This is that scan the vulnerability of Docker images stored in ECR.
- Pull Docker Image From ECR
- Support multi account
- Vulnerability Scan
- Trivy detects software (OS package and application library) vulnerabilities in Docker Image
- Slack Integration
- Trivy
- Git (Used with Trivy)
pip install ecranner
A ecranner.yml looks like this:
aws:
stg:
account_id: xxxxxxxxx
region: us-east-1
aws_access_key_id: xxxxxxxxx
aws_secret_access_key: xxxxxxxxx
images:
- image:latest
- image:1.0-dev
prod:
account_id: xxxxxxxxx
region: us-east-1
aws_access_key_id: xxxxxxxxx
aws_secret_access_key: xxxxxxxxx
images:
- image:1.4
- image:5.3
trivy:
path: ~/user/.local/bin/trivy
options: --severity CRITICAL -q
ecranner
You execute the above and then output the scan result to the console as follows:
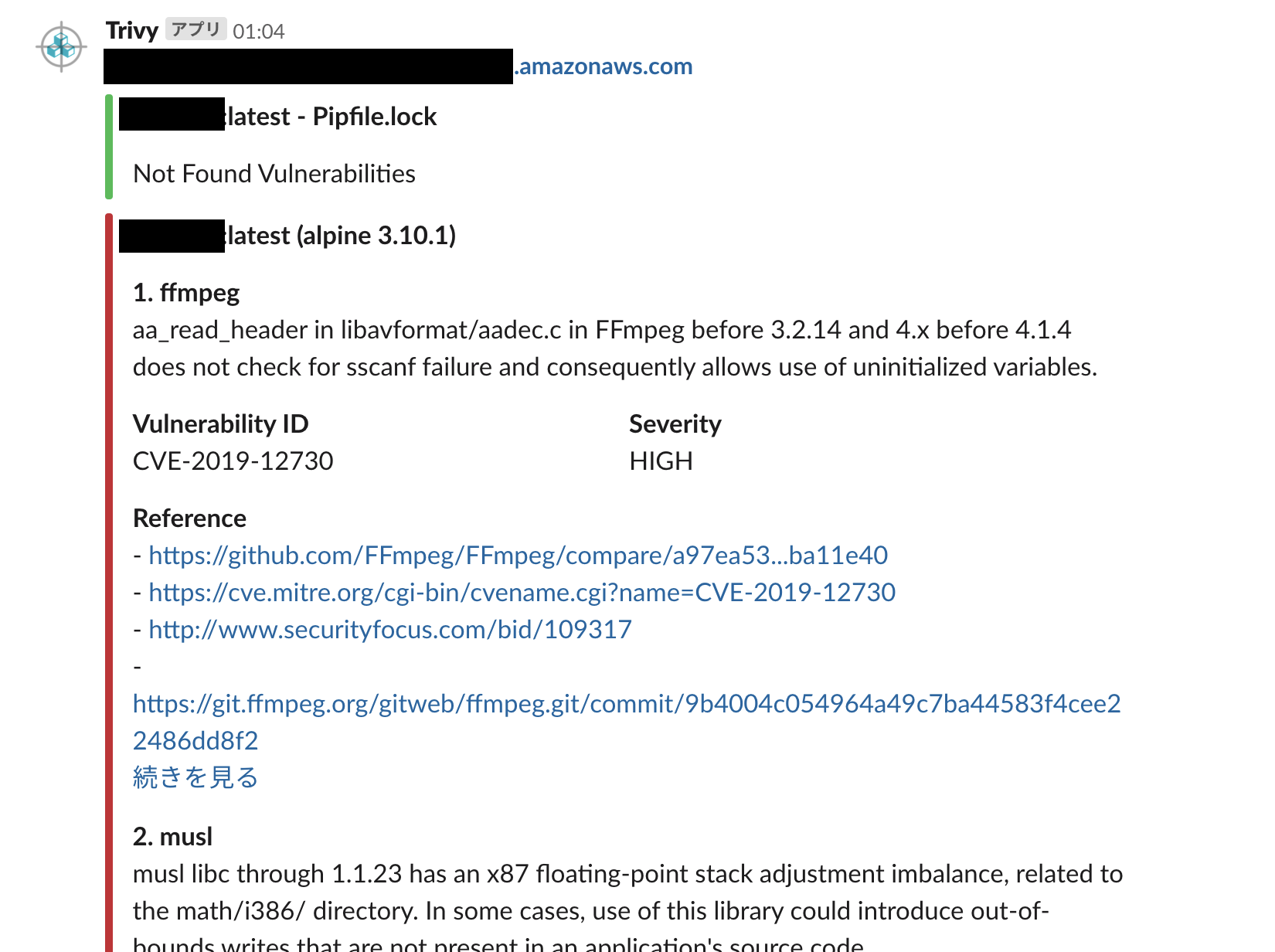
[ { 'Target': 'image_name:latest'
'(alpine 3.10.1)',
'Vulnerabilities': [ { 'Description': 'aa_read_header in '
'libavformat/aadec.c in FFmpeg '
'before 3.2.14 and 4.x before 4.1.4 '
'does not check for sscanf failure '
'and consequently allows use of '
'uninitialized variables.',
'FixedVersion': '4.1.4-r0',
'InstalledVersion': '4.1.3-r1',
'PkgName': 'ffmpeg',
'References': [ 'https://git.ffmpeg.org/gitweb/ffmpeg.git/shortlog/n4.1.4',
'https://github.com/FFmpeg/FFmpeg/commit/ed188f6dcdf0935c939ed813cf8745d50742014b',
'https://github.com/FFmpeg/FFmpeg/compare/a97ea53...ba11e40',
'https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-12730',
'http://www.securityfocus.com/bid/109317',
'https://git.ffmpeg.org/gitweb/ffmpeg.git/commit/9b4004c054964a49c7ba44583f4cee22486dd8f2'],
'Severity': 'HIGH',
'Title': '',
'VulnerabilityID': 'CVE-2019-12730'}
| option | required | default | description |
|---|---|---|---|
| -f, --file | false | ./ecranner.yml |
Filepath to configuration in YAML. Specify this option if you change configuration filename. |
| --env-file | false | ./.env |
Specify .env file path. Automatically load .env file if this file is found in current directory. |
| --slack | false | N/A | Send the scan result to Slack. If you use this option, set incoming webhooks url as system environment variable like this: export SLACK_WEBHOOK=https://xxxxxxxxxx |
| --rm | false | N/A | Remove images after scan with Trivy. |
| -q, --quiet | false | N/A | Suppress logging message. |
| --no-cache | false | N/A | Implement in the future, so you can not use this option Disable to store cache. This command does not use cache, but Trivy command use cache. |
| -h, --help | false | N/A | Show command option usage. |
Specify to use parameter in ecranner.yml.
Version 1.0 configuration parameters
Spefify version 1.0 as follows:
version: '1.0'First, declare that this configuration is for AWS.
<id> must be unique.
You are free to decide which word is <id>.
Your AWS account ID.
Specify the region where docker images to be pulled is stored.
Your IAM user's AWS access key ID.
Absolutely, you should not use AWS Root account for ECRanner.
Your IAM user's AWS secret access key.
Specify docker images that you want to pull.
Pull docker image with latest tag if not specify tag.
aws:
# omit
images:
- alpine:3.10
- ubuntu:18.04Set configuration for Trivy command.
Specify the path of trivy command.
You does not need to specify the path if trivy is installed in $PATH.
Set trivy command options as a one line string.
To send the scan result to Slack, the -f json option is already set.
You can specify all options except this option.
Please see Trivy documentation in details.
trivy:
options: --severity HIGH,CRITICAL -q --clear-cache