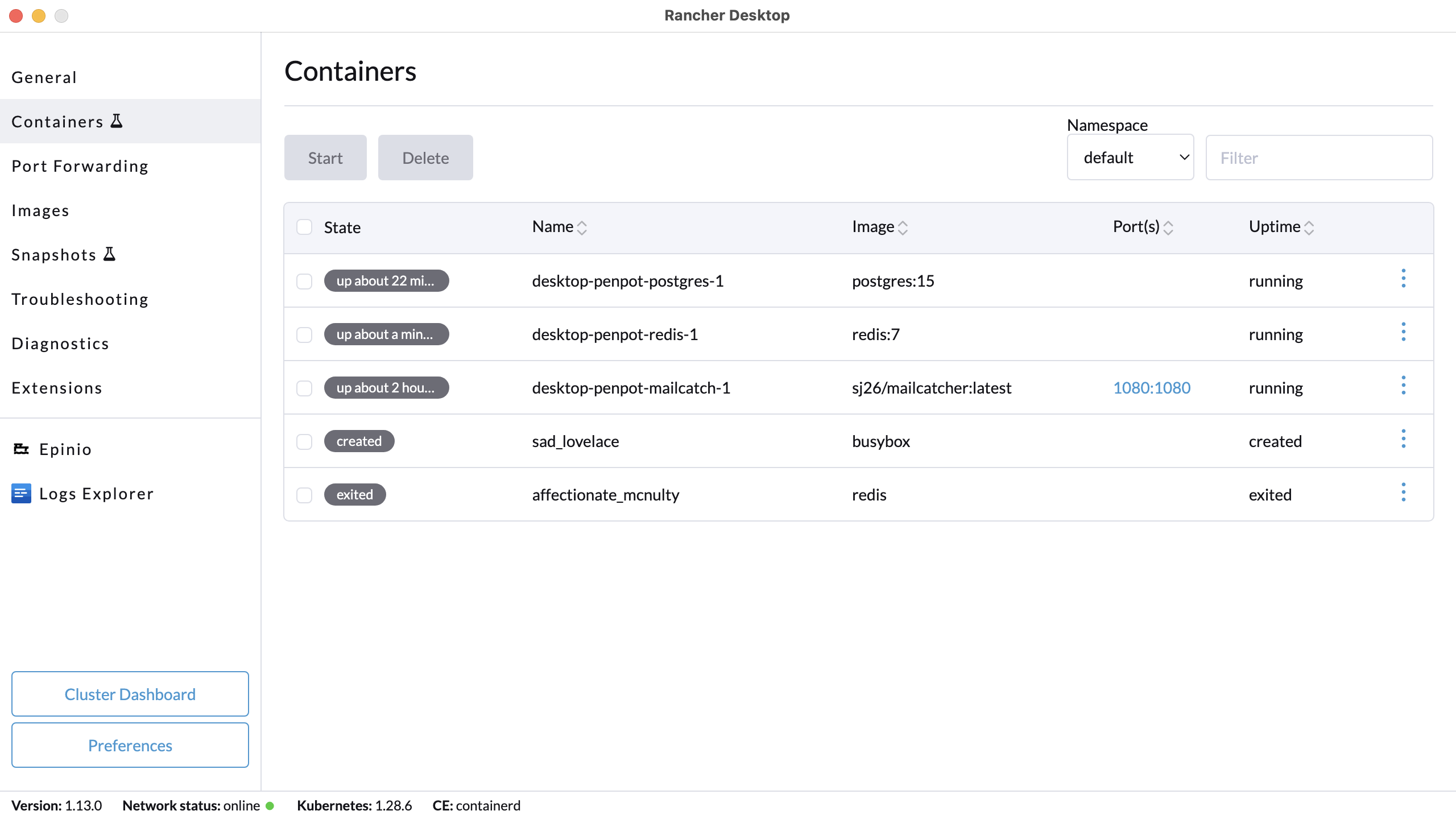
+
-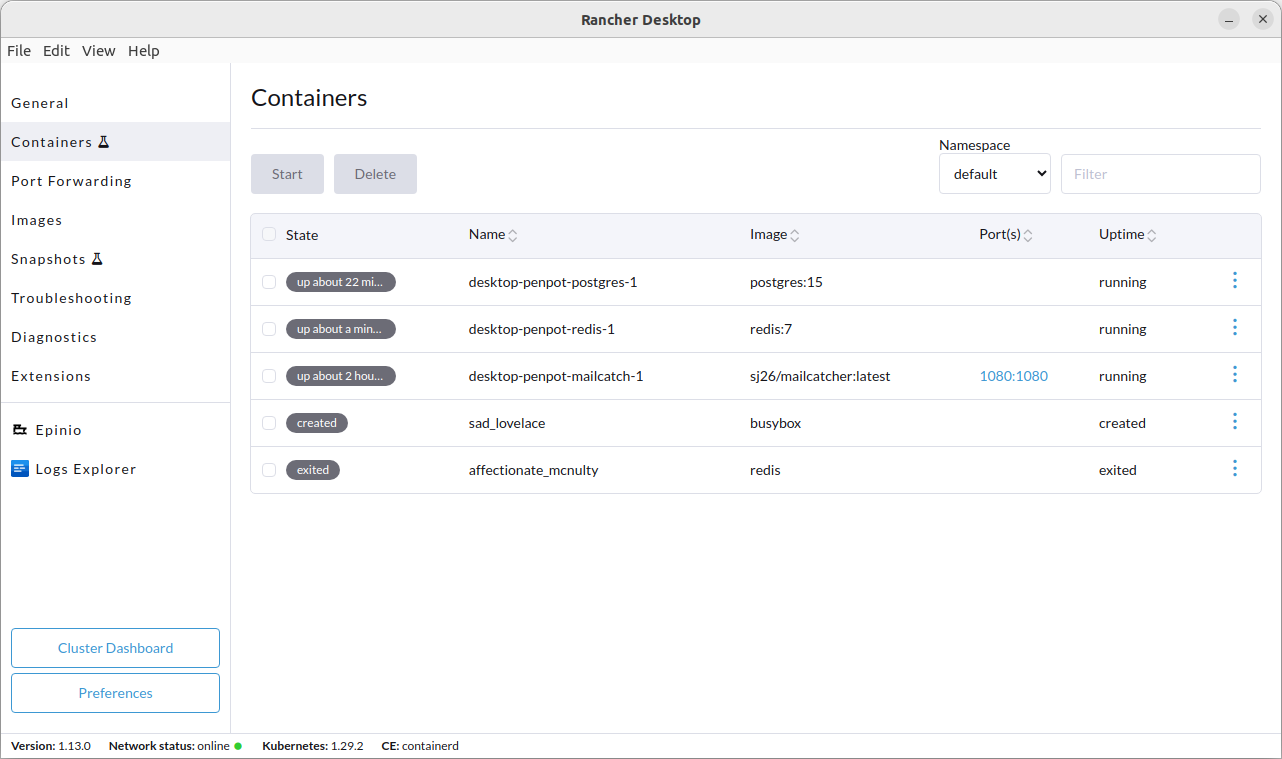
+
diff --git a/versioned_docs/version-latest/ui/diagnostics.md b/versioned_docs/version-latest/ui/diagnostics.md
index a577803b94..962c6ebef1 100644
--- a/versioned_docs/version-latest/ui/diagnostics.md
+++ b/versioned_docs/version-latest/ui/diagnostics.md
@@ -16,17 +16,17 @@ The **Diagnostics** feature runs several checks in the background to detect comm
-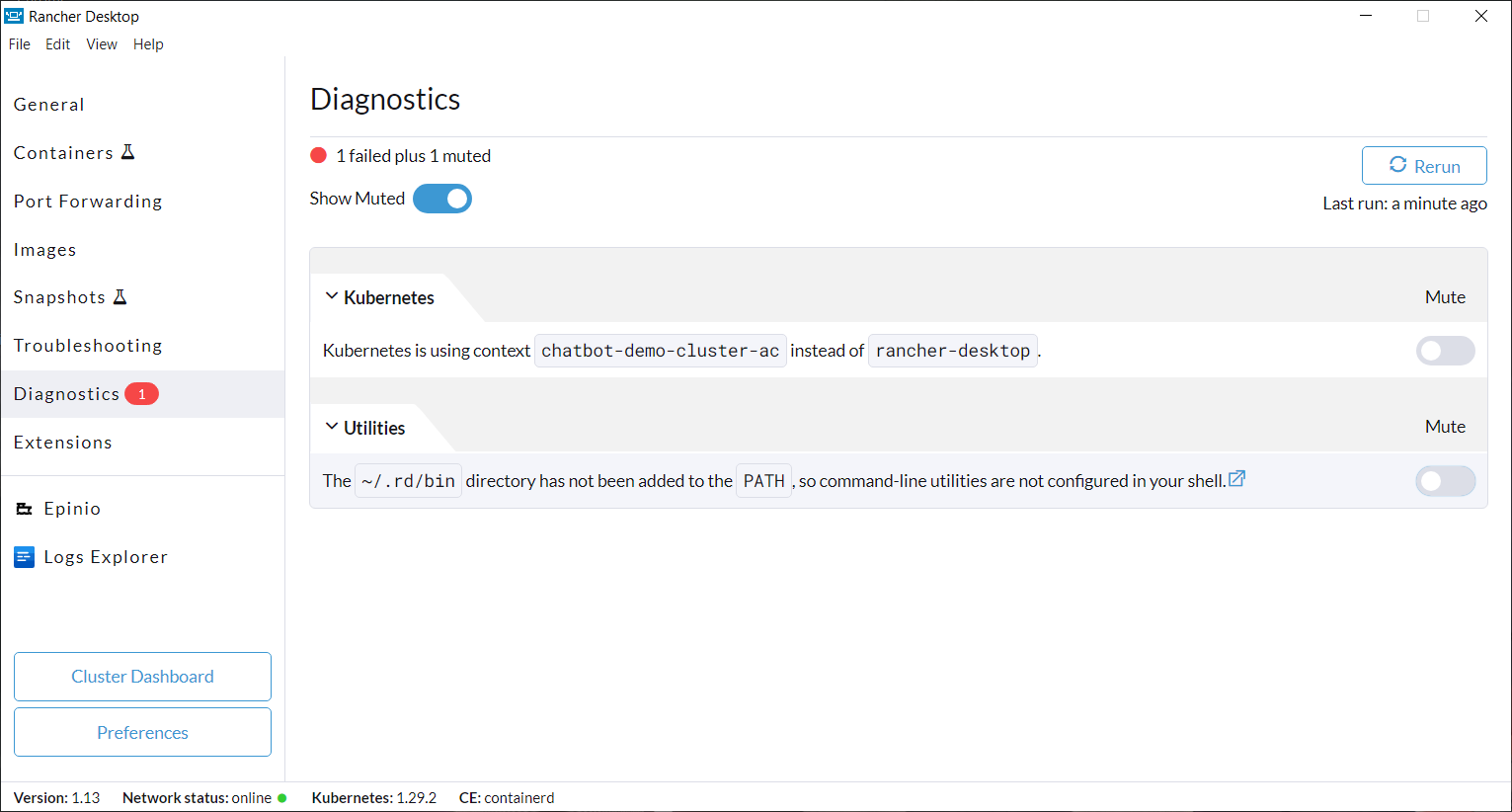
+
-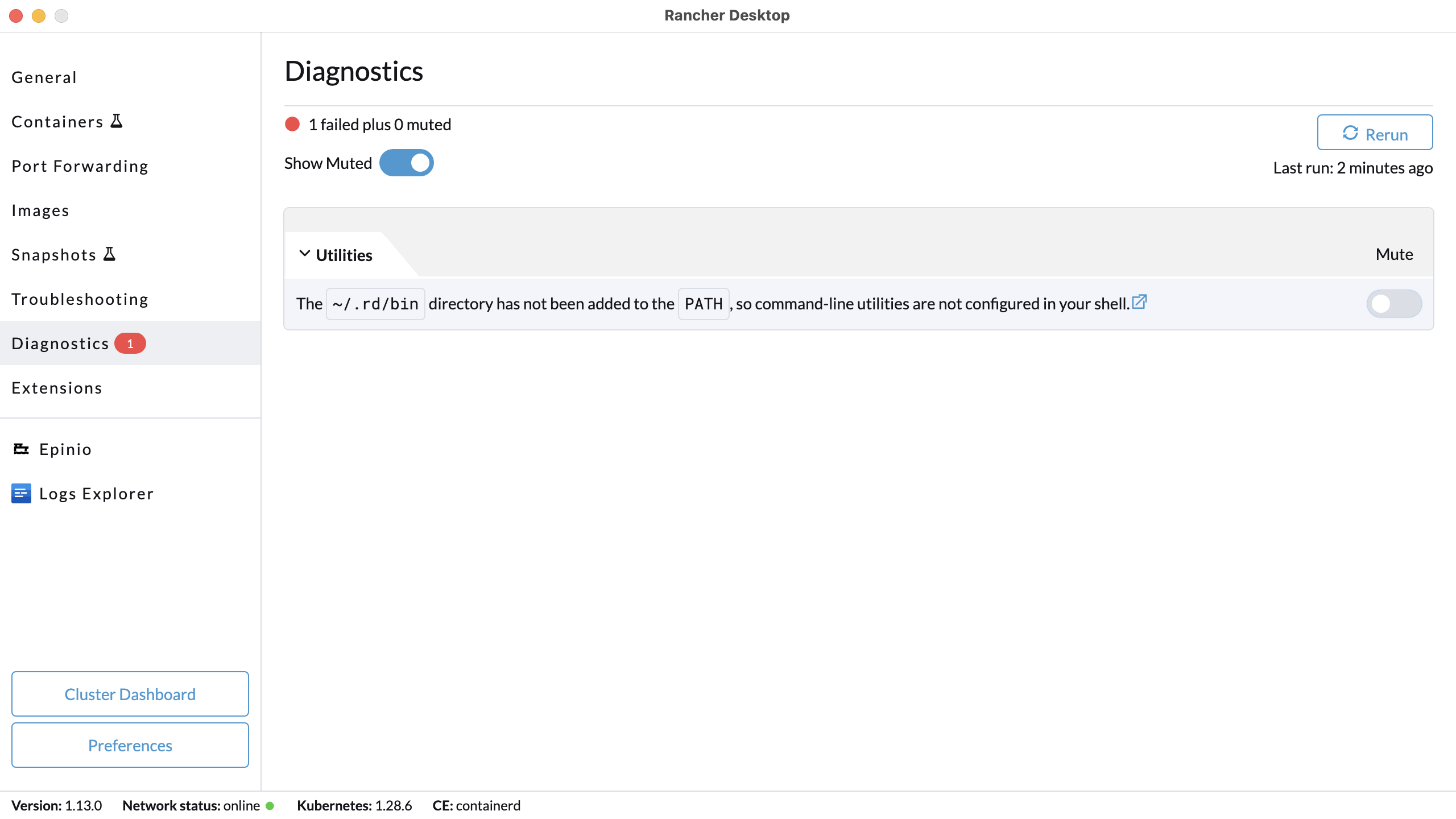
+
-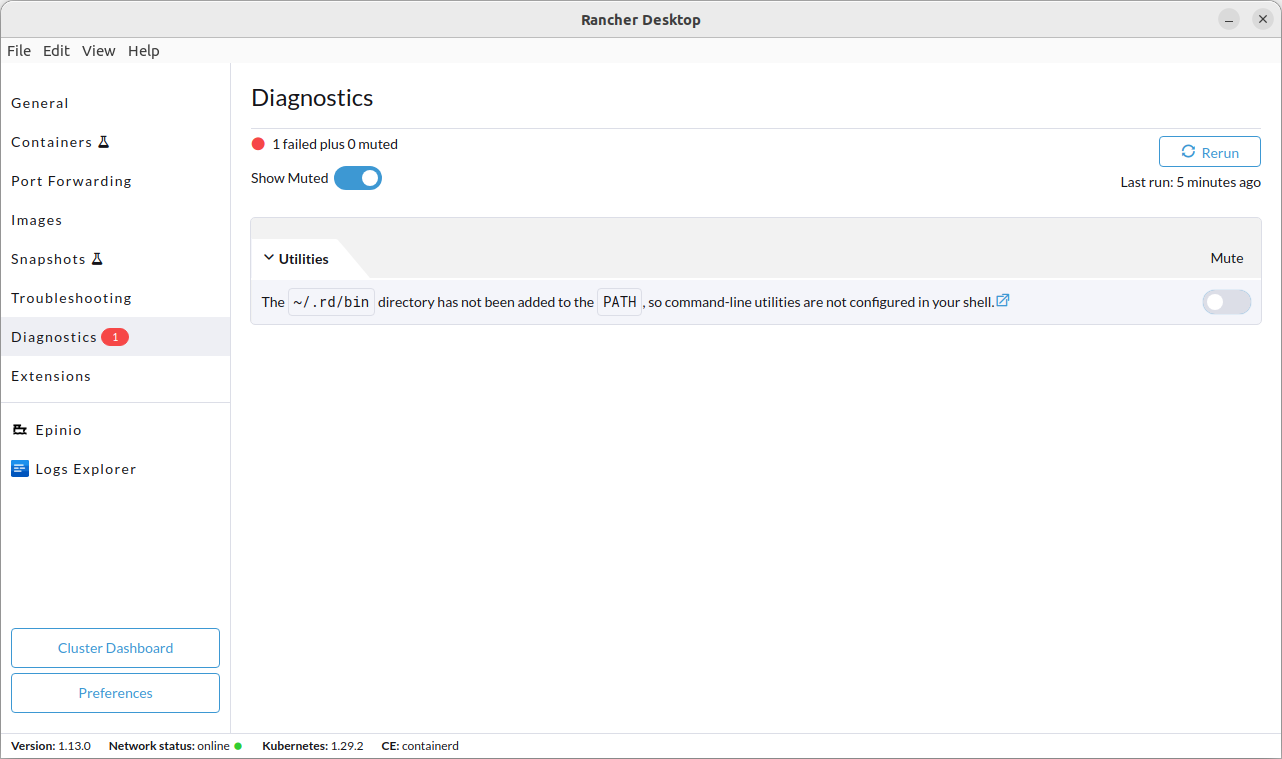
+
diff --git a/versioned_docs/version-latest/ui/extensions.md b/versioned_docs/version-latest/ui/extensions.md
index 21f797d741..f33cd23f0f 100644
--- a/versioned_docs/version-latest/ui/extensions.md
+++ b/versioned_docs/version-latest/ui/extensions.md
@@ -16,17 +16,17 @@ The **Catalog** tab acts as a marketplace for available Rancher Desktop Extensio
-
+
-
+
-
+
@@ -42,17 +42,17 @@ The **Installed** tab is a view for all installed extensions on your Rancher Des
-
+
-
+
-
+
diff --git a/versioned_docs/version-latest/ui/general.md b/versioned_docs/version-latest/ui/general.md
index 0f8c873c38..ba75bba503 100644
--- a/versioned_docs/version-latest/ui/general.md
+++ b/versioned_docs/version-latest/ui/general.md
@@ -14,17 +14,17 @@ The **General** tab provides information on communication channels where users c
-
+
-
+
-
+
diff --git a/versioned_docs/version-latest/ui/images.md b/versioned_docs/version-latest/ui/images.md
index 3b7bc6586c..92463a0dcf 100644
--- a/versioned_docs/version-latest/ui/images.md
+++ b/versioned_docs/version-latest/ui/images.md
@@ -12,17 +12,17 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-
+
-
+
diff --git a/versioned_docs/version-latest/ui/port-forwarding.md b/versioned_docs/version-latest/ui/port-forwarding.md
index 5048f6519c..1a8a515f3c 100644
--- a/versioned_docs/version-latest/ui/port-forwarding.md
+++ b/versioned_docs/version-latest/ui/port-forwarding.md
@@ -12,17 +12,17 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-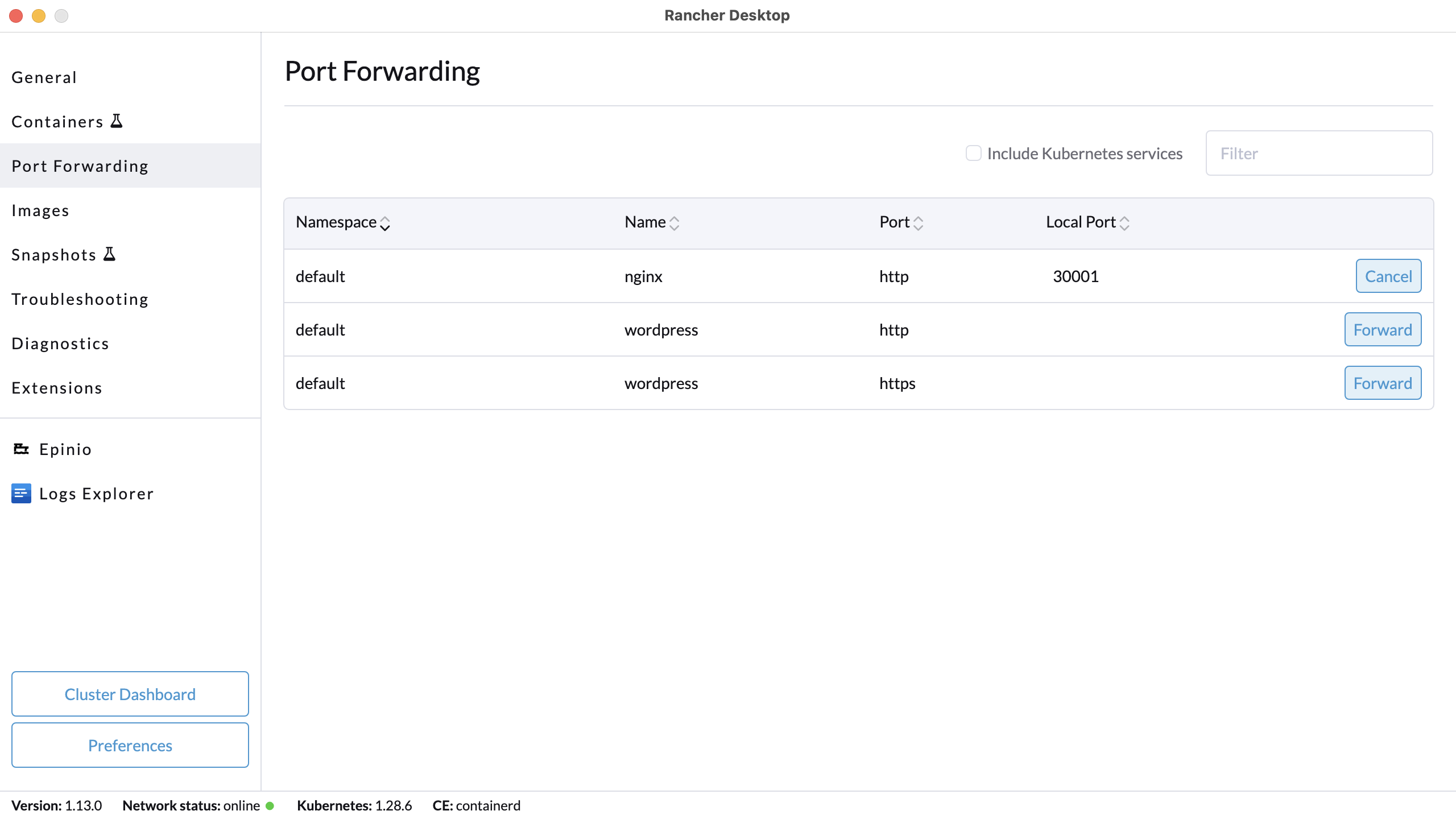
+
-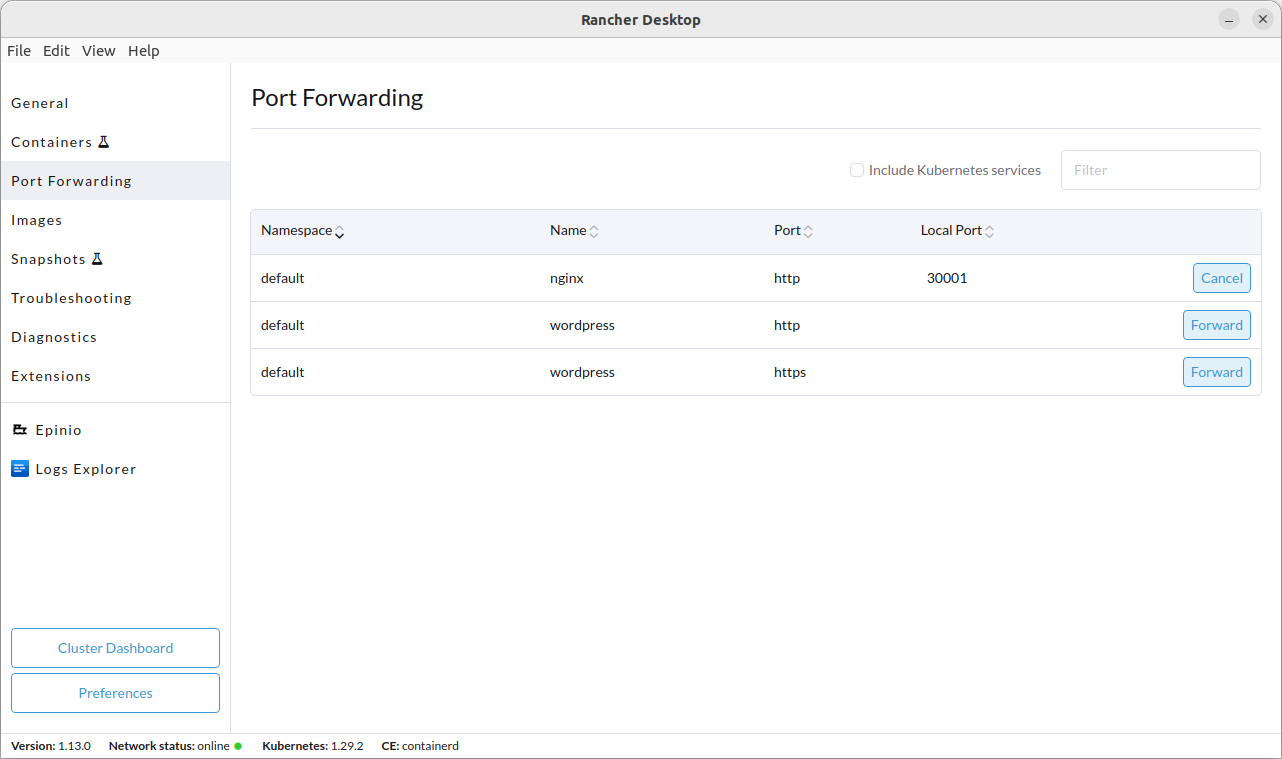
+
@@ -42,6 +42,6 @@ Rancher Desktop includes automated port forwarding for versions `1.9` and later.
:::note
-Please see [Traefik Port Binding Access](/getting-started/installation#traefik-port-binding-access) to configure ports at the operating system level.
+Please see [Traefik Port Binding Access](../getting-started/installation.md#traefik-port-binding-access) to configure ports at the operating system level.
:::
diff --git a/versioned_docs/version-latest/ui/preferences/application/behavior.md b/versioned_docs/version-latest/ui/preferences/application/behavior.md
index e6790f89d8..bae2c87703 100644
--- a/versioned_docs/version-latest/ui/preferences/application/behavior.md
+++ b/versioned_docs/version-latest/ui/preferences/application/behavior.md
@@ -14,7 +14,7 @@ Allows for configuration of application behavior upon startup, background proces
-
+
#### Startup
@@ -39,7 +39,7 @@ Rancher Desktop shows the application status with a notification icon. The conte
-
+
#### Startup
@@ -64,7 +64,7 @@ Rancher Desktop shows the application status with a notification icon in the men
-
+
#### Startup
diff --git a/versioned_docs/version-latest/ui/preferences/application/environment.md b/versioned_docs/version-latest/ui/preferences/application/environment.md
index 7ba56565b5..f6c3dcadf5 100644
--- a/versioned_docs/version-latest/ui/preferences/application/environment.md
+++ b/versioned_docs/version-latest/ui/preferences/application/environment.md
@@ -14,7 +14,7 @@ Allows for configuration of the `$PATH` variable in the users shell in order to
-
+
#### Configure PATH
@@ -30,7 +30,7 @@ There are two options for doing this:
-
+
#### Configure PATH
diff --git a/versioned_docs/version-latest/ui/preferences/application/general.md b/versioned_docs/version-latest/ui/preferences/application/general.md
index 7a6e40b158..0a1d928bc8 100644
--- a/versioned_docs/version-latest/ui/preferences/application/general.md
+++ b/versioned_docs/version-latest/ui/preferences/application/general.md
@@ -14,7 +14,7 @@ Allows for enablement of automatic updates, as well as an optional field to allo
-
+
#### Automatic Updates
@@ -29,7 +29,7 @@ This option allows Rancher Desktop to collect information on how you interact wi
-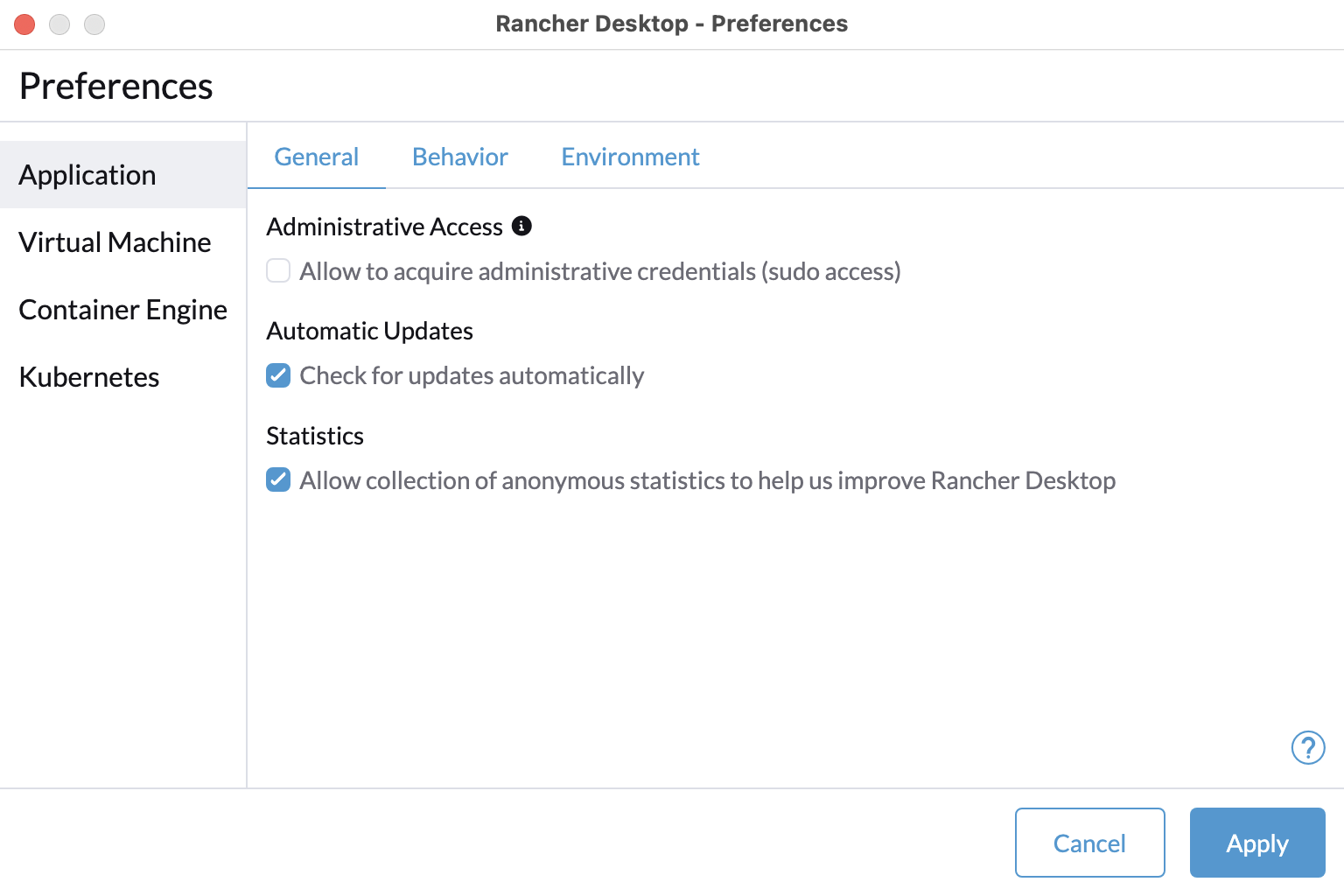
+
#### Administrative Access
@@ -48,7 +48,7 @@ This option allows Rancher Desktop to collect information on how you interact wi
-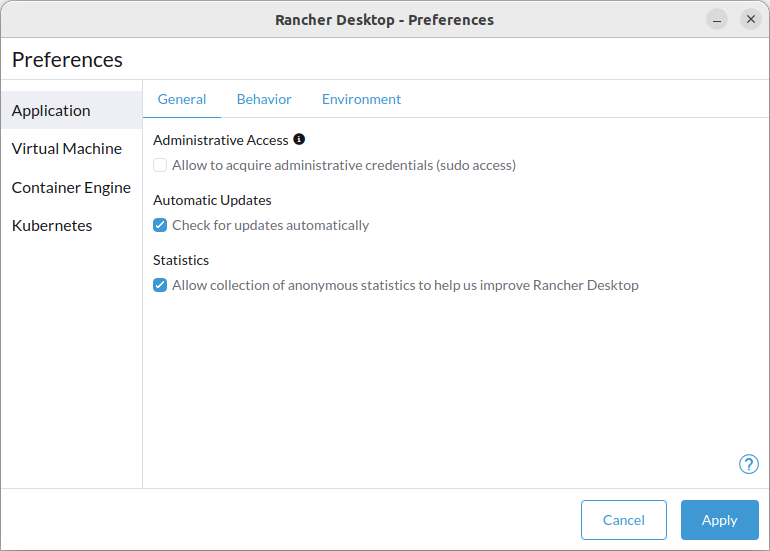
+
#### Administrative Access
diff --git a/versioned_docs/version-latest/ui/preferences/container-engine/allowed-images.md b/versioned_docs/version-latest/ui/preferences/container-engine/allowed-images.md
index 2b624c7f5b..514e9fbb76 100644
--- a/versioned_docs/version-latest/ui/preferences/container-engine/allowed-images.md
+++ b/versioned_docs/version-latest/ui/preferences/container-engine/allowed-images.md
@@ -14,17 +14,17 @@ The `Allowed Images` tab lets you control which registry artifacts you can acces
-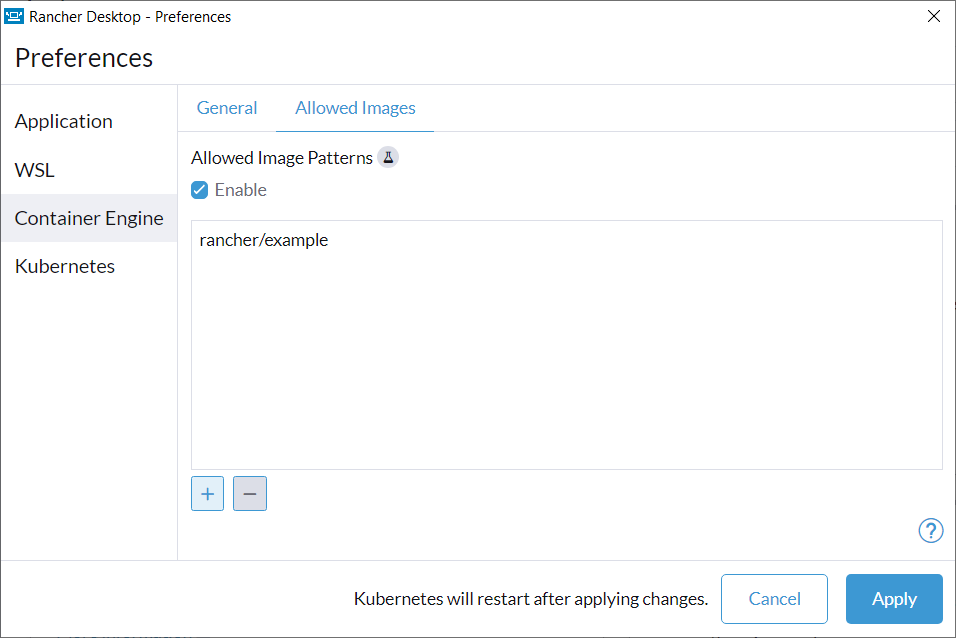
+
-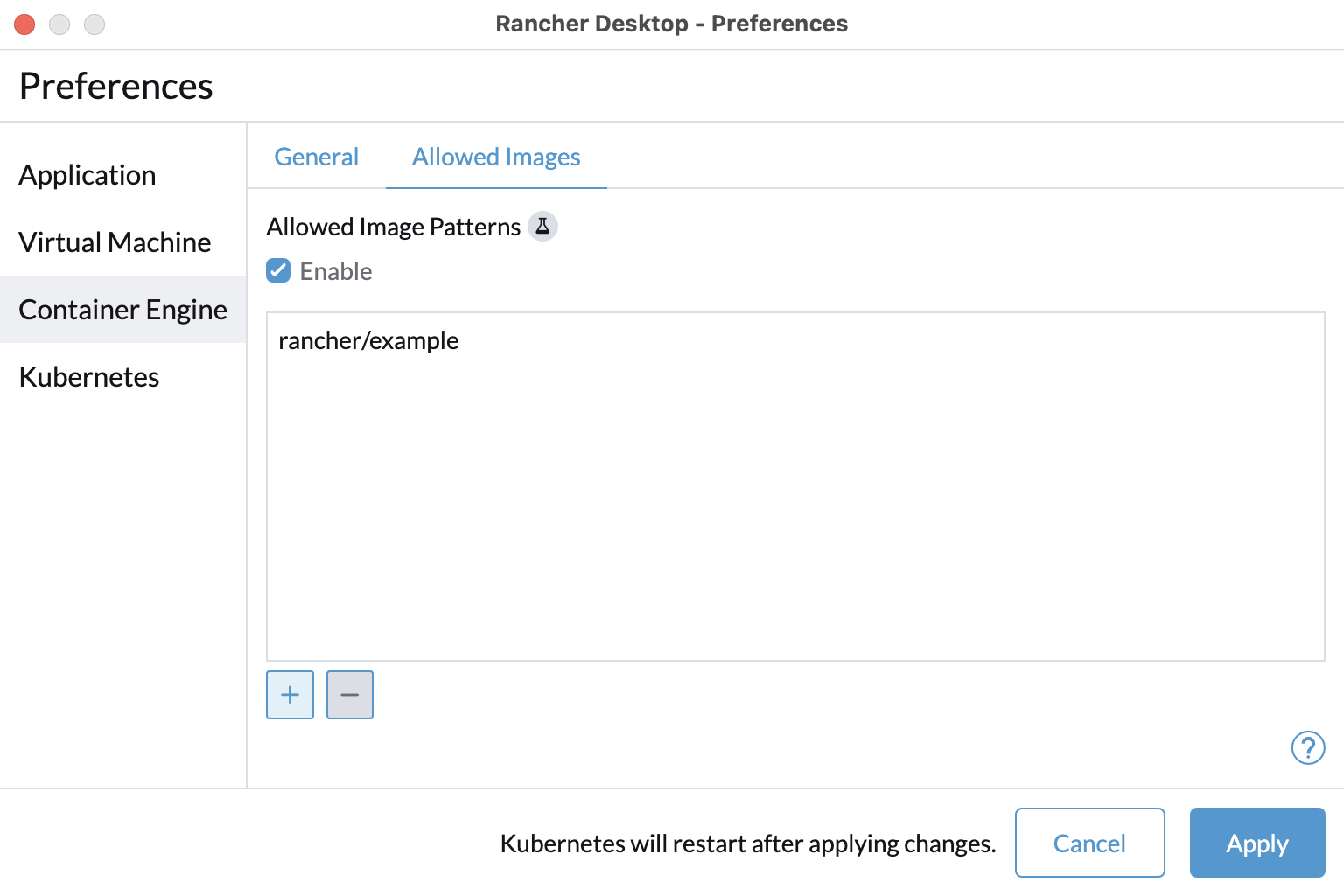
+
-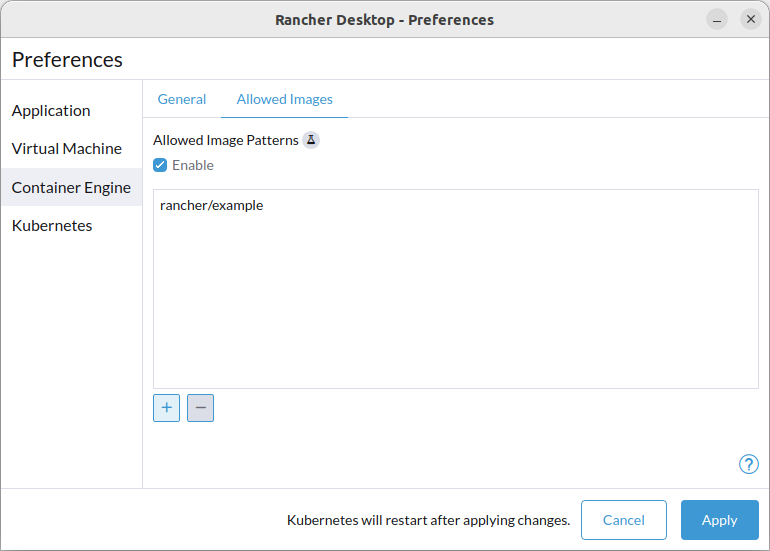
+
diff --git a/versioned_docs/version-latest/ui/preferences/container-engine/general.md b/versioned_docs/version-latest/ui/preferences/container-engine/general.md
index acb2eab349..9d3401c41e 100644
--- a/versioned_docs/version-latest/ui/preferences/container-engine/general.md
+++ b/versioned_docs/version-latest/ui/preferences/container-engine/general.md
@@ -14,17 +14,17 @@ Set the [container runtime] for Rancher Desktop. Users have the option of [conta
-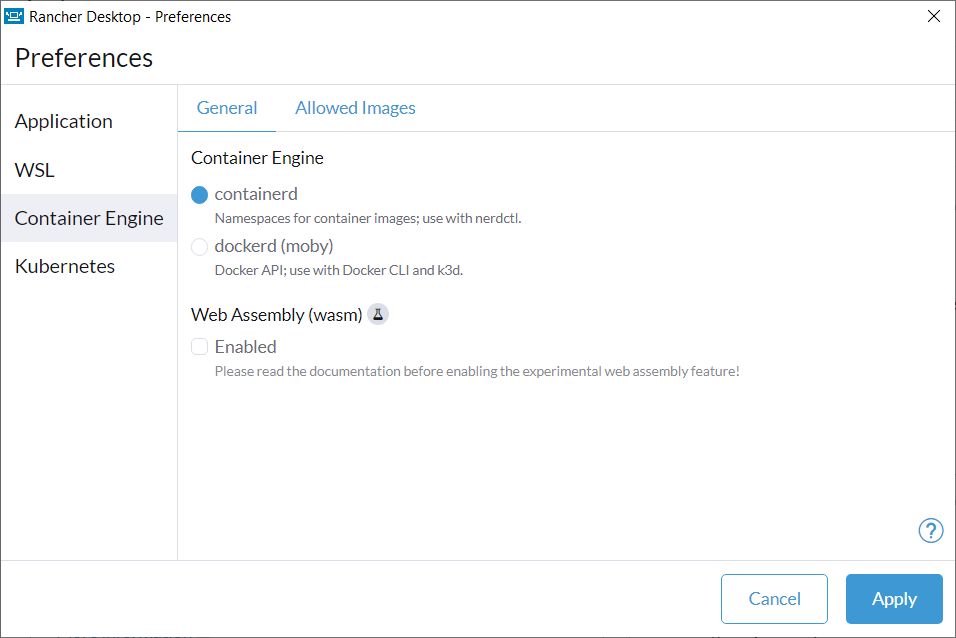
+
-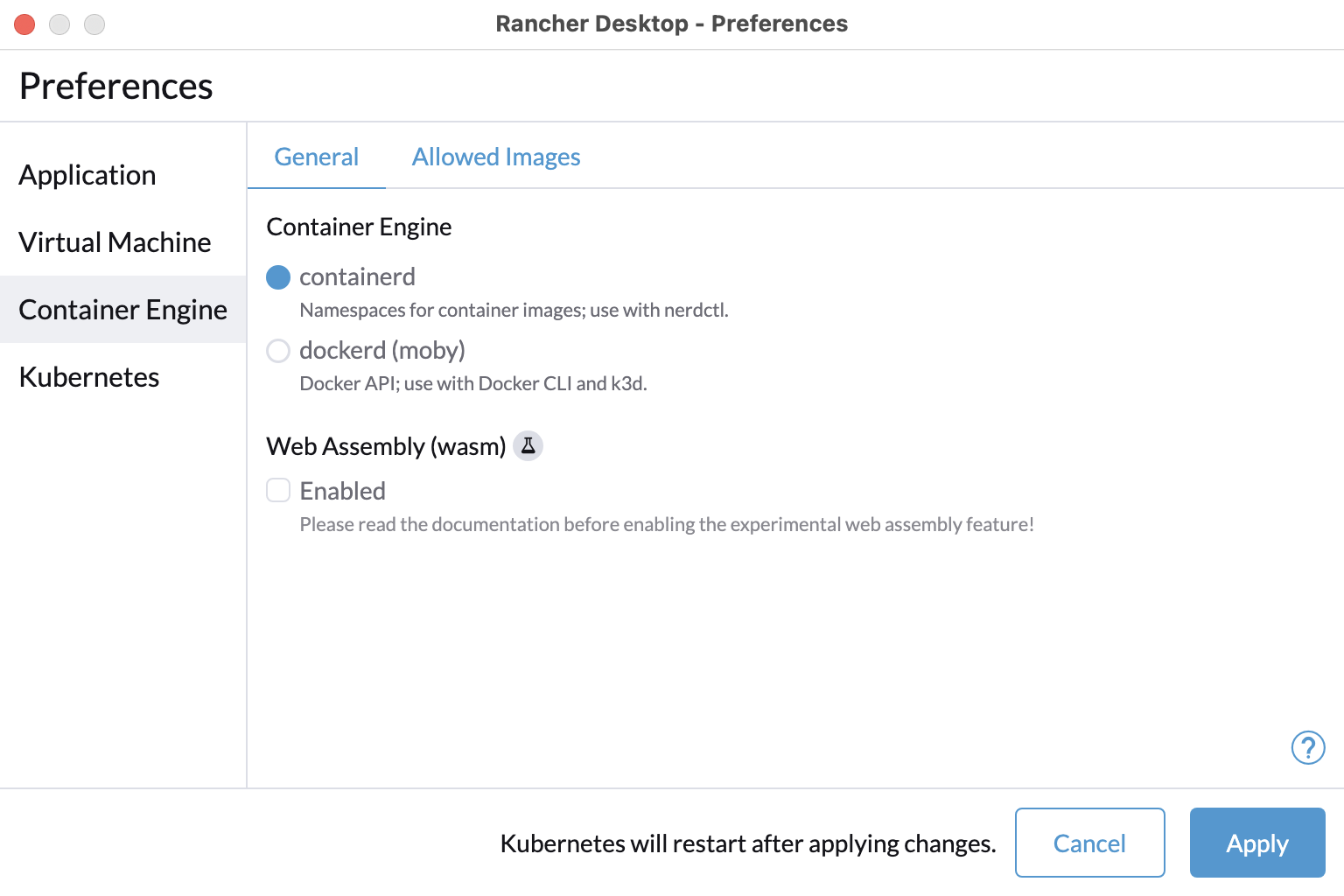
+
-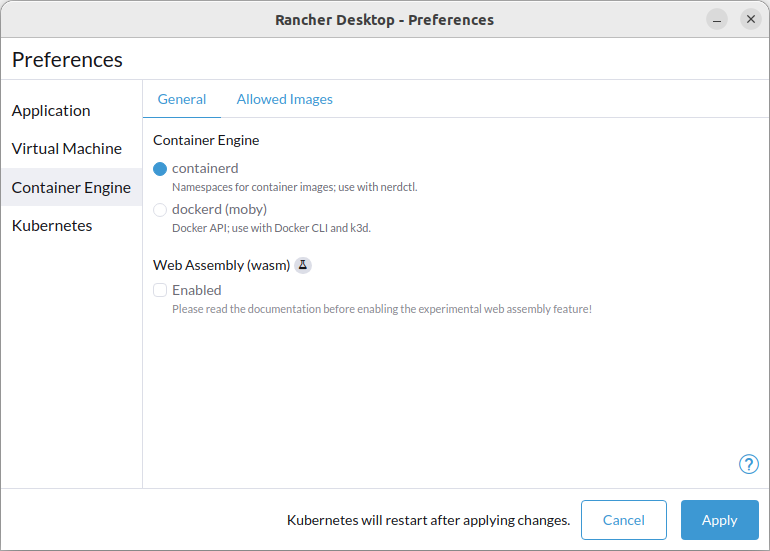
+
@@ -33,7 +33,13 @@ Set the [container runtime] for Rancher Desktop. Users have the option of [conta
When switching to a different container runtime: Workloads and images that have been built or pulled using the current container runtime are not available on the container runtime being switched to.
-#### WebAssembly (wasm)
+#### WebAssembly (Wasm)
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
The Wasm feature allows running WebAssembly application as containers, either directly with the container engine, or via Kubernetes. Details are available in the [Working with WebAssembly](../../../tutorials/working-with-webassembly.md) tutorial.
diff --git a/versioned_docs/version-latest/ui/preferences/kubernetes.md b/versioned_docs/version-latest/ui/preferences/kubernetes.md
index 471cf9f4d9..38146b7183 100644
--- a/versioned_docs/version-latest/ui/preferences/kubernetes.md
+++ b/versioned_docs/version-latest/ui/preferences/kubernetes.md
@@ -12,17 +12,17 @@ import TabsConstants from '@site/core/TabsConstants';
-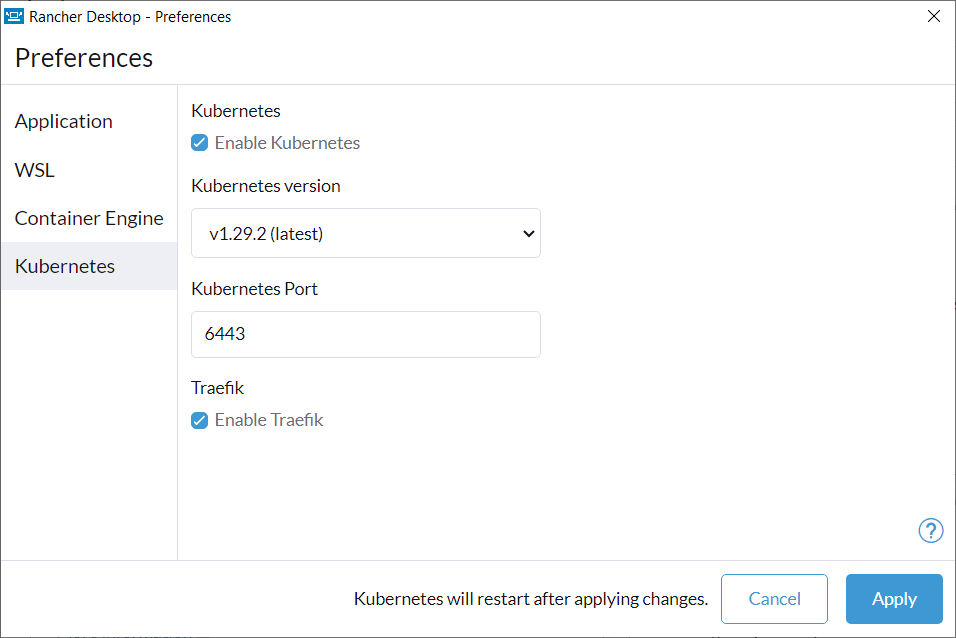
+
-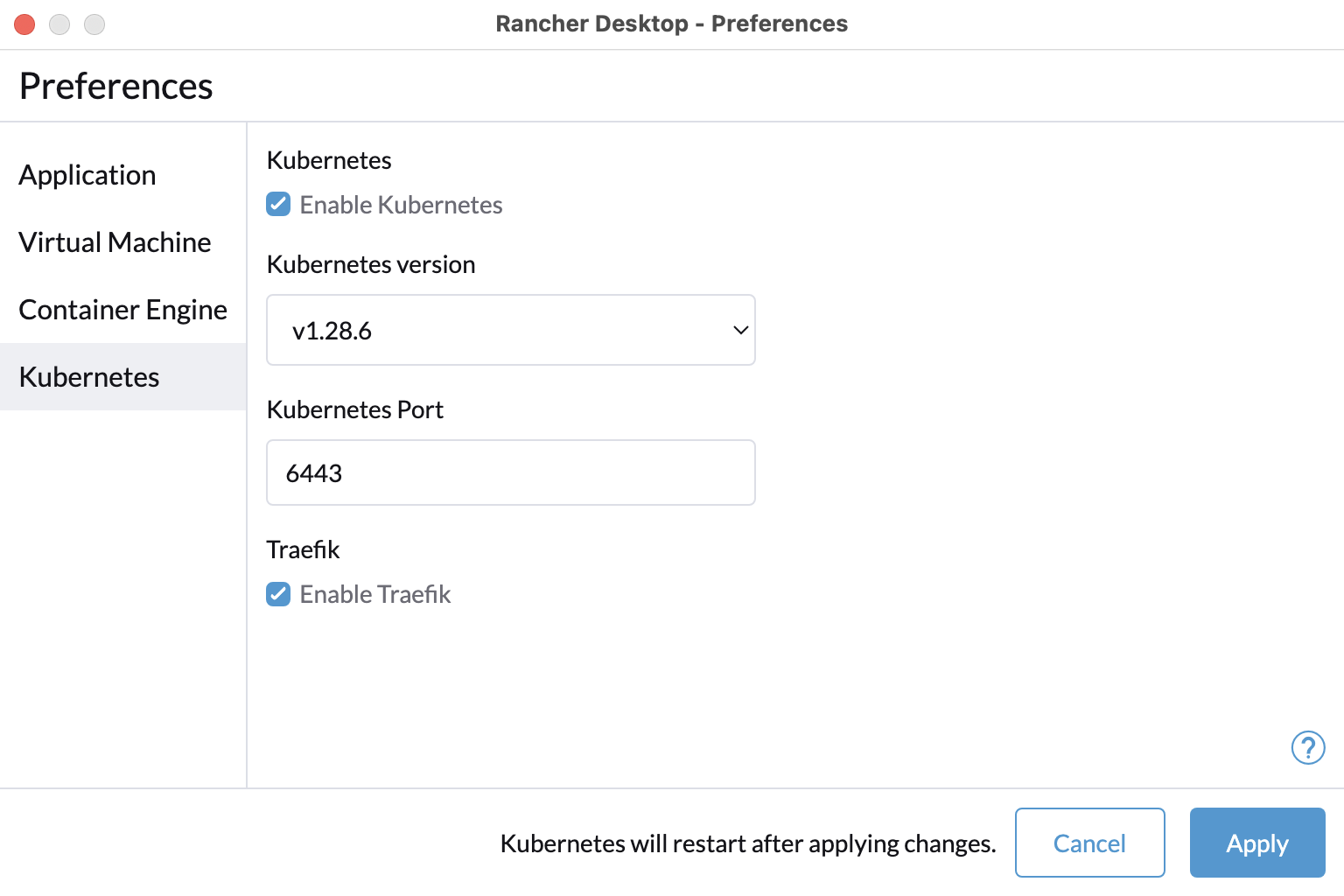
+
-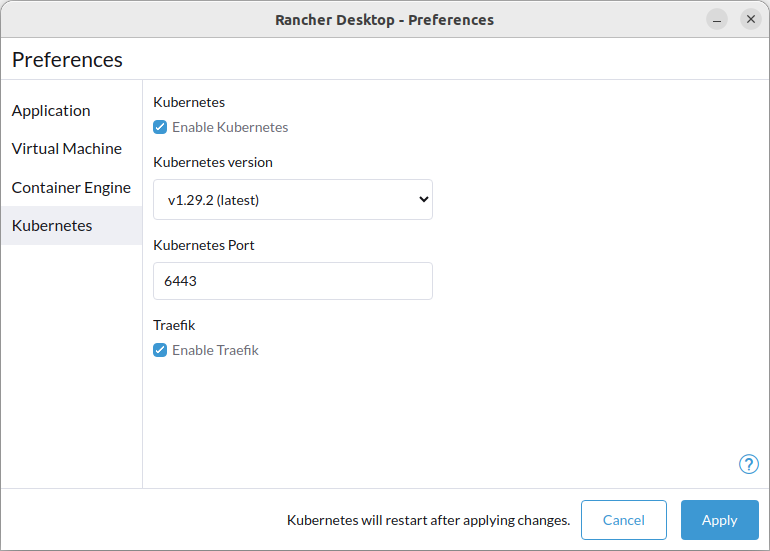
+
@@ -57,8 +57,28 @@ To switch versions:
Set the port Kubernetes is exposed on. Use this setting to avoid port collisions if multiple instances of K3s are running.
-#### Enable Traefik
+#### Options
+
+##### Enable Traefik
This option allows you to enable or disable Traefik. By disabling Traefik, you can free up port 80 and 443 for alternate ingress configuration. By default, Traefik is enabled.
Disabling Traefik will not delete existing resources.
+
+##### Install Spin Operator
+
+:::caution warning
+
+This is an **experimental** setting.
+
+:::
+
+This option will install the [spinkube](https://www.spinkube.dev/) operator with the `cert-manager` prerequisite, and configure it with the `spin` RuntimeClass.
+
+This option requires that the [WebAssembly](./container-engine/general.md) support is enabled.
+
+:::note
+
+Rancher Desktop automatically installs the [spin cli](https://developer.fermyon.com/spin/v2/index) and the [kube plugin](https://github.com/spinkube/spin-plugin-kube) to help develop and deploy Spin applications on Kubernetes.
+
+:::
diff --git a/versioned_docs/version-latest/ui/preferences/virtual-machine/emulation.md b/versioned_docs/version-latest/ui/preferences/virtual-machine/emulation.md
index 4b46f092ad..1665fbebf8 100644
--- a/versioned_docs/version-latest/ui/preferences/virtual-machine/emulation.md
+++ b/versioned_docs/version-latest/ui/preferences/virtual-machine/emulation.md
@@ -9,13 +9,13 @@ title: Emulation (macOS)
### QEMU
- 
+ 
The [**QEMU**](https://www.qemu.org/documentation/) option is enabled by default and turns on a guest operating system. You can switch the virtual machine type after the first run.
### VZ
- 
+ 
:::caution warning
diff --git a/versioned_docs/version-latest/ui/preferences/virtual-machine/hardware.md b/versioned_docs/version-latest/ui/preferences/virtual-machine/hardware.md
index fba7c4459b..d813e1884a 100644
--- a/versioned_docs/version-latest/ui/preferences/virtual-machine/hardware.md
+++ b/versioned_docs/version-latest/ui/preferences/virtual-machine/hardware.md
@@ -12,12 +12,12 @@ import TabsConstants from '@site/core/TabsConstants';
-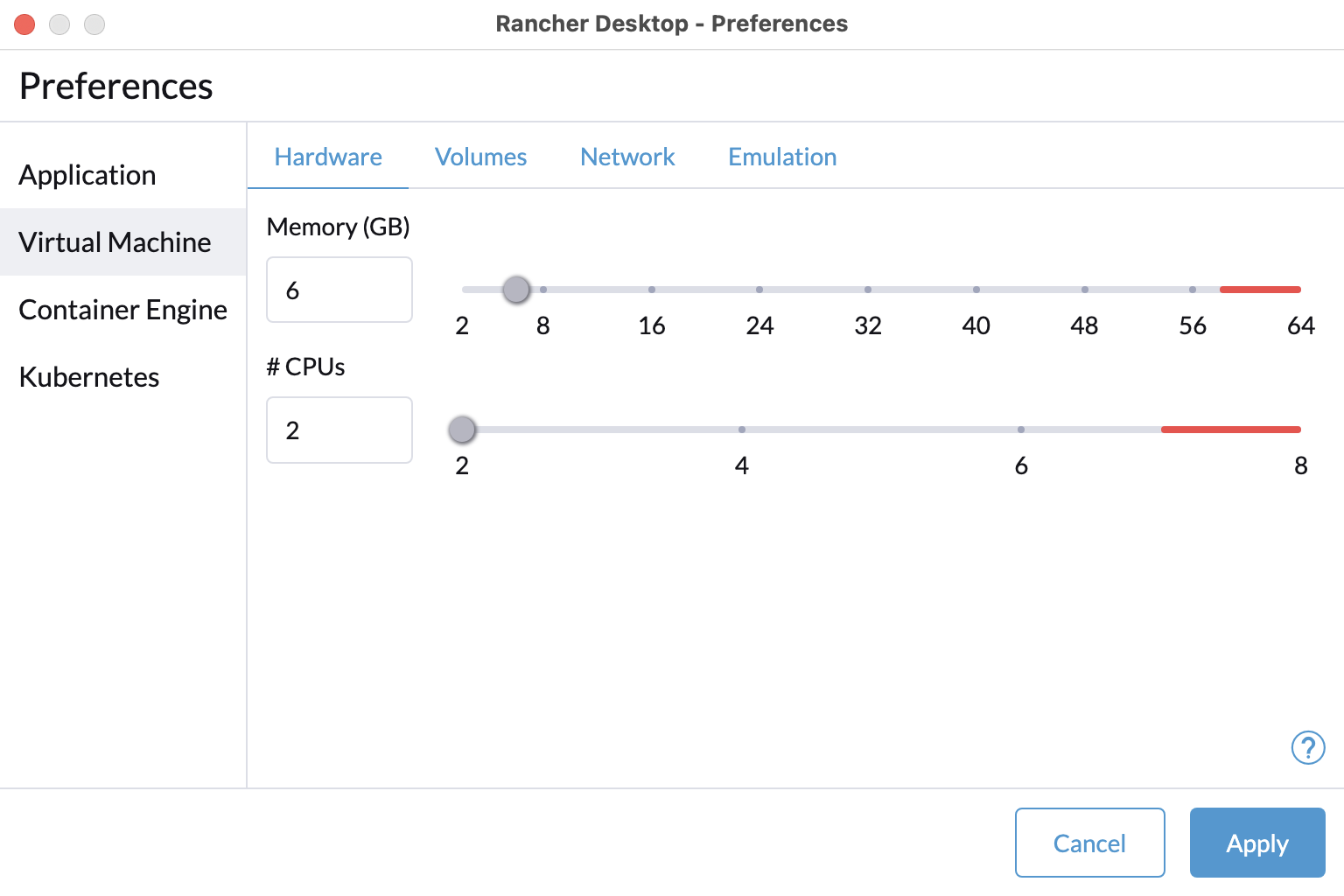
+
-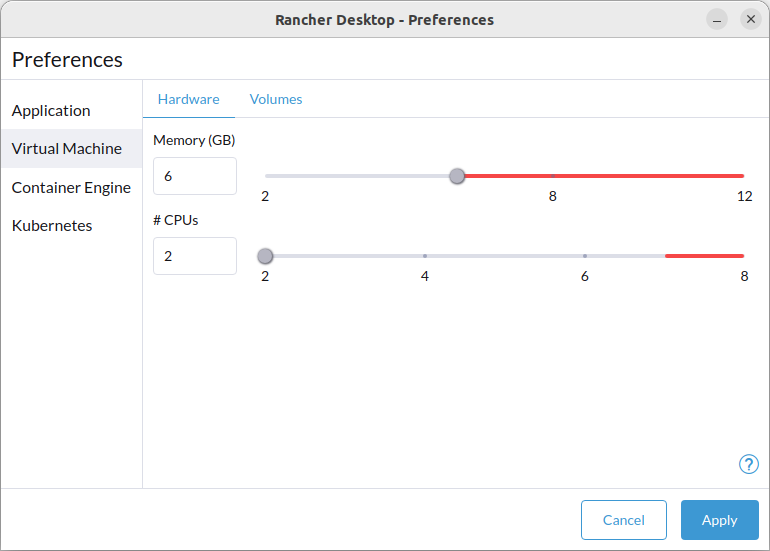
+
diff --git a/versioned_docs/version-latest/ui/preferences/virtual-machine/network.md b/versioned_docs/version-latest/ui/preferences/virtual-machine/network.md
index 81dfe523c8..39158d4b62 100644
--- a/versioned_docs/version-latest/ui/preferences/virtual-machine/network.md
+++ b/versioned_docs/version-latest/ui/preferences/virtual-machine/network.md
@@ -7,7 +7,7 @@ title: Network (macOS)
-
+
### Enable `socket-vmnet`
diff --git a/versioned_docs/version-latest/ui/preferences/virtual-machine/volumes.md b/versioned_docs/version-latest/ui/preferences/virtual-machine/volumes.md
index bb323f3303..6ab5093fc6 100644
--- a/versioned_docs/version-latest/ui/preferences/virtual-machine/volumes.md
+++ b/versioned_docs/version-latest/ui/preferences/virtual-machine/volumes.md
@@ -16,12 +16,12 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-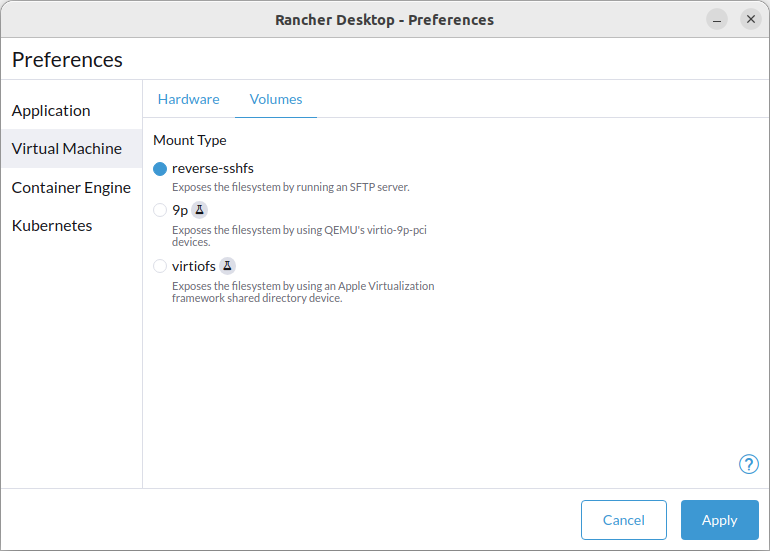
+
@@ -33,12 +33,12 @@ Users can enable the "[reverse-sshfs](https://github.com/lima-vm/lima/blob/maste
-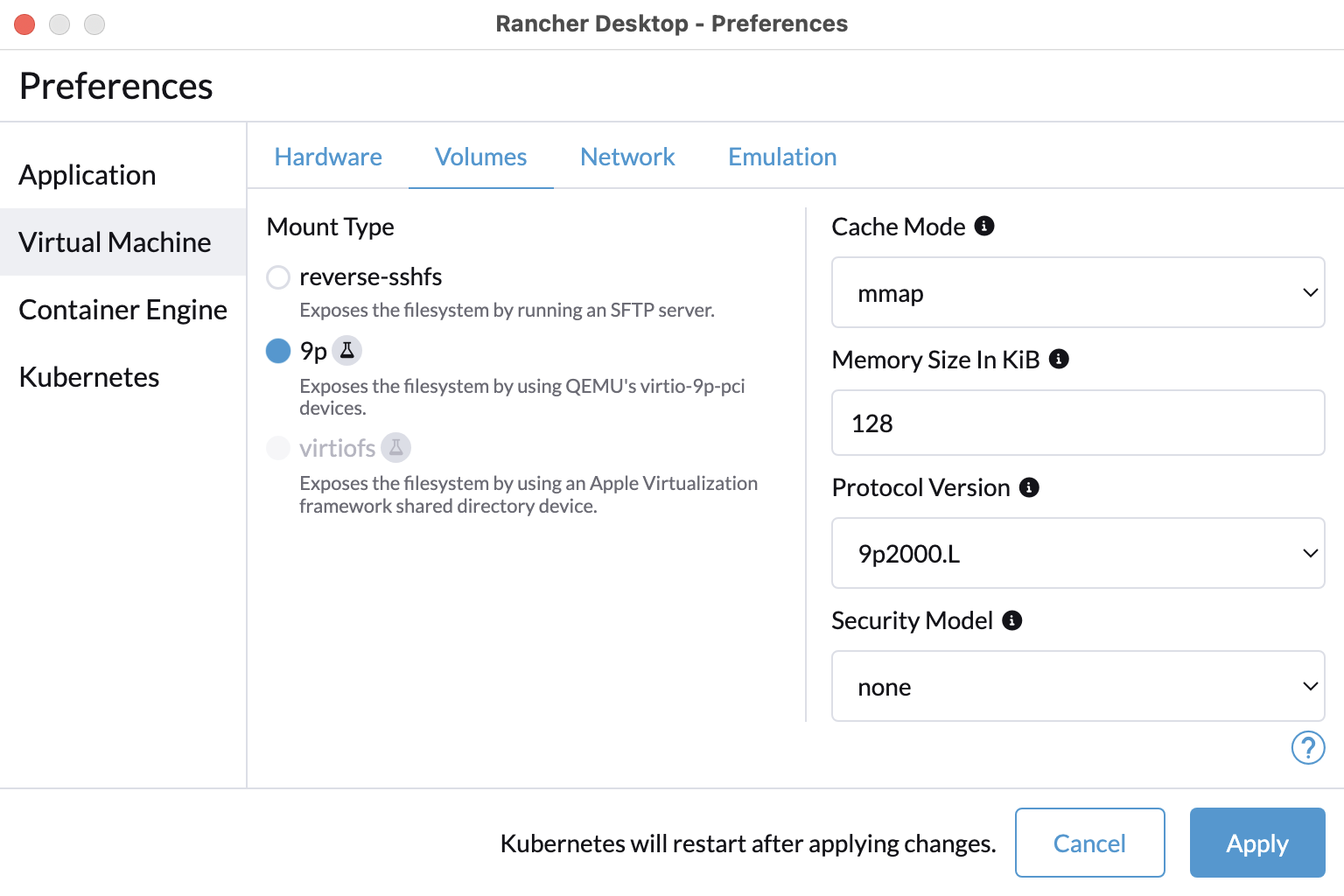
+
-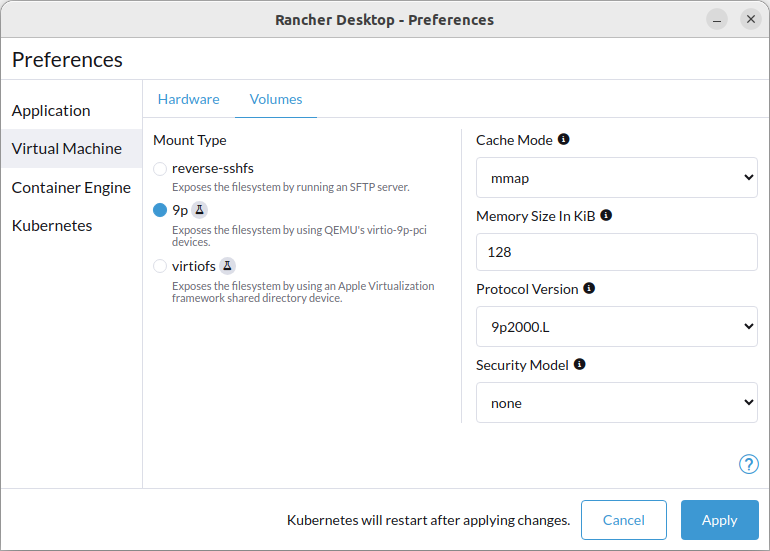
+
@@ -68,12 +68,12 @@ Users can select a supported security model with options being `[passthrough, ma
-
+
-
+
diff --git a/versioned_docs/version-latest/ui/preferences/wsl/integrations.md b/versioned_docs/version-latest/ui/preferences/wsl/integrations.md
index cfba5e7799..87114b0cae 100644
--- a/versioned_docs/version-latest/ui/preferences/wsl/integrations.md
+++ b/versioned_docs/version-latest/ui/preferences/wsl/integrations.md
@@ -9,21 +9,25 @@ title: Integrations
The Integrations tab allows for the option to make the Rancher Desktop Kubernetes configuration accessible to any Linux distributions configured for WSL. Once enabled, you can communicate with the Rancher Desktop Kubernetes cluster using tools like `kubectl` from within the WSL distribution.
-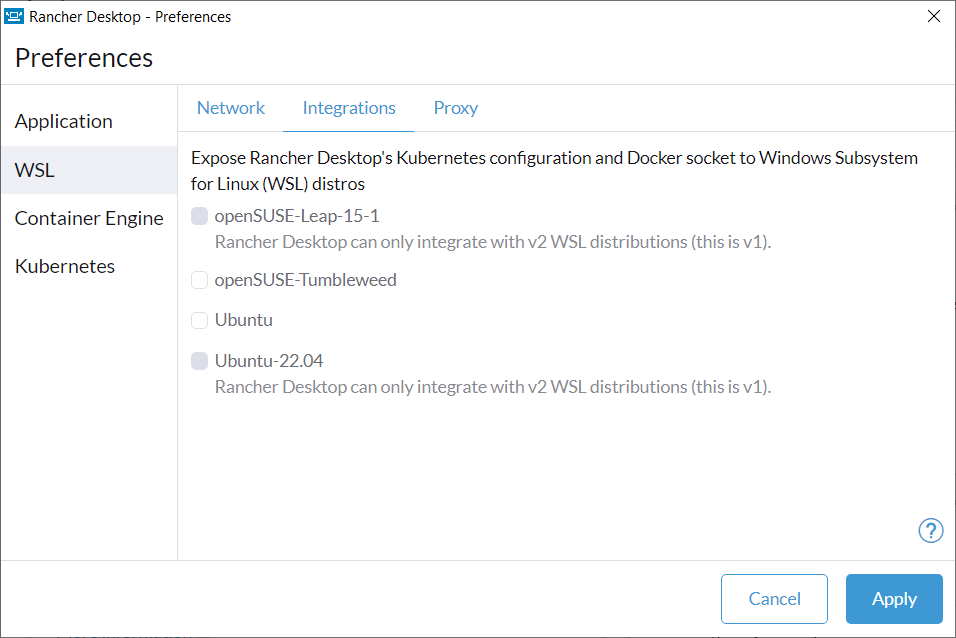
+
With WSL, memory and CPU allocation is configured globally across all Linux distributions. Refer to the [WSL documentation] for instructions.
[WSL documentation]:
https://docs.microsoft.com/en-us/windows/wsl/wsl-config#options-for-wslconfig
-:::caution warning: breaking change
+### `~/.kube/config`
-:::
+Rancher Desktop will create a symlink from `~/.kube/config` inside the distro to the corresponding `%USERPROFILE%\.kube\config` file on the Windows filesystem.
+
+If the `~/.kube/config` file already exists inside the distro and contains only `rancher-desktop` contexts, users, and clusters then it will be deleted and replaced with the symlink.
-Starting with version `1.11.1`, Rancher Desktop no longer supports a symlink from the `~/.kube/config` file to the instance on your Windows filesystem. This is due to the Kubernetes endpoint differing between the Windows host and inside a WSL2 distribution. The application will replace found symlinks with a separate file instead.
+If it contains any other information then the file will not be modified and the user has to update the Rancher Desktop cluster information manually. In that case the "Kubernetes context" menu entry for the notification icon will show (and change) the context for the Win32 side only. The contexts inside distributions will need to be managed manually from a command prompt.
-If the file inside the distribution is a separate file, or a symlink to any other location, then Rancher Desktop will update that file with the `rancher-desktop` context.
+:::caution info
-However, if the file is a symlink to the default location on the host, then Rancher Desktop will delete it and create a new file with the cluster configuration that works from inside the distribution.
+In Rancher Desktop `1.11.1` and `1.12.*` the `~/.kube/config` file was converted from a symlink into a regular file because the network tunnelling option required a different Kubernetes endpoint inside WSL clusters than on the host.
-Consequently, the "Kubernetes context" menu entry for the notification will show (and change) the context for the Win32 side only. The contexts inside distributions will need to be managed manually from a command prompt.
+Rancher Desktop `1.13.0` added a network proxy between the cluster and the other distros, so the endpoint is the same again as on the host. If the `~/.kube/config` file only references the `rancher-desktop` cluster then it will automatically be converted into a symlink again. Otherwise the user need to consolidate the different files manually.
+
+:::
diff --git a/versioned_docs/version-latest/ui/preferences/wsl/network.md b/versioned_docs/version-latest/ui/preferences/wsl/network.md
index a79ba5c0dc..eb25c3a0bc 100644
--- a/versioned_docs/version-latest/ui/preferences/wsl/network.md
+++ b/versioned_docs/version-latest/ui/preferences/wsl/network.md
@@ -7,7 +7,7 @@ title: Network (Windows)
-
+
### Networking Tunnel
diff --git a/versioned_docs/version-latest/ui/preferences/wsl/proxy.md b/versioned_docs/version-latest/ui/preferences/wsl/proxy.md
index 315e518b54..3698326a34 100644
--- a/versioned_docs/version-latest/ui/preferences/wsl/proxy.md
+++ b/versioned_docs/version-latest/ui/preferences/wsl/proxy.md
@@ -7,7 +7,7 @@ title: Proxy
-
+
### WSL Proxy
diff --git a/versioned_docs/version-latest/ui/snapshots.md b/versioned_docs/version-latest/ui/snapshots.md
index c46031d7c1..67b33cf606 100644
--- a/versioned_docs/version-latest/ui/snapshots.md
+++ b/versioned_docs/version-latest/ui/snapshots.md
@@ -12,17 +12,17 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-
+
-
+
diff --git a/versioned_docs/version-latest/ui/troubleshooting.md b/versioned_docs/version-latest/ui/troubleshooting.md
index cd4983e753..59686f38bd 100644
--- a/versioned_docs/version-latest/ui/troubleshooting.md
+++ b/versioned_docs/version-latest/ui/troubleshooting.md
@@ -12,17 +12,17 @@ import TabsConstants from '@site/core/TabsConstants';
-
+
-
+
-
+
diff --git a/versioned_sidebars/version-1.14-sidebars.json b/versioned_sidebars/version-1.14-sidebars.json
new file mode 100644
index 0000000000..cd88ea462d
--- /dev/null
+++ b/versioned_sidebars/version-1.14-sidebars.json
@@ -0,0 +1,115 @@
+{
+ "tutorialSidebar": [
+ {
+ "type": "category",
+ "label": "Getting Started",
+ "items": [
+ "getting-started/introduction",
+ "getting-started/installation",
+ "getting-started/deployment"
+ ],
+ "collapsed": false
+ },
+ {
+ "type": "category",
+ "label": "User Interface",
+ "items": [
+ "ui/general",
+ "ui/containers",
+ "ui/port-forwarding",
+ "ui/images",
+ "ui/snapshots",
+ "ui/troubleshooting",
+ "ui/diagnostics",
+ "ui/extensions",
+ {
+ "type": "category",
+ "label": "Preferences",
+ "items": [
+ {
+ "type": "category",
+ "label": "Application",
+ "items": [
+ "ui/preferences/application/general",
+ "ui/preferences/application/behavior",
+ "ui/preferences/application/environment"
+ ]
+ },
+ {
+ "type": "category",
+ "label": "Virtual Machine",
+ "items": [
+ "ui/preferences/virtual-machine/emulation",
+ "ui/preferences/virtual-machine/hardware",
+ "ui/preferences/virtual-machine/network",
+ "ui/preferences/virtual-machine/volumes"
+ ]
+ },
+ {
+ "type": "category",
+ "label": "WSL",
+ "items": [
+ "ui/preferences/wsl/integrations",
+ "ui/preferences/wsl/network",
+ "ui/preferences/wsl/proxy"
+ ]
+ },
+ {
+ "type": "category",
+ "label": "Container Engine",
+ "items": [
+ "ui/preferences/container-engine/general",
+ "ui/preferences/container-engine/allowed-images"
+ ]
+ },
+ "ui/preferences/kubernetes"
+ ]
+ }
+ ]
+ },
+ {
+ "type": "category",
+ "label": "Tutorials",
+ "items": [
+ "tutorials/working-with-images",
+ "tutorials/working-with-containers",
+ "tutorials/working-with-webassembly",
+ "tutorials/using-persistent-storage"
+ ]
+ },
+ {
+ "type": "category",
+ "label": "How-to Guides",
+ "items": [
+ "how-to-guides/generating-deployment-profiles",
+ "how-to-guides/hello-world-example",
+ "how-to-guides/installing-uninstalling-extensions",
+ "how-to-guides/transfer-container-images",
+ "how-to-guides/create-multi-node-cluster",
+ "how-to-guides/setup-NGINX-Ingress-Controller",
+ "how-to-guides/vs-code-docker",
+ "how-to-guides/vs-code-remote-containers",
+ "how-to-guides/rancher-on-rancher-desktop",
+ "how-to-guides/skaffold-and-rancher-desktop",
+ "how-to-guides/provisioning-scripts",
+ "how-to-guides/increasing-open-file-limit",
+ "how-to-guides/running-air-gapped",
+ "how-to-guides/odo-rancher-desktop",
+ "how-to-guides/traefik-ingress-example",
+ "how-to-guides/using-testcontainers",
+ "how-to-guides/mirror-private-registry"
+ ]
+ },
+ {
+ "type": "category",
+ "label": "References",
+ "items": [
+ "references/architecture",
+ "references/rdctl-command-reference",
+ "references/bundled-utilities"
+ ]
+ },
+ "faq",
+ "troubleshooting-tips"
+ ]
+}
diff --git a/versions.json b/versions.json
index a9ff289661..c3b037ddc5 100644
--- a/versions.json
+++ b/versions.json
@@ -1,5 +1,6 @@
[
"latest",
+ "1.14",
"1.13",
"1.12",
"1.11",