WPA2/WPA WIFI Drone hijack control by ROS with hackrf one fake GPS
Hong Kong Institute of Vocational Education (Chai Wan)
Information and Network Security (IT114104) Final Year Project
- Alex Wong - WIFI WPA/WPA2 hacking , Fake GPS and crack password
- Cherry Zhang - ROS (Parrot Bebop 2,DJI Tello) to take off , land down , take camera and open drone folder
- Sunny Chan - Main program , GUI deskgn , WIFI connection and server tools - Github
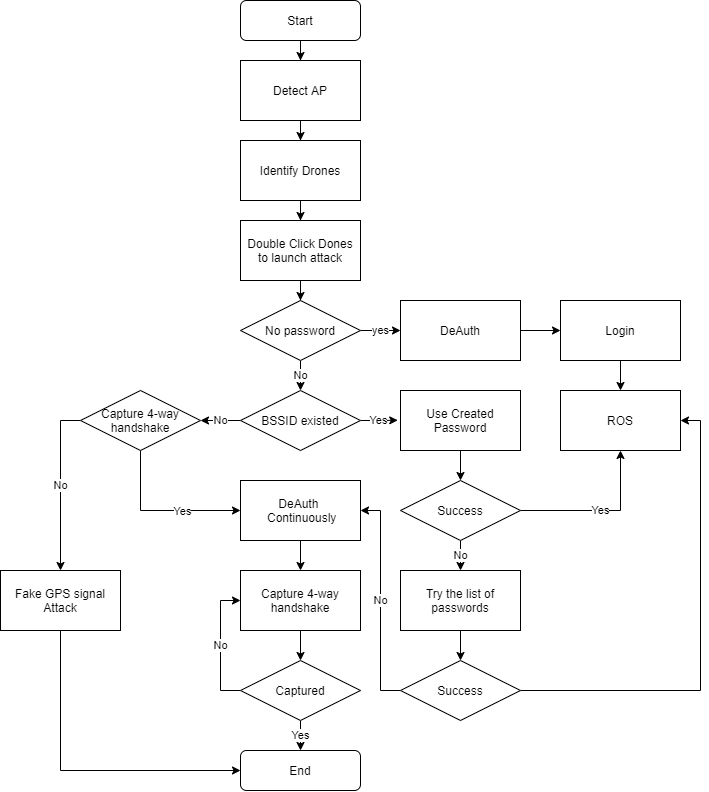
These instructions will provide you with a copy of the project running and running on your local computer for development and testing. For notes on how to deploy the project on a real-time system, see deployment.
Hardware
1. a Ubuntu 16.04 desktop (We set up in virtual machine)
2. two Wifi antenna (for the aircrack-ng)
3. a hackrf one(fakegps)
4. Drone (for testing e set up (Parrot Bebop 2,DJI Tello)
4. a server with powerful gpu (Used : pc with GTX1080 x 4 )
Software
1. Ubuntu 16.04 desktop
2. Aircrack-ng (tried verison 1.5.2)
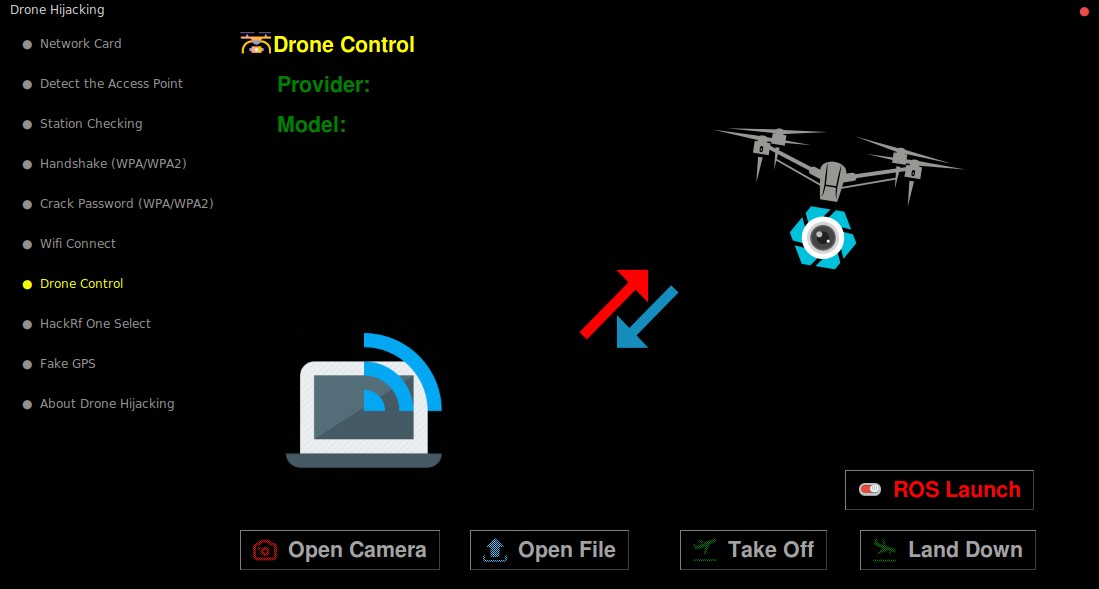
3. ROS ROS Kinetic (need to set up for each model of drone)
4. a hackrf one
5. Drone (for testing e set up (Parrot Bebop 2,DJI Tello)
6. Python3 with tkinter , ttk , threading , os , time , subprocess ,
csv , datetime , pyautogui , string , sys , requests,
re
7. nmap (Parrot Bebop 2 control)
8. Mplayer (DJI tello control)
9. xdotool (DJI tello control)
10.hackrf (hackrf on drive)
11.hashcat (for the server)
The ros of the drone:
- Parrot Bebop 2 (https://github.com/gsilano/BebopS)
- DJI Tello (https://github.com/hanyazou/TelloPy)
The set up will follow "/DroneControlCMD/sample.json"
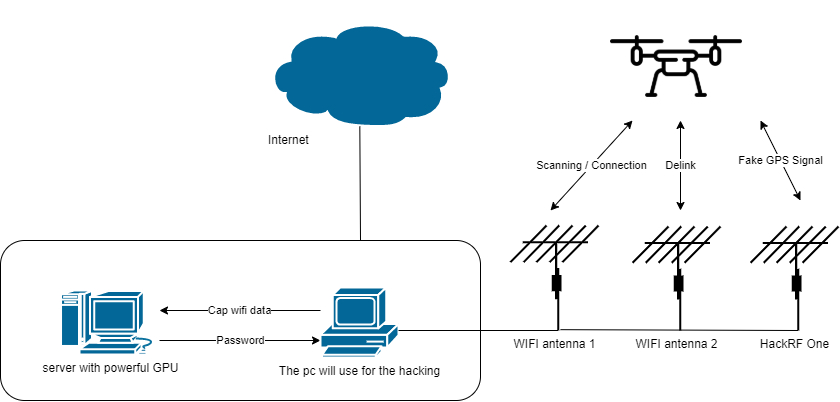
The set up environment will like this
Please keep the server (for crack password) and the pc can communication with each other For the api work please keep the pc connect to the internet
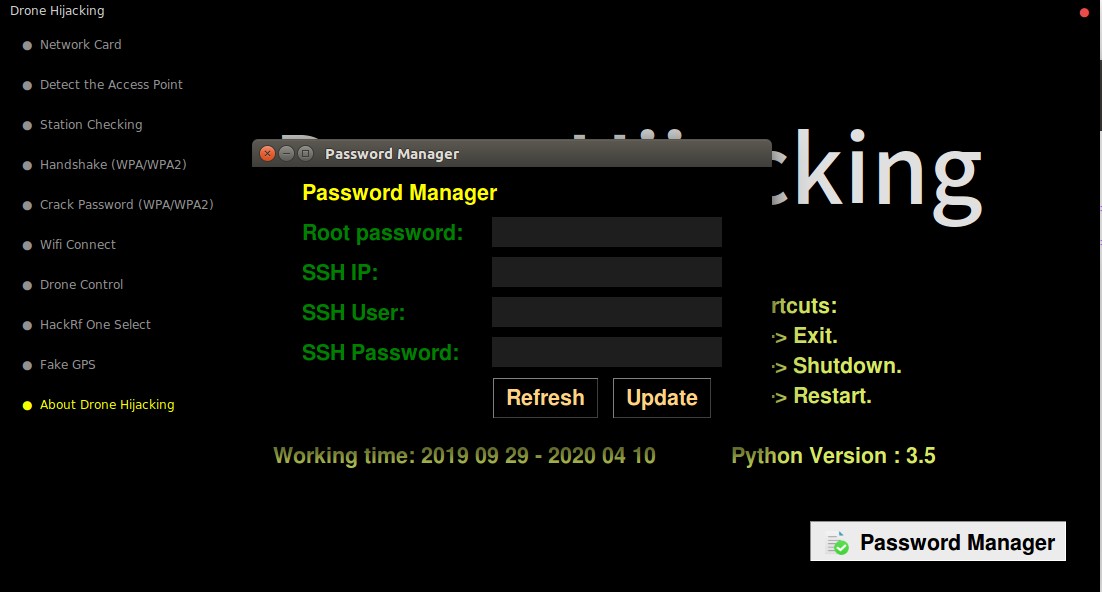
before launch software set up the "SystemInformation.txt"
rootPassword <Root_Password>
SSHIp <SSH_IP>
SSHUser <SSH_USER>
SSHPassword <SSH_Password>
Launch the software:
python3 FYP_GUI_NoRoot.py
Distributed under the GPL-3.0 License. See LICENSE for more information.
- "/CrackPasswdTools/hashcat-utils-master/": https://github.com/hashcat/hashcat-utils