GitHub Action
CVE Binary Tool
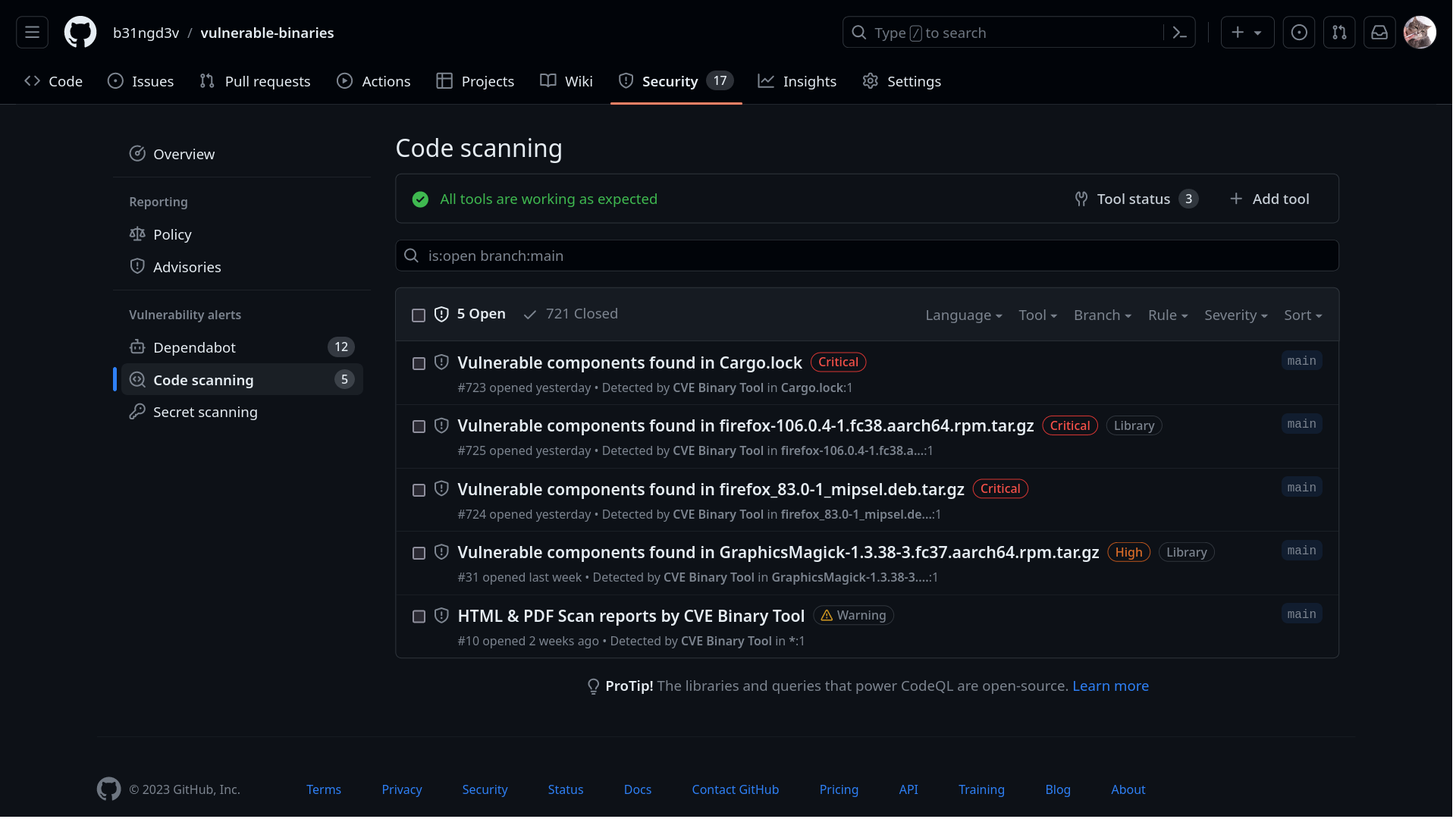
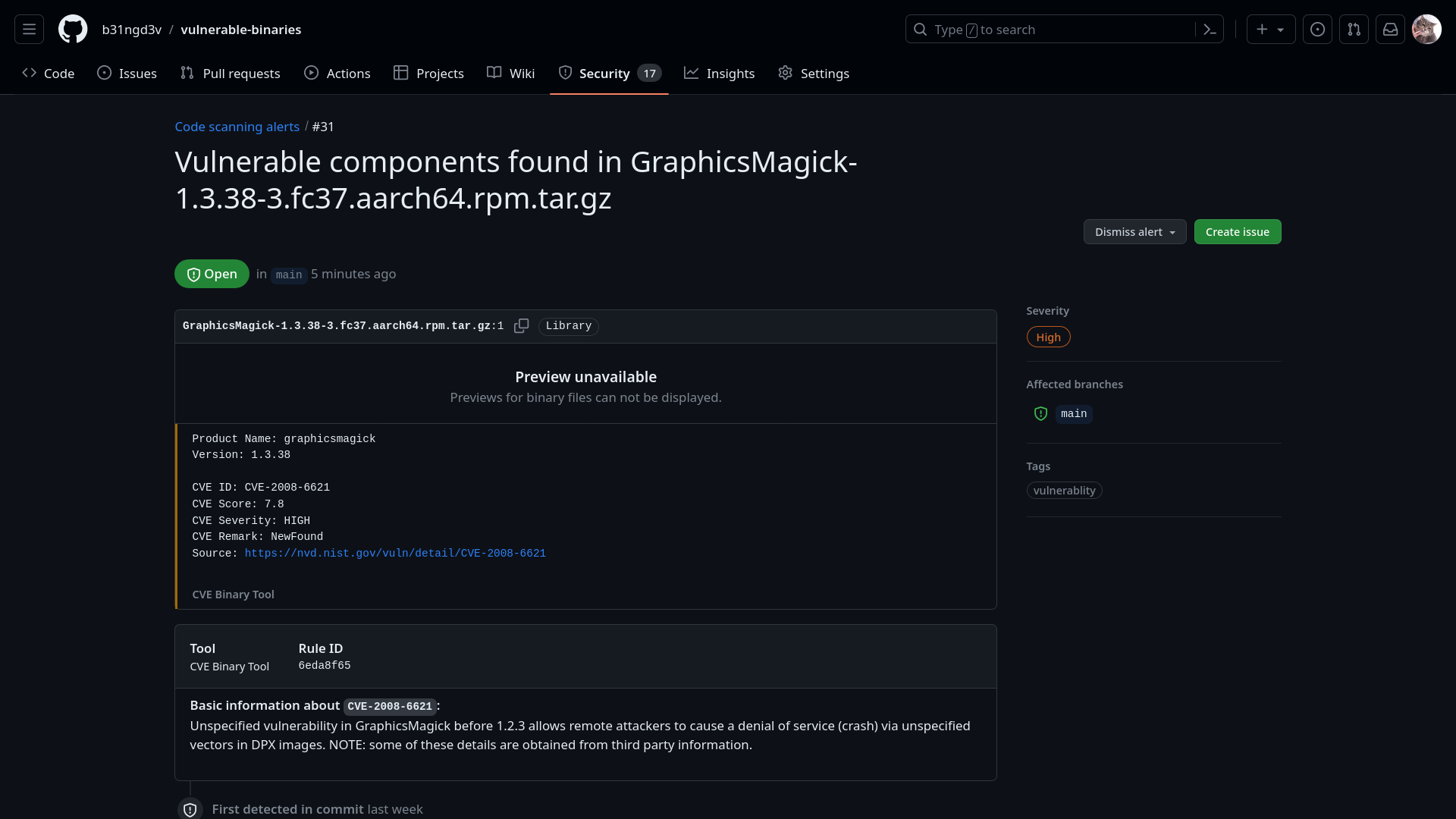
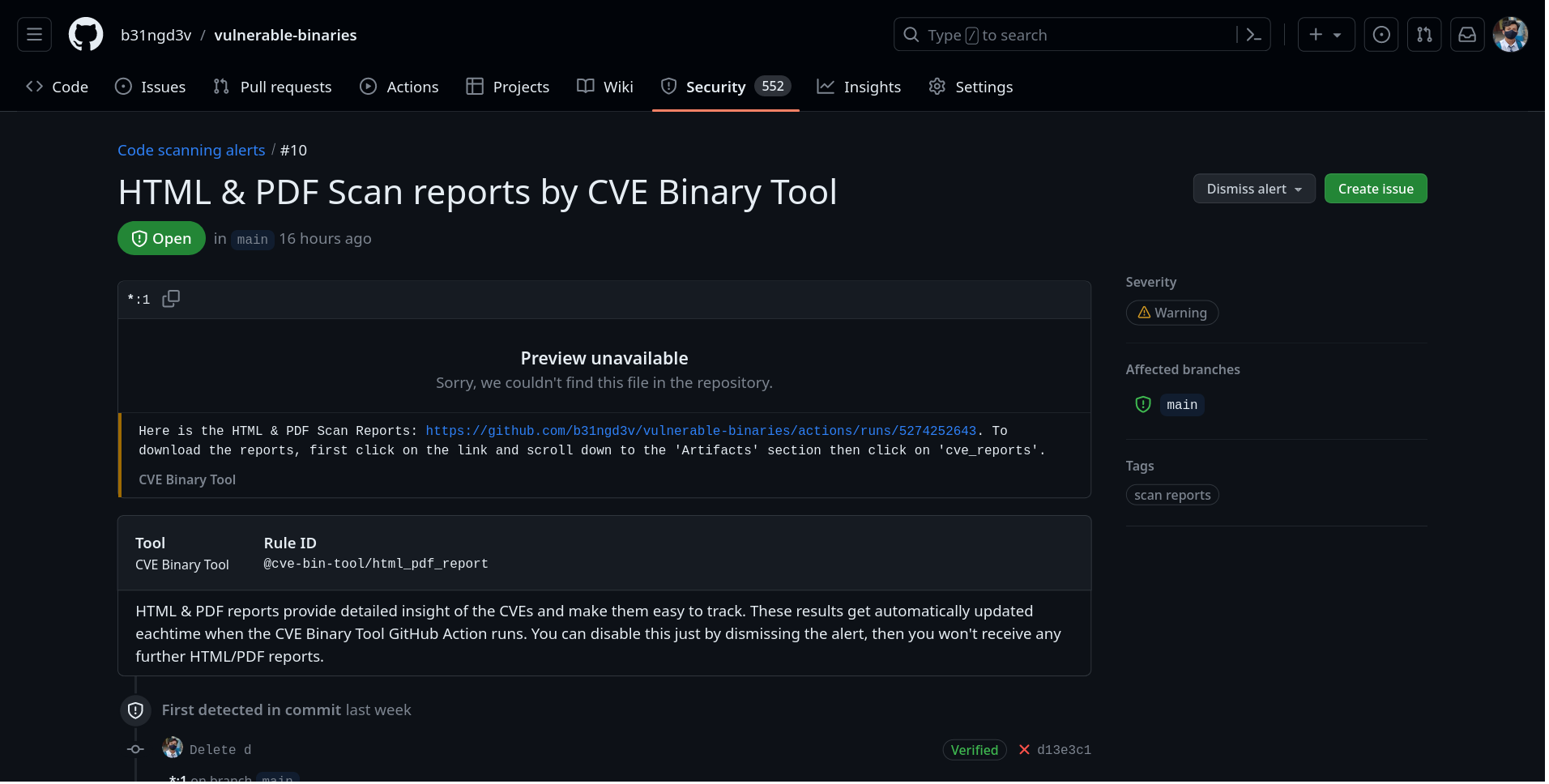
CVE Binary Tool GitHub Action helps you to scan your GitHub repositories more conveniently. Just add this Action by following the instructions below and It will start doing it's work and will give you updates through the security tab.
Optional CVE Binary Tool GitHub Action has three scan modes. The scan modes are listed below:
- repo-only (default): In this mode cve-bin-tool will automatically detect binary and requirement files and scan them.
- sbom-only: In this mode cve-bin-tool will only automatically detect supported SBOM files and scan them.
- both: In this mode cve-bin-tool will automatically detect SBOM, binary and requirement files and scan them.
NOTE: Scans may have duplicate results when using the both option as scan_mode.
Optional NVD API Key is required for downloading National Vulnerbility Database.
NOTE: CVE Binary Tool GitHub Action uses https://cveb.in as mirror to fetch the latest CVEs, and this mirror gets updated every day. So when you provide the nvd_api_key it uses the latest NVD data instead of one day old mirror data.
Optional While scanning, CVE Binary Tool will ignore these directories.
NOTE: To mention multiple directories, use comma as a separator and don't include spaces.
Optional Split security alerts based on source file. By default it creates separate security alerts for every component.
Optional It will run the build_command before running CVE Binary Tool on the build output and the repository content.
Optional CVE Binary Tool GitHub Action provides SBOM report in security tab along with HTML/PDF scan reports. Valid SBOM types are spdx, cyclonedx. (default: spdx)
Optional Valid SBOM formats are tag, json, yaml. (default: json)
Optional Provide input filename for triage data. The supported format is CycloneDX VEX, OpenVEX and CSAF. Find more information here.
Optional Provide a filter_triage flag in addition to triage_input_file that filters out vulnerabilities marked as 'not affected' and 'false positive' in the triage input file from the security tab.
name: CVE Binary Tool Scanner
on:
push:
pull_request:
workflow_dispatch:
schedule:
- cron: '20 2 * * *'
permissions:
contents: read
jobs:
scan:
runs-on: ubuntu-latest
permissions:
security-events: write
steps:
- uses: intel/cve-bin-tool-action@main
with:
nvd_api_key: '${{ secrets.NVD_API_KEY }}'
exclude_dir: testname: CVE Binary Tool Scanner
on:
push:
workflow_dispatch:
permissions:
contents: read
jobs:
scan:
runs-on: ubuntu-latest
permissions:
security-events: write
steps:
- uses: intel/cve-bin-tool-action@main
with:
nvd_api_key: '${{ secrets.NVD_API_KEY }}'
alerts_based_on_file: true
build_command: makename: CVE Binary Tool Scanner
on:
push:
workflow_dispatch:
permissions:
contents: read
jobs:
scan:
runs-on: ubuntu-latest
permissions:
security-events: write
steps:
- name: Setup node v16 (for build process)
run: |
curl -sL https://deb.nodesource.com/setup_16.x | sudo bash -
sudo apt -y install nodejs
- uses: intel/cve-bin-tool-action@main
with:
nvd_api_key: '${{ secrets.NVD_API_KEY }}'
build_command: npm run buildname: Update SBOM Action
on:
schedule:
- cron: '20 2 * * *'
permissions:
contents: read
jobs:
scan:
runs-on: ubuntu-latest
permissions:
security-events: write
contents: write
pull-requests: write
steps:
- uses: intel/cve-bin-tool-action@main
with:
nvd_api_key: '${{ secrets.NVD_API_KEY }}'
exclude_dir: binary
sbom_type: spdx
sbom_format: json
alerts_based_on_file: false
- run: |
mkdir -p reports
mv SBOM.spdx.json reports/SBOM.spdx.json # by default the SBOM file will be stored in the root directory of the repository, in this example the SBOM file is moved to reports directory in the repository
- name: Create Pull Request
uses: peter-evans/create-pull-request@v5
with:
commit-message: 'chore: update sbom'
title: 'chore: update sbom'
branch: chore-update-sbom
delete-branch: true
author: GitHub <[email protected]>