Note: This training is tailored to a specific audience.
- VPM creates primarily below Vault resources
- Ldap auth method
- Approle Auth method
- Ldap secrets engine
- Policies
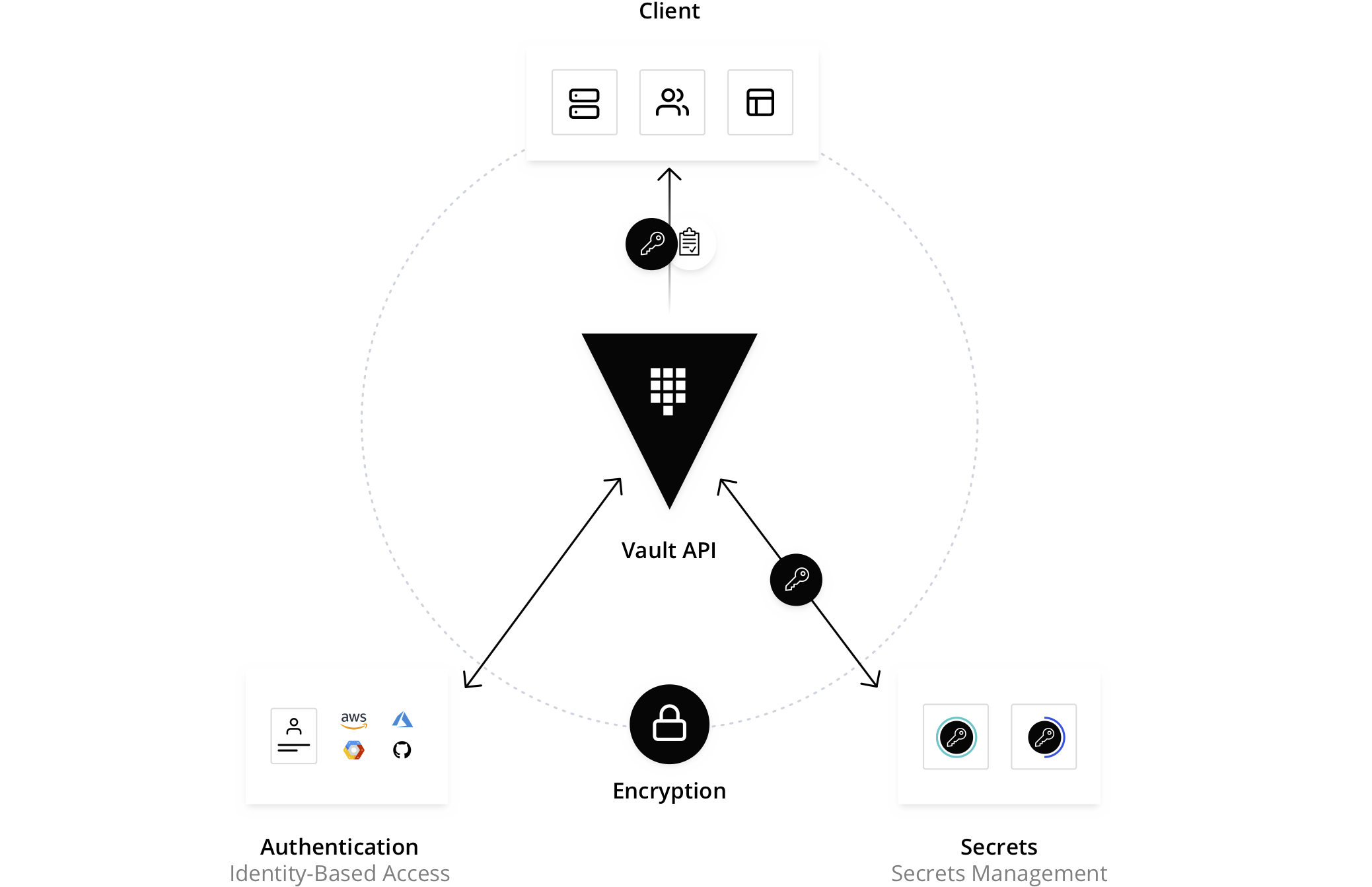
- Secrets management solution and much more - what is a secret?
- Provides Lifecycle Management for Secrets
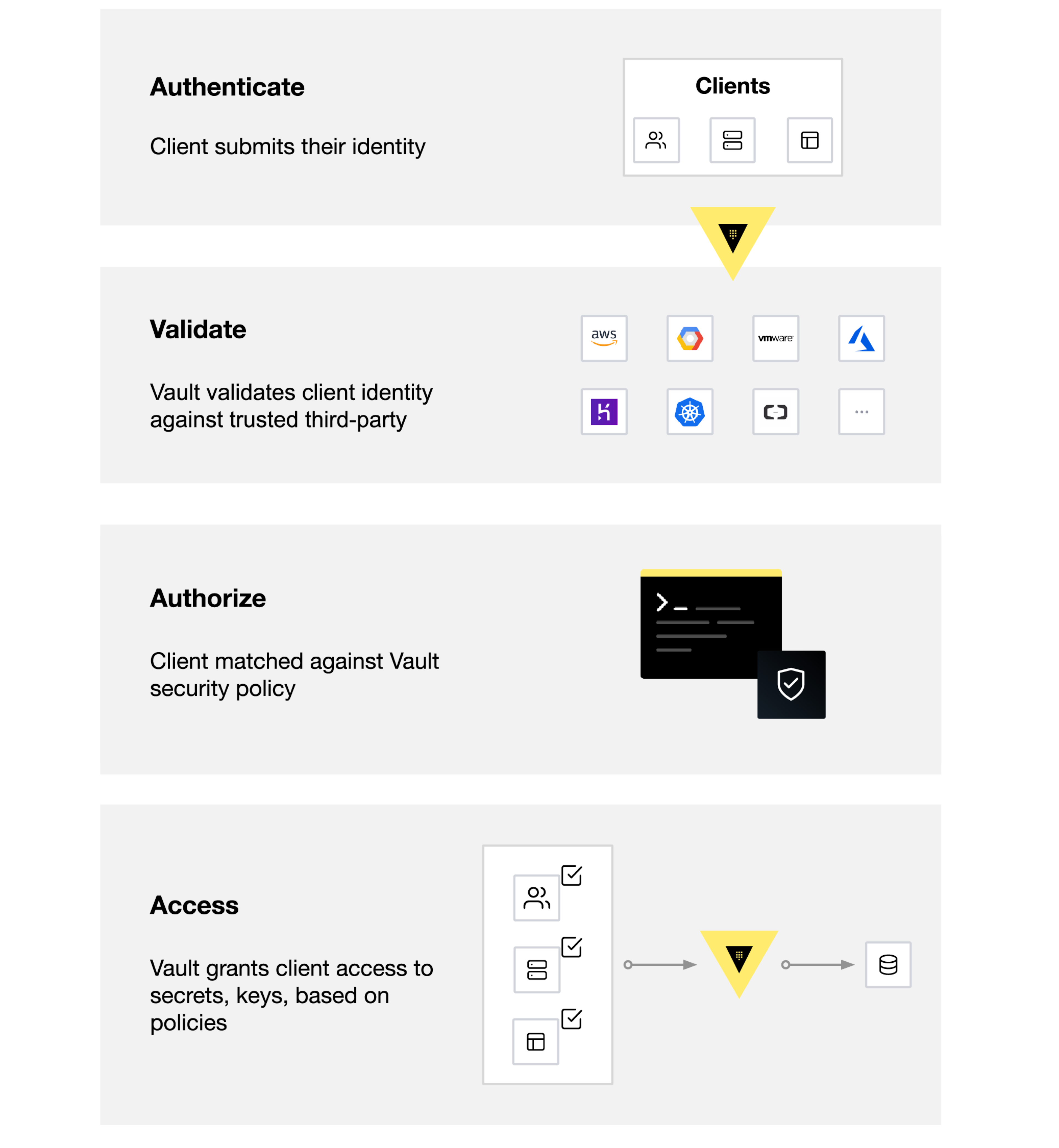
- Perform authentication and assign policy to the token
- Humans vs Machines Auth methods
- Token auth method is already enabled
- Types of auth method
- Approle
- LDAP
vault auth enable approle
vault write auth/approle/role/12345-application \
token_ttl=14400 token_max_ttl=14400 secret_id_ttl=15552000 \
role_id=ZS12345
vault write auth/approle/role/12345-automation \
token_ttl=14400 token_max_ttl=14400 secret_id_ttl=15552000 \
token_policies=12345-automation role_id=ZS56789
vault write auth/approle/role/12345-application \
token_ttl=14400 token_max_ttl=14400 secret_id_ttl=15552000 \
token_policies=12345-application role_id=ZS12345
- TTL default to 4 hours
- secret_id ttl default to 180 days
- Application, Automation, Manager (LDAP)
vault read auth/approle/role/12345-application/role-id
vault write -f auth/approle/role/12345-application/secret-id
vault write auth/approle/login role_id=ZS12345 secret_id=
vault auth enable ldap
vault write auth/ldap/config \
url="ldap://20.237.38.22" \
userdn="ou=users,dc=learn,dc=example" \
userattr="cn" \
groupdn="ou=groups,dc=learn,dc=example" \
groupattr="cn" \
insecure_tls=true \
starttls=false \
binddn="cn=admin,dc=learn,dc=example" \
bindpass=""
- TTL default to 4 hours
- secret_id ttl default to 180 days
- Humans (LDAP)
vault write auth/ldap/groups/aitmanager policies=aitmanager
vault write auth/ldap/groups/vaultadmin policies=vaultadmin
vault login -method=ldap username=alice
| User | Groups | Policies |
|---|---|---|
| Alice | aitmanager | aitmanager |
| Kalam | VaultAdmin | vaultadmin |
- Secrets engines are Vault components which store, generate or encrypt secrets
- Types of Engines - KV store, dynamic creds, Encryption as service
- Secret engines are plugins that need to be enabled, Community, Custom etc
- Types of secrets engines
- Ldap
- Databases
- KV engine
vault secrets enable -path=secrets/kv kv-v2
vault kv put -mount=secrets/kv/ ait-12345/db password=supersecret
vault kv put -mount=secrets/kv/ ait-56789/db password=supersecret
vault kv get -mount=secrets/kv/ ait-12345/db
vault kv get -mount=secrets/kv/ ait-56789/db
vault secrets enable ldap
vault write sys/policies/password/ldap policy=@password_policy.hcl
vault write ldap/config \
binddn=cn=admin,dc=learn,dc=example \
password_policy=ldap \
bindpass= \
url=ldap://4.157.222.221
vault write ldap/static-role/12345-serviceaccount1 \
dn='cn=serviceaccount1,ou=users,dc=learn,dc=example' \
username='serviceaccount1' \
rotation_period="600s"
vault write ldap/static-role/12345-serviceaccount2 \
dn='cn=serviceaccount2,ou=users,dc=learn,dc=example' \
username='alice2' \
rotation_period="600s"
vault read ldap/static-cred/12345-serviceaccount1
ldapsearch -b "cn=johnny,dc=learn,dc=example" \
-D 'cn=serviceaccount1,ou=users,dc=learn,dc=example' -h 4.157.222.221:389 \
-w
- Policies provide a declarative way to grant or forbid access to certain paths and operations in Vault
- Policies are deny by default, so an empty policy grants no permission in the system
vault policy write 12345-application 12345-application.hcl
vault server -dev