-
Notifications
You must be signed in to change notification settings - Fork 3
Let's Not Do That Again (so soon)
###Overview
In our last tutorial, we implemented a malware scan using the Microsoft Malicious Software removal tool. This scan can take a few minutes on older systems.
For users that run through your configuration process only once, this is ok, but users needing to restart the process may get frustrated by waiting for the malware scan to complete again and again.
One way to reduce this frustration is to perform the scan conditionally. If, for example, the scan completed 10 minutes ago without issue, we probably don't need to run it again so soon.
In this tutorial, we will configure the engine to skip the malware scan if it has been completed without issue in the last 24-hours.
Setup
This tutorial assumes that you have completed the tutorial, Scanning for malware, and have a version of the engine that will start and attempt to contact your web-server.
A note on examples
Our xml files are starting to get too long to include their full text inline in these tutorials. When you see this symbol  in the text, you can click on it to view the xml in question.
in the text, you can click on it to view the xml in question.
Saving a time stamp to the persisted settings store
In the tutorial Saving user settings, we used Settings.PersistSettingsString and Settings.RetrieveSettingsString tasks to save and retrieve the user's username across multiple engine sessions. We can employ a variant of the same technique -- this time using the Settings.PersistSettingsTimestamp task and Control.SecondsHaveElapsed conditions -- to have the engine remember when it last completed the malware scan successfully.
- In the file,
antimalware.xml, add the following xml block to the end of theantimalware.scantask branch:
<Settings.PersistSettingsTimestamp>
<Properties>
<SettingKey>Last malware scan</SettingKey>
</Properties>
</Settings.PersistSettingsTimestamp>This instructs the engine to persist a time stamp (the current date/time) to the persisted settings store using the key 'Last malware scan.' Here, it is important to place this task after the AntiMalware.ScanComputerForMalware task, as we don't want to persist a time stamp if AntiMalware.ScanComputerForMalware has not completed without issue.
Retrieving and evaluating a persisted time stamp
In the tutorial, Saving user settings, we used the task Settings.RetrieveSettingsString to retrieve strings saved to the persisted settings store. Things work a little differently for time stamps. Here, we need to use two conditions to retrieve their values, Control.SecondsHaveElapsed and its inverse, Control.SecondsHaveNotElapsed. Because persisted time stamps are only used conditionally, it saves us a step if we retrieve them and evaluate them in the appropriate conditions.
- Add this task branch xml to
antimalware.xml:
<TaskBranch name="antimalware.evaluate">
<Control.ReturnBranchResult>
<Conditions.Any>
<Control.SecondsHaveNotElapsed key="Last malware scan" value="86400"/>
</Conditions.Any>
<Properties>
<Branch>antimalware.skip</Branch>
</Properties>
</Control.ReturnBranchResult>
<Control.ReturnBranchResult>
<Conditions.Any>
<Control.SecondsHaveElapsed key="Last malware scan" value="86400"/>
</Conditions.Any>
<Properties>
<Branch>antimalware.scan</Branch>
</Properties>
</Control.ReturnBranchResult>
</TaskBranch>This branch determines whether or not we need to run the malware scan. To do this, it uses Control.SecondsHaveElapsed conditions to either run the branch antimalware.scan or the branch antimalware.skip depending on whether 24 hours (86400 seconds) have elapsed since the time stamp persisted under the key "Last malware scan."
- Add the following branch to
antimalware.xml:
<TaskBranch name="antimalware.skip">
<UserInterface.SetCheckedParagraphSubtitle>
<Properties>
<Dialog>Main dialog</Dialog>
<ControlKey>Scanning computer for malware</ControlKey>
</Properties>
<Content>
<SimpleParagraph margin="0,0,0,0" padding="0,0,0,0">
<Content>
<DirectTextContent>A malicious software scan has been recently completed on this computer.</DirectTextContent>
</Content>
</SimpleParagraph>
</Content>
</UserInterface.SetCheckedParagraphSubtitle>
</TaskBranch>
This branch informs the user that we are skipping the malware scan.
- Finally, we need to tell our main task branch to run
antimalware.evaluateinstead ofantimalware.scan. To do this, change theControl.ReturnBranchResultblock that we added totasklist.xmlin our last tutorial as follows:
<Control.ReturnBranchResult>
<Properties>
<Branch>antimalware.evaluate</Branch>
</Properties>
</Control.ReturnBranchResult>The first time you run the engine, it should run the malware scan as before:
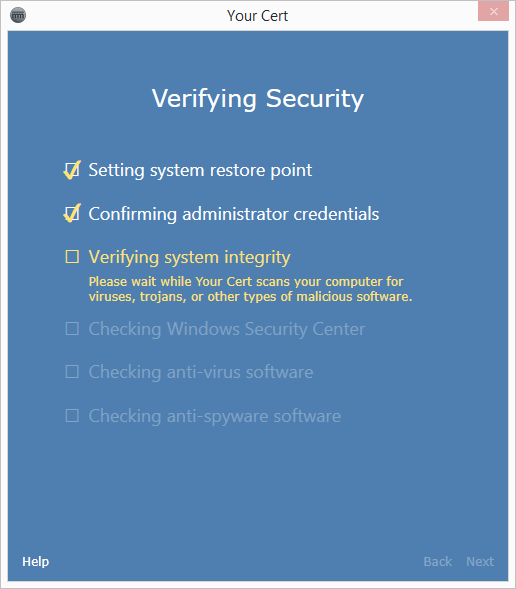
But when you run the engine again, it should skip the malware scan:
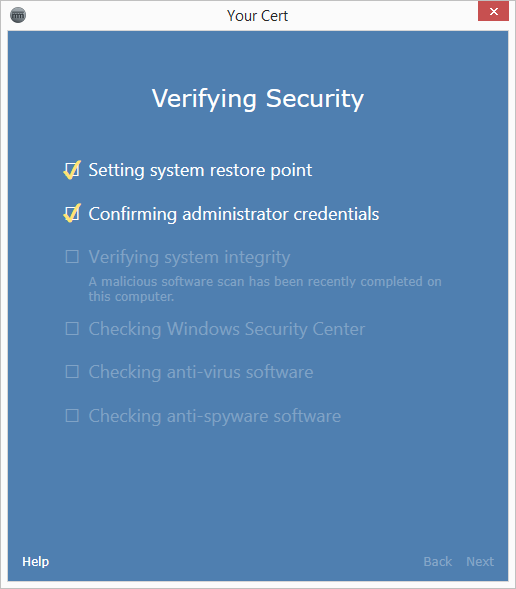
Note: things might go by too fast for you to see the disabled text at this point. You can modify the antimalware.skip branch as follows to allow more time to show the disabled text:
<TaskBranch name="antimalware.skip">
<UserInterface.SetCheckedParagraphSubtitle minimumTaskTime="3">
<Properties>
<Dialog>Main dialog</Dialog>
<ControlKey>Scanning computer for malware</ControlKey>
</Properties>
<Content>
<SimpleParagraph margin="0,0,0,0" padding="0,0,0,0">
<Content>
<DirectTextContent>A malicious software scan has been recently completed on this computer.</DirectTextContent>
</Content>
</SimpleParagraph>
</Content>
</UserInterface.SetCheckedParagraphSubtitle>
</TaskBranch>
Conclusion
In this tutorial, we used the Settings.PersistSettingsTimestamp task and Control.SecondsHaveElapsed conditions to ignore the anti-malware scan if it was completed without issue within 24 hours. In the next tutorial, we will verify that users' computers have working security software installed.